In today’s data-driven world, the importance of data in decision-making is paramount. Managing this ever-growing data necessitates robust database management systems, and MS SQL Server stands out as a leading choice. Mastering MS SQL Server opens up exciting career paths as an SQL Specialist and SQL Developer. To confidently navigate your SQL server interview, thorough preparation with common interview questions is key. This article delves into frequently asked MS Sql Server Interview Questions to set you on the path to success. Let’s explore!
Top SQL Server Interview Questions for 2025
Let’s begin with these carefully selected SQL server interview questions, designed to help you excel in your upcoming interview:
1. What is Windows Authentication Mode in SQL Server?
Windows Authentication Mode leverages Windows accounts to authenticate server connections. In this mode, the SQL server relies on the username and password of the Windows account attempting to connect, effectively disabling SQL server authentication.
2. Can you provide an example of an SQL server function that returns the first non-null expression from multiple columns?
SELECT COALESCE(sid, sname, marks) from the student;The COALESCE function elegantly handles null values by returning the first non-null expression it encounters in the provided list of arguments.
3. Explain the concept of a one-to-many relationship in SQL Server databases.
A one-to-many relationship arises when a single value in a column of one table is associated with one or more values in a column of another table. For example, one department can have many employees.
4. What is the significance of the CHECK constraint in SQL Server?
The CHECK constraint is crucial for enforcing data integrity by limiting the permissible values within a table column. It acts as a rule, ensuring that all values inserted into the column adhere to a specific condition. This constraint is defined at the column level to impose specific value restrictions.
Example:
CONSTRAINT CHK_StudentAge CHECK (age >= 18)This CHECK constraint ensures that the ‘age’ column in the ‘Student’ table only accepts values greater than or equal to 18.
Basics to Advanced – Learn It All!
Full Stack Java Developer Masters ProgramExplore Program
5. How would you retrieve the 3rd highest marks from a ‘Student’ table?
SELECT TOP 1 marks
FROM (SELECT DISTINCT TOP 3 marks
FROM student
ORDER BY marks DESC) a
ORDER BY marks ASC;This query efficiently finds the third highest mark. The inner query selects the top 3 distinct marks in descending order, and the outer query then picks the top 1 from these 3 in ascending order, effectively giving the 3rd highest.
6. What is a trigger in SQL Server?
Triggers are powerful tools in SQL Server that automatically execute a batch of SQL code in response to specific table events, such as INSERT, DELETE, or UPDATE operations. Managed by the Database Management System (DBMS), triggers can also invoke stored procedures. For instance, you can set up a trigger to be activated whenever a new record is inserted into a database table, perhaps to log the event or perform related actions.
7. Under what conditions can records be deleted from a view in SQL Server?
Records can be deleted from a ‘simple’ view, which is defined as a view that retrieves data from only one base table. If a view is based on multiple tables or uses aggregations, direct deletion is generally not allowed to maintain data integrity and view consistency.
8. Outline some key features of MS SQL Server.
MS SQL Server boasts a range of features, including:
- Easy and Straightforward Syntax: SQL Server employs a user-friendly and intuitive syntax, making it easier to write and understand queries.
- Transact-SQL (T-SQL): SQL Server utilizes Transact-SQL, an extension of standard SQL, providing enhanced programming capabilities and control.
- Query Optimization: SQL Server includes a robust query optimizer that automatically improves query execution plans for better performance. (Note: The original article incorrectly states “Query optimization is not supported.”)
- Transaction Rollbacks: SQL Server transactions fully support rollbacks, allowing you to undo changes and maintain data consistency in case of errors. (Note: The original article incorrectly states “The transaction process does not allow rollbacks”)
- Clustering Support: SQL Server supports clustering, enabling high availability and scalability by distributing workload across multiple servers. (Note: The original article incorrectly states “Clustering is not supported”)
- Concurrent Statement Execution: SQL Server supports concurrent execution of statements, improving overall database performance and responsiveness. (Note: The original article incorrectly states “Statements are executed serially.”)
9. Which command retrieves the SQL Server version?
To determine the SQL Server version, execute the following query:
SELECT SERVERPROPERTY('productversion')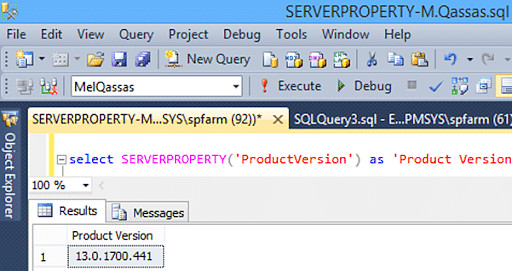 SQL_QandA
SQL_QandA
alt text: SQL Q&A icon representing frequently asked questions and answers for SQL Server interviews.
10. What is a user-defined function in SQL Server?
User-defined functions (UDFs) empower users to encapsulate custom logic within SQL Server. They allow you to create reusable functions tailored to specific needs, extending the built-in functionalities. Unlike predefined functions, UDFs provide flexibility for implementing complex SQL code. They can return either a table or a scalar value.
Example:
CREATE FUNCTION sample(@sid INT)
RETURNS TABLE
AS
RETURN
SELECT *
FROM student
WHERE Id = @sid;This UDF, named sample, takes a student ID (@sid) as input and returns a table containing the details of the student with that ID.
11. Explain the different types of replication in SQL Server.
SQL Server offers three primary types of replication for data distribution and synchronization:
- Transactional Replication: This method focuses on near real-time data distribution from a publisher to subscribers. It’s ideal for scenarios with frequent data changes, ensuring subscribers receive updates with low latency.
- Merge Replication: Merge replication enables data synchronization between multiple sources and a central database. It is particularly useful when both central and branch databases need to update information independently and then consolidate changes, often used in mobile or distributed environments.
- Snapshot Replication: Snapshot replication is the simplest form, periodically taking a “snapshot” of the data at a specific point in time and applying it to subscribers. It is best suited for data that changes infrequently, such as lookup tables or reference data, and is easy to maintain. For example, it’s well-suited for distributing daily updated product lists from a main server to branch servers.
12. Define referential integrity.
Referential integrity is a fundamental concept in relational databases. It ensures that relationships between tables remain consistent. Specifically, it mandates that every foreign key value in a child table must have a corresponding matching primary key value in the parent table. This constraint prevents orphaned records and maintains data accuracy across related tables.
13. What are TCL Commands? List the TCL Commands available in SQL Server.
TCL, or Transaction Control Language, commands are used to manage transactions within a database. They provide control over the execution and outcome of database transactions. The three core TCL commands in SQL Server are:
- ROLLBACK: The
ROLLBACKcommand undoes all changes made within the current transaction and reverts the database to its state at the beginning of the transaction or the last savepoint. - SAVE TRANSACTION (SAVE TRAN):
SAVE TRANestablishes a savepoint within a transaction. This allows you to selectively rollback to a specific point within a transaction without undoing the entire transaction. - COMMIT: The
COMMITcommand permanently saves all changes made within the current transaction to the database, making them durable and visible to other users.
14. Write an SQL Server query to find the position of the letter ‘e’ in the name ‘Jenna’ from the ‘student’ table.
SELECT CHARINDEX('e', NAME, 1)
FROM student
WHERE name = 'Jenna';The CHARINDEX function is used to locate the starting position of a substring within a string. In this query, it finds the position of the first occurrence of ‘e’ in the ‘NAME’ column for the student named ‘Jenna’. We use 1 as the starting position for the search.
15. As an SQL developer, how would you ensure optimal performance for SQL server-based applications and databases?
Ensuring optimal performance involves a multifaceted approach:
- Data Volume and Type Analysis: Understanding the volume of data, the types of information stored, and data access patterns is crucial. Analyze the data to identify potential bottlenecks and areas for optimization.
- System Upgrade Considerations: When upgrading systems, analyze existing data, data access methods, and query performance to identify potential issues in the new environment.
- Data Awareness: Maintaining a deep understanding of the data itself, its structure, and usage is essential for effective database design and performance tuning.
- Query Optimization: Regularly review and optimize SQL queries, focusing on efficient indexing, appropriate join types, and minimizing resource consumption. Use SQL Server Profiler and Database Engine Tuning Advisor to identify slow-running queries and get optimization recommendations.
- Index Management: Implement appropriate indexes to speed up data retrieval. Regularly review and maintain indexes, removing unused or redundant indexes.
- Database Design: Design databases with normalization principles in mind to reduce data redundancy and improve data integrity.
- Hardware Considerations: Ensure adequate hardware resources, including sufficient memory, CPU, and disk I/O, to support database workload.
- Regular Maintenance: Implement regular database maintenance tasks, such as index defragmentation, statistics updates, and database backups.
Basics to Advanced – Learn It All!
Full Stack Java Developer Masters ProgramExplore Program
16. When are server-based cursors appropriate to use?
Server-based cursors are useful when you need to process data row by row, performing operations on individual records rather than working with the entire dataset at once. This is beneficial in scenarios where:
- Record-by-record processing is required: When business logic necessitates individual processing of each row returned by a query.
- Large datasets need to be processed incrementally: Cursors can help manage memory usage when dealing with very large result sets that might not fit into memory.
However, cursors can be less performant than set-based operations, especially with large data volumes. Therefore, consider alternative set-based solutions whenever possible and use cursors judiciously.
17. Explain the functionality of the FLOOR function.
The FLOOR function in SQL Server rounds a given non-integer numeric value down to the nearest preceding integer. For example, FLOOR(5.6) returns 5, and FLOOR(-5.6) returns -6.
18. What are scheduled tasks (SQL Server Agent Jobs) in SQL Server?
Scheduled tasks, also known as SQL Server Agent Jobs, are automated processes that execute predefined SQL Server operations at specified times or intervals. They enable you to automate routine database administration tasks, data processing jobs, and other scheduled activities. By scheduling tasks, you minimize manual intervention, ensure timely execution of jobs, and improve operational efficiency.
19. Provide a query to list all triggers in a database.
SELECT *
FROM sys.objects
WHERE type = 'TR';This query retrieves information about all database objects of type ‘TR’, which represents triggers, from the sys.objects system view.
20. Differentiate between ROLLBACK and COMMIT commands.
- COMMIT: The
COMMITcommand finalizes a transaction, making all changes made within the transaction permanent in the database. Once committed, the changes are saved and become visible to other users and sessions. - ROLLBACK: The
ROLLBACKcommand cancels a transaction, discarding all changes made within it. It reverts the database to its state before the transaction began or to the last savepoint, effectively undoing any modifications made during the transaction.
21. Explain how to create a table in SQL Server.
The basic syntax for creating a table in SQL Server is:
CREATE TABLE table_name (
column1 datatype,
column2 datatype,
...
);For example, to create a ‘Student’ table:
CREATE TABLE Student (
Name VARCHAR(20),
DOB DATE,
Marks NVARCHAR(5),
Subject VARCHAR(20)
);This statement creates a table named ‘Student’ with columns for ‘Name’ (text up to 20 characters), ‘DOB’ (Date of Birth), ‘Marks’ (text up to 5 characters, allowing for potential non-numeric marks), and ‘Subject’ (text up to 20 characters).
22. What is the function of a foreign key in a database?
A foreign key establishes and enforces a link between two tables, typically referred to as the parent table and the child table. It acts as a constraint to maintain referential integrity. The foreign key in the child table references the primary key in the parent table. It ensures that values in the foreign key column of the child table must match existing values in the primary key column of the parent table. A table can have multiple foreign keys, each referencing different parent tables or columns.
Example:
Consider two tables: ‘student’ and ‘teacher’.
student (StudentID, Name, Age, Contact, Gender, Address)
teacher (TeacherID, Name, StudentID)Here, StudentID in the ‘teacher’ table is a foreign key referencing StudentID (primary key) in the ‘student’ table. This ensures that every teacher is associated with a valid student.
23. What is the importance of views in a database?
Views offer several advantages and are valuable tools in database management:
- Data Aggregation and Performance: Views can pre-aggregate data, simplifying complex queries and improving performance by reducing the need for repeated aggregations.
- Schema and Data Customization: Views allow you to present a customized view of the database schema and data to specific users or applications, hiding complexity or sensitive information.
- Access Control: Views provide a mechanism for controlling access to specific columns and rows of data. You can grant users access to a view without granting direct access to the underlying base tables, enhancing data security.
Prepare Yourself to Answer All Questions!
Automation Testing Masters ProgramExplore Program
 Prepare Yourself to Answer All Questions!
Prepare Yourself to Answer All Questions!
alt text: Banner ad promoting an Automation Testing Masters Program, suggesting further career development after mastering SQL Server.
24. Describe the steps to hide SQL Server Instances.
Hiding SQL Server instances enhances security by making them less discoverable on the network. To hide an instance, follow these steps using SQL Server Configuration Manager:
- Open SQL Server Configuration Manager: Search for “SQL Server Configuration Manager” in the Windows Start Menu.
- Navigate to SQL Server Network Configuration: In the left pane, expand “SQL Server Network Configuration” and select “Protocols for [Your Instance Name]”.
- Access Instance Properties: Right-click on “TCP/IP” in the right pane and select “Properties”.
- Hide Instance Setting: In the “TCP/IP Properties” dialog box, go to the “Flags” tab. Set “Hide Instance” to “Yes”.
- Apply Changes: Click “Apply” to save the changes and then “OK” to close the dialog.
- Restart SQL Server Instance: Restart the SQL Server instance for the changes to take effect.
After these steps, the SQL Server instance will not be listed when clients browse for available SQL Server instances on the network. They will need to know the specific server name and instance name to connect.
25. Explain the DBCC command and its uses.
DBCC (Database Consistency Checker) commands are a suite of powerful utilities in SQL Server used to perform various maintenance, validation, and diagnostic tasks on databases, tables, indexes, and other database objects. DBCC commands are essential for database administration and troubleshooting. Examples of common DBCC commands and their uses include:
- DBCC CHECKALLOC: Verifies the allocation and structural integrity of all pages in a database, ensuring that pages are correctly allocated and linked.
- DBCC CHECKDB: Performs a comprehensive check of database integrity, including checking physical and logical consistency of database objects, indexes, and data. It ensures that indexes are correctly linked to tables and that data pages are not corrupted.
- DBCC CHECKFILEGROUP: Validates the integrity of all file groups within a database, checking for any damage or corruption in the file groups.
26. Describe the SIGN function.
The SIGN function determines the sign of a numeric input. It returns:
- 1: if the number is positive (greater than 0).
- -1: if the number is negative (less than 0).
- 0: if the number is zero (equal to 0).
Syntax:
SIGN(number)27. Define alternate key.
An alternate key is a candidate key that is not chosen as the primary key for a table. When a table has multiple candidate keys (columns or sets of columns that uniquely identify each row), one is designated as the primary key, and the remaining candidate keys are termed alternate keys. Like primary keys, alternate keys also enforce uniqueness for the identified columns.
28. Define JOIN. What are the different types of JOINs in SQL Server?
A JOIN clause in SQL combines rows from two or more tables based on a related column between them. Joins are fundamental for querying relational databases to retrieve data from multiple related tables. SQL Server supports several types of JOINs:
- INNER JOIN: Returns rows only when there is a match in both tables based on the join condition. Rows with no match in either table are excluded.
- OUTER JOINs: Return all rows from one table (left, right, or both) and matching rows from the other table. If there’s no match, NULL values are returned for columns of the non-matching table.
- LEFT OUTER JOIN (LEFT JOIN): Returns all rows from the left table and matching rows from the right table.
- RIGHT OUTER JOIN (RIGHT JOIN): Returns all rows from the right table and matching rows from the left table.
- FULL OUTER JOIN (FULL JOIN): Returns all rows from both tables. If there are no matches, NULL values are used for columns of the table without a match.
- CROSS JOIN: Produces a Cartesian product of the rows from the joined tables. It returns every possible combination of rows from all tables involved, without requiring a join condition.
29. Explain the use of UPDATE STATISTICS.
UPDATE STATISTICS is a crucial command for maintaining query performance in SQL Server. It updates the query optimizer’s statistics about the distribution of key values within indexes and table columns. These statistics are used by the query optimizer to create efficient query execution plans. Outdated statistics can lead to suboptimal query plans and slow performance. Regularly updating statistics, especially after significant data modifications, ensures that the query optimizer has accurate information for plan generation.
30. Define Full Backup in SQL Server.
A full backup is the most comprehensive type of backup in SQL Server. It creates a complete copy of the entire database, including all data files, database objects (tables, indexes, stored procedures, etc.), and a portion of the transaction log to allow for database recovery. Full backups are the foundation for other backup strategies and are essential for point-in-time recovery.
31. What is an identity column in SQL Server?
An identity column in SQL Server automatically generates sequential numeric values when new rows are inserted into a table. It simplifies the process of creating unique identifiers for records. You define the starting value (seed) and the increment value for the identity column. Identity columns are typically used as primary keys, although they don’t inherently enforce primary key constraints. They ensure automatic, unique value generation without manual intervention.
32. Explain the UNIQUE KEY constraint.
The UNIQUE KEY constraint enforces uniqueness for the values in a specified column or a set of columns within a table. It ensures that no duplicate values are allowed in the constrained columns, maintaining data integrity and preventing redundancy. Unlike primary keys, a table can have multiple UNIQUE KEY constraints, and UNIQUE KEY columns can allow NULL values (unless explicitly disallowed). UNIQUE KEY constraints enforce entity integrity by ensuring that each entity in the table is uniquely identifiable based on the constrained columns.
33. Define the process of denormalization.
Denormalization is a database optimization technique where redundant data is intentionally added to a database schema that was previously in a normalized form. The primary goal of denormalization is to improve query performance by reducing the need for complex joins across multiple tables. While normalization aims to minimize data redundancy and improve data integrity, denormalization prioritizes faster data retrieval, often at the cost of increased data redundancy and potential data inconsistencies if not managed carefully. Denormalization is typically considered after normalization and is applied strategically to address specific performance bottlenecks.
34. Show how to apply a table type constraint to a table.
Table type constraints are not directly applied using ALTER TABLE ... ALTER CONSTRAINT. The syntax provided in the original article is incorrect. Table-level constraints, like CHECK or UNIQUE constraints that apply to multiple columns, are typically defined during table creation using CREATE TABLE or added later using ALTER TABLE ... ADD CONSTRAINT.
Example of adding a table-level CHECK constraint:
ALTER TABLE YourTable
ADD CONSTRAINT CK_MultiColumnCheck
CHECK (Column1 > 10 AND Column2 < 100);This example adds a table-level CHECK constraint named CK_MultiColumnCheck to YourTable, ensuring that both Column1 and Column2 satisfy the specified conditions.
35. Differentiate between a derived persistent attribute and a derived attribute.
- Derived Attribute: A derived attribute is an attribute whose value is calculated or derived from the values of other attributes in the database. The derived value is not stored directly in the database but is computed on demand when needed. For example, ‘age’ can be derived from ‘date of birth’.
- Derived Persistent Attribute: A derived persistent attribute is also derived from other attributes, but its value is stored in the database. This is done to improve query performance by pre-calculating and storing frequently accessed derived values, avoiding repeated calculations. However, maintaining data consistency for persistent derived attributes is crucial, as they need to be updated whenever the source attributes change.
Basics to Advanced – Learn It All!
Full Stack Java Developer Masters ProgramExplore Program
Conclusion
These SQL server interview questions offer a solid foundation for understanding key SQL Server concepts. Practicing these questions and answers will significantly enhance your preparation for your next SQL server interview. To further solidify your SQL skills, consider exploring structured learning resources like certification courses.
To elevate your software development expertise, we recommend checking out Simplilearn’s SQL Certification Course. This comprehensive course can equip you with the necessary skills to become job-ready in the SQL domain.
If you have further questions or require clarification on any of these topics, please feel free to leave a comment below. Our team will respond to you promptly. Start your learning journey today and advance your SQL Server career!

