Microsoft has issued a clear warning: the era of running outdated, unpatched on-premises Exchange Servers and expecting seamless communication with Exchange Online is coming to an end. In a recent announcement, Microsoft declared its intent to actively protect Exchange Online by implementing measures to first throttle, and then outright block, inbound email messages originating from on-premises Exchange servers that are not kept up to date. This decisive action underscores the critical need to Upgrade Outdated Exchange Server infrastructure to maintain uninterrupted email flow and robust security.
The catalyst for this firm stance is rooted in the persistent vulnerabilities exploited over the past few years, most notably the widespread Hafnium attacks of March 2021. Despite the significant disruption caused by these exploits, a concerning number of on-premises Exchange servers remain unpatched and dangerously exposed to known threats. While efforts like the FBI’s intervention to patch US-based servers provided temporary relief, countless vulnerable servers worldwide continue to be prime targets for malicious actors.
The exact number of outdated Exchange servers in operation remains somewhat opaque to Microsoft. Their visibility is limited to servers within hybrid Exchange environments and those discernible through inbound SMTP traffic analysis. However, the undeniable reality is that a significant portion of on-premises deployments are running obsolete and vulnerable versions of Microsoft Exchange Server. This alarming landscape includes Exchange 2007, Exchange 2010, and Exchange 2013, with the latter having reached its end-of-support date in April 2023. Even Exchange 2016 and Exchange 2019 installations are at risk of falling into the “outdated” category if they are not consistently updated with the latest security and cumulative updates.
The Growing Threat Landscape for Unpatched Exchange Servers
The vulnerability of these older Exchange Server versions stems from their architecture, designed in a time when the current sophisticated threat landscape was barely conceived. These legacy systems are now inherently susceptible to a vast and ever-expanding arsenal of attack techniques, readily available to everyone from novice hackers to state-sponsored cybercriminals. This makes running outdated Exchange servers an increasingly risky proposition.
Even organizations with considerable experience in managing on-premises infrastructure struggle to maintain the necessary update cadence. The complexity of patching and the potential for disruptions can lead to update neglect, inadvertently leaving systems exposed. The stark reality is that Exchange 2007, Exchange 2010, and Exchange 2013 are no longer supported and thus receive no security patches or cumulative updates. With each passing month, their vulnerability to compromise escalates, transforming them into attractive targets for cyberattacks, as highlighted by the zero-day vulnerabilities discovered in September 2022.
For many organizations still operating on-premises Exchange, migrating to Exchange Online and Microsoft 365 is the most secure and sustainable long-term strategy. However, for those with compelling business or regulatory reasons to maintain on-premises infrastructure, Microsoft’s message is unequivocal: continued communication with Exchange Online necessitates running a supported version of Exchange Server and adhering to a rigorous update regime, applying both security and cumulative updates promptly. “Current” in this context signifies running the latest available updates or, at the very least, the immediately preceding ones.
Microsoft’s Enforcement Strategy: Report, Throttle, and Block
To underscore the urgency of upgrading and to incentivize organizations to modernize their Exchange infrastructure, Microsoft is implementing a phased enforcement strategy within the Exchange Online transport service. This involves inspecting SMTP headers of inbound messages arriving through inbound connectors configured with the ConnectorType set to OnPremises. This specifically targets hybrid organizations routing email to Exchange Online via these connectors.
When a message originates from an Exchange Server, Exchange Online’s transport service analyzes the version number embedded in the message header to identify the sending server’s version. A typical header might reveal information like this:
Received: from <domain>.com (xx.xx.x.xx) by HOST.mail.protection.outlook.com (xx.xxx.xxx.xx) with Microsoft SMTP Server (TLS) id 14.3.496.0 via Frontend Transport; Mon, 27 Mar 2023 13:20:21 +0000This header, entirely standard in SMTP communication, reveals that the sending server is running Exchange 2010 SP3 with Rollup Update 30 (version 14.3.496.0), a version released in February 2020 and unsupported since March 2021. Notably, Exchange 2013 also reached its end-of-support milestone in April 2023.
Armed with this version intelligence, Exchange Online can then decide whether to accept, throttle, or reject the incoming message. Acknowledging the installed base of older Exchange servers, Microsoft is adopting a graduated approach, moving from reporting to throttling and ultimately to blocking.
The Phased Rollout: Reporting, Throttling, and Blocking Timeline
Microsoft’s enforcement strategy unfolds in distinct phases: reporting, throttling, and blocking, each designed to progressively encourage upgrades.
The reporting phase commenced in April, with Microsoft releasing reports to identify organizations utilizing affected servers. For Exchange 2007 users, the generally available version of this report became accessible in May.
Throttling for Exchange 2007 servers began on June 26th, ninety days after the initial announcement. This throttling mechanism, applied to messages sent via OnPremises inbound connectors, introduces delays in message processing. Traffic from obsolete servers arriving through other routes remains, for the time being, unaffected.
The throttling implementation in Exchange Online works by temporarily delaying the acceptance of inbound messages, effectively creating backpressure on the sending servers. This is perceived as temporary unavailability by the sending server. Initially, throttling starts at five minutes per hour, gradually escalating over 30 days to 20 minutes per hour. If no upgrade action is taken, throttling will transition into blocking. Figure 1 illustrates this three-stage enforcement process, with each phase spanning approximately 30 days for reporting, throttling, and blocking respectively. Blocking of inbound traffic from obsolete Exchange 2007 servers commenced on July 26, 2023.
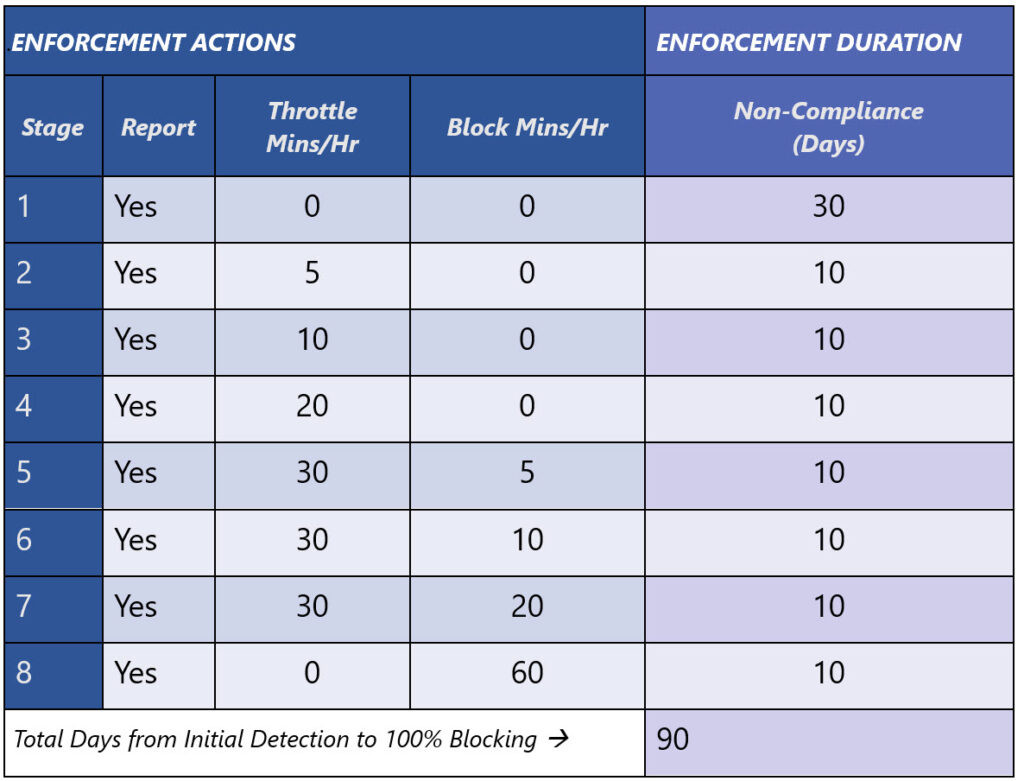 The stages of enforcement by Exchange Online (source: Microsoft) Microsoft Exchange Server
The stages of enforcement by Exchange Online (source: Microsoft) Microsoft Exchange Server
Figure 1: Microsoft’s enforcement stages for outdated Exchange Servers communicating with Exchange Online.
During throttling, Exchange Online issues temporary SMTP errors, causing messages to queue on the source servers, mimicking temporary service disruptions. As throttling durations increase, users will experience noticeable email delays, and administrators should observe message queue growth. However, the concern remains that some neglected servers might not be actively monitored, potentially delaying the recognition of the issue.
Navigating the Throttling and Blocking Cycle
Prior to the commencement of throttling, Microsoft initiates a notification process via the Microsoft 365 message center. These notifications are crucial for alerting administrators in hybrid organizations about the presence of outdated servers within their environment.
The notification cycle broadly follows these steps:
- Ongoing Detection: Microsoft continuously analyzes message traffic to identify outdated Exchange Servers.
- Reporting in Exchange Admin Center: Detected outdated servers are added to a new mail flow report within the Exchange Admin Center (EAC). This report provides details on throttling and blocking actions and outlines the necessary steps for remediation.
- Message Center Notifications: For organizations with Exchange 2007 servers sending email to Exchange Online via OnPremises connectors, Microsoft sends message center notifications announcing the impending throttling, scheduled to begin in 60 days.
- Progressive Throttling: Throttling commences and escalates over 30 days, increasing in duration every 10 days.
- Transition to Blocking: Following 30 days of throttling, blocking is initiated and progressively intensifies over the subsequent 10 days, while throttling is commensurately reduced, culminating in complete blockage of traffic from the outdated server.
While notification specifics may evolve, the core message remains constant: administrators must take immediate action. This necessitates proactive monitoring of message center notifications, identifying outdated servers (tools like the Health Checker script can assist), understanding their role within the organization, and planning for upgrades, which may include hardware upgrades. Prompt response to these notifications is paramount.
If throttling warnings are ignored, Microsoft escalates enforcement to message rejection. Exchange Online will permanently block inbound messages, and senders will receive Non-Delivery Reports (NDRs) with a 5.7.230 error code, signaling email delivery failure. This should serve as a clear indicator to senders and their administrators to investigate and rectify the underlying issue. The NDRs and associated error messages in message tracking logs should prompt administrators to address the outdated server problem.
Upgrade or Lose Email Connectivity to Exchange Online
The ultimate choice facing organizations operating outdated Exchange servers is stark: upgrade to a supported version or forfeit the ability to send emails to Exchange Online. Considering the vast volume of email traffic processed by Exchange Online, choosing inaction is akin to severely hindering business communication.
While Microsoft is initially targeting Exchange 2007 servers communicating with Exchange Online, similar enforcement measures are anticipated for Exchange 2010 and Exchange 2013 servers in the near future. The same pattern of reporting, throttling, and rejection is expected to be applied to incentivize upgrades to supported versions, and to encourage consistent patching of even Exchange 2016 and Exchange 2019 servers. Microsoft’s actions serve as a clear signal to prioritize security and apply timely updates to all Exchange Server deployments.
Microsoft’s objective is unambiguous: to compel organizations running on-premises Exchange servers to adopt and maintain secure, supported software. Those who heed this guidance will maintain seamless interoperability with Exchange Online. Those who disregard it will face communication disruptions. The message is clear and the path forward is defined.
This approach may also extend to other vulnerable server types if they are identified as vectors for malware injection into Exchange Online. For example, outdated Postfix servers on Linux, if exploited, could also become targets for similar blocking measures to safeguard Exchange Online’s integrity.
Planning Your Microsoft Platform Migration and Consolidation
The 90-Day Enforcement Pause: A Temporary Exemption
Recognizing the complexities of real-world IT environments, Microsoft acknowledges that some hybrid Exchange deployments may include older Exchange servers performing specific functions, such as sending marketing communications. Applying throttling or blocking to these servers could disrupt legitimate business operations.
While the ultimate goal remains server upgrades, Microsoft offers a 90-day “enforcement pause” per calendar year. This provision acknowledges that organizations may have periods where upgrades are infeasible or require extended timelines for remediation. Customers can request this pause via the mail flow report in the EAC, allowing for a single 90-day block or multiple shorter blocks totaling 90 days within the year.
Upon expiry of the pause period, enforcement resumes at the pre-pause level if the outdated servers remain in operation.
The Imperative of Upgrading Your Exchange Server
While some may perceive Microsoft’s actions as heavy-handed, they are ultimately necessary to protect a global email service relied upon by millions. Regardless of perspective, organizations utilizing Exchange Online with outdated on-premises Exchange servers have a clear mandate: upgrade those servers or risk losing email communication with Exchange Online. And while addressing server updates, it’s also crucial to ensure Outlook clients are up to date to mitigate other vulnerabilities. The time to upgrade your outdated exchange server is now.
