A transparent proxy server intercepts connections between users and the internet without modifying requests or responses, offering benefits like content filtering and traffic monitoring. At rental-server.net, we help you understand transparent proxies and how they can enhance your server setup, offering comprehensive information and a range of server solutions. Explore our dedicated server options, VPS hosting, and cloud server solutions to find the perfect fit for your needs.
1. Understanding the Basics: What is a Transparent Proxy Server?
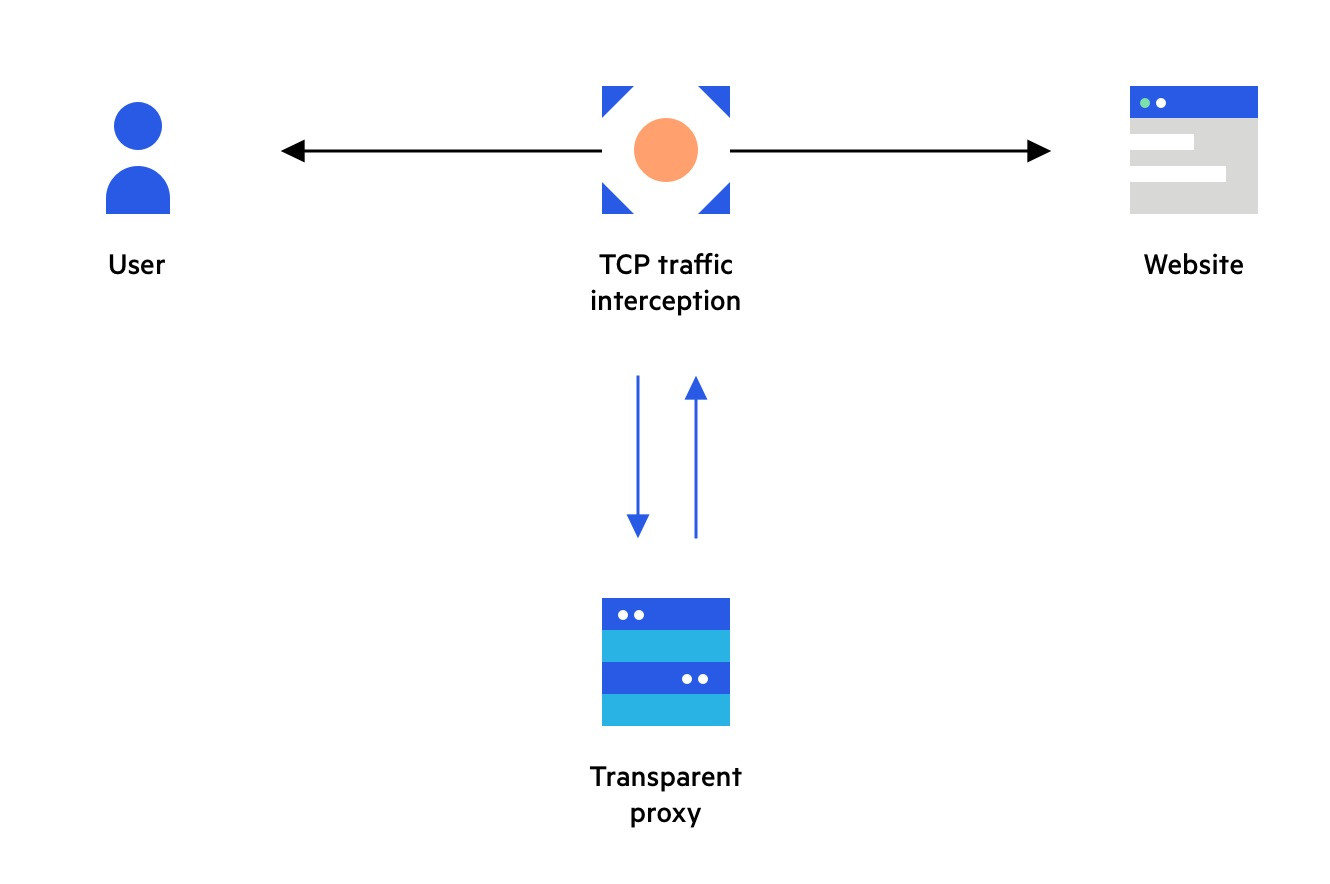
A transparent proxy server, also known as an inline, intercepting, or forced proxy, acts as an intermediary between a user and the internet. The key characteristic is its transparency: it intercepts traffic without altering the requests or responses exchanged between the user and the destination server.
To elaborate:
- Interception: The proxy intercepts network traffic, effectively sitting between the user’s device and the internet.
- No Modification: Unlike other proxies, a transparent proxy forwards requests and receives responses without changing the content.
- Transparency: The user is often unaware that their traffic is being routed through a proxy server.
This type of proxy is favored for its ability to implement policies, monitor traffic, and cache content without requiring any configuration changes on the user’s end.
 Transparent proxy deployment example
Transparent proxy deployment example
2. Transparent Proxy vs. Traditional Proxy: What Are the Key Differences?
The primary difference between a transparent proxy and a traditional proxy lies in their visibility and configuration requirements. Transparent proxies operate invisibly to the user, while traditional proxies require explicit configuration.
| Feature | Transparent Proxy | Traditional Proxy |
|---|---|---|
| Visibility | Invisible to the end-user; no configuration required on the client-side. | Requires explicit configuration in the user’s browser or operating system. |
| Configuration | Configured on the network infrastructure level (e.g., router or gateway). | Configured on the client device. |
| Use Cases | Content filtering, traffic monitoring, transparent caching, forced authentication. | Bypassing geo-restrictions, enhancing privacy, accessing content from different regions. |
| Deployment | Typically deployed by network administrators or ISPs. | Typically configured by individual users. |
The choice between transparent and traditional proxies depends on the specific requirements and goals of the network administrator or user. Transparent proxies are ideal for situations where centralized control and transparent operation are essential, while traditional proxies are better suited for users who want more control over their internet traffic.
3. How Does a Transparent Proxy Server Work?
A transparent proxy server operates by intercepting network traffic at the network level, typically at a router or gateway. This interception happens without any explicit configuration on the user’s device. Here’s a step-by-step breakdown:
-
User Request: A user initiates a request to access a website or online service.
-
Traffic Interception: The network infrastructure, such as a router, intercepts the traffic.
-
Proxy Processing: The transparent proxy server processes the request. This may include:
- Content Filtering: Checking if the requested content is allowed based on predefined policies.
- Caching: Checking if the content is already stored in the proxy’s cache.
- Traffic Monitoring: Logging the request for monitoring and analysis purposes.
-
Forwarding the Request: If the content is not cached and the request is allowed, the proxy forwards the request to the destination server.
-
Receiving the Response: The destination server sends the response back to the proxy server.
-
Processing the Response: The proxy server may cache the response for future requests.
-
Delivering the Response: The proxy server forwards the response to the user’s device.
This entire process occurs without the user being aware that their traffic is being routed through a proxy server.
4. What Are the Benefits of Using a Transparent Proxy Server?
Transparent proxy servers offer several benefits for network administrators and organizations. These include:
- Content Filtering: Transparent proxies can filter out unwanted content, such as malicious websites or inappropriate material.
- Traffic Monitoring: They allow network administrators to monitor user traffic and behavior for security and compliance purposes.
- Transparent Caching: Caching frequently accessed content can improve network performance and reduce bandwidth consumption.
- Forced Authentication: Transparent proxies can be used to force users to authenticate themselves before accessing the network.
These benefits make transparent proxy servers a valuable tool for managing and securing networks.
5. What Are the Drawbacks of Using a Transparent Proxy Server?
While transparent proxy servers offer numerous benefits, they also have some drawbacks:
- Privacy Concerns: Users may be concerned about their privacy if their traffic is being monitored without their knowledge or consent.
- Performance Overhead: Intercepting and processing traffic can introduce some performance overhead, potentially slowing down network speeds.
- Complexity: Setting up and managing a transparent proxy server can be complex, requiring technical expertise.
- Circumvention: Technically savvy users may find ways to circumvent the proxy, defeating its intended purpose.
Despite these drawbacks, the benefits of transparent proxy servers often outweigh the disadvantages, especially in organizations with strict security and compliance requirements.
6. Transparent Proxy Server Use Cases: Where Are They Commonly Used?
Transparent proxy servers are commonly used in various environments to enhance security, manage network traffic, and improve performance. Here are some typical use cases:
- Corporate Networks: To enforce acceptable use policies, filter content, and monitor employee internet usage.
- Educational Institutions: To protect students from inappropriate content and manage network bandwidth.
- Public Wi-Fi Hotspots: To force users to authenticate and agree to terms of service before accessing the internet.
- ISPs (Internet Service Providers): To cache content and improve network performance for their subscribers.
- Government Agencies: To filter content and monitor internet traffic for security and compliance purposes.
In each of these scenarios, the transparent proxy server helps to maintain a secure and efficient network environment.
7. Setting Up a Transparent Proxy Server: What Are the Key Steps?
Setting up a transparent proxy server involves several key steps:
- Choose Proxy Software: Select a suitable proxy server software, such as Squid, which is a popular open-source option.
- Install and Configure: Install the proxy software on a dedicated server or virtual machine and configure it according to your network requirements.
- Configure Network Devices: Configure your network devices, such as routers, to redirect traffic to the proxy server.
- Define Policies: Define the policies you want to enforce, such as content filtering rules and access controls.
- Test and Monitor: Test the proxy server to ensure it is working correctly and monitor its performance to identify any issues.
Proper planning and configuration are essential for a successful transparent proxy server deployment.
8. What is Squid Transparent Proxy Server?
Squid is a widely-used open-source proxy server and cache that supports various protocols, including HTTP, HTTPS, and FTP. It can be configured as a transparent proxy to intercept and process network traffic without requiring any changes on the client-side.
Key features of Squid include:
- Caching: Squid caches frequently accessed content to improve network performance and reduce bandwidth consumption.
- Content Filtering: It supports content filtering through access control lists (ACLs) and external helper programs.
- Access Control: Squid allows you to control access to websites and online services based on various criteria, such as IP address, time of day, and user identity.
- Logging and Monitoring: It provides detailed logs and monitoring capabilities to track network traffic and identify potential issues.
Squid is a powerful and flexible proxy server that is well-suited for use as a transparent proxy in a variety of environments.
9. Configuring Squid as a Transparent Proxy: A Step-by-Step Guide
Configuring Squid as a transparent proxy involves several steps:
- Install Squid: Install the Squid package on your server using your distribution’s package manager (e.g.,
apt-get install squidon Debian/Ubuntu). - Configure Squid: Edit the Squid configuration file (
squid.conf) to enable transparent proxying. This typically involves setting thehttp_portdirective to intercept traffic and configuring access control lists (ACLs) to define your policies. - Redirect Traffic: Configure your network devices, such as routers, to redirect HTTP and HTTPS traffic to the Squid server. This can be done using techniques like Web Cache Communication Protocol (WCCP) or port redirection.
- Test the Configuration: Test the configuration by browsing the web and verifying that your traffic is being intercepted and processed by Squid.
- Monitor Performance: Monitor Squid’s performance to ensure it is handling the traffic load and caching content effectively.
A properly configured Squid transparent proxy can significantly improve network performance and security.
10. Transparent Proxy Authentication: How Does It Work?
Transparent proxy authentication is the process of authenticating users without requiring them to explicitly enter their credentials. This is typically done using techniques like:
- IP Address Authentication: Granting access based on the user’s IP address.
- Cookie-Based Authentication: Using cookies to identify authenticated users.
- Kerberos Authentication: Using the Kerberos protocol to authenticate users based on their network credentials.
Transparent proxy authentication can simplify the user experience and improve security by ensuring that only authorized users can access the network.
11. Transparent Proxy vs. Reverse Proxy: Understanding the Differences
While both transparent proxies and reverse proxies act as intermediaries, they serve different purposes and are deployed in different environments.
| Feature | Transparent Proxy | Reverse Proxy |
|---|---|---|
| Purpose | Intercepts traffic between users and the internet. | Protects and optimizes web servers. |
| Deployment | Typically deployed on the client-side. | Typically deployed on the server-side. |
| Visibility | Invisible to the end-user. | Acts as a single point of contact for clients. |
| Use Cases | Content filtering, traffic monitoring. | Load balancing, security, caching. |
In essence, a transparent proxy manages outbound traffic from clients, while a reverse proxy manages inbound traffic to servers.
12. Security Implications of Transparent Proxy Servers: What You Need to Know
Transparent proxy servers have significant security implications:
- Content Filtering: They can block access to malicious websites and prevent users from downloading harmful content.
- Traffic Monitoring: They allow network administrators to monitor user traffic and detect potential security threats.
- SSL Interception: Some transparent proxies can intercept SSL traffic, allowing them to inspect encrypted content. This can be a security risk if not implemented properly.
- Privacy Concerns: Users may be concerned about their privacy if their traffic is being monitored without their knowledge or consent.
It’s crucial to carefully consider the security implications of transparent proxy servers and implement appropriate safeguards to protect user privacy and data security.
13. Transparent Proxy and SSL/TLS: How to Handle Encrypted Traffic
Handling SSL/TLS traffic with a transparent proxy requires careful consideration. There are two main approaches:
- SSL Bridging: The proxy decrypts the SSL traffic, inspects it, and then re-encrypts it before forwarding it to the destination server. This allows the proxy to perform content filtering and traffic monitoring on encrypted traffic, but it also introduces security risks.
- SSL Passthrough: The proxy forwards the SSL traffic without decrypting it. This preserves the end-to-end encryption but limits the proxy’s ability to inspect the traffic.
The choice between SSL bridging and SSL passthrough depends on the specific security requirements and privacy concerns of the organization.
14. Transparent Proxy and Caching: How to Improve Network Performance
Caching is a key feature of transparent proxy servers that can significantly improve network performance. By caching frequently accessed content, the proxy can serve requests directly from its cache, reducing the load on the origin server and improving response times for users.
Effective caching strategies include:
- Content Expiration: Setting appropriate expiration times for cached content to ensure that users receive fresh data.
- Cache Hierarchy: Using a multi-level cache hierarchy to optimize cache performance.
- Content Invalidation: Invalidating cached content when it changes on the origin server.
Properly configured caching can greatly enhance the performance of a transparent proxy server.
15. Bypassing Transparent Proxy Servers: Techniques and Countermeasures
Technically savvy users may attempt to bypass transparent proxy servers using various techniques:
- Using a VPN: A VPN (Virtual Private Network) encrypts all traffic and routes it through a remote server, bypassing the proxy.
- Using a Traditional Proxy: Configuring a traditional proxy in the browser or operating system can override the transparent proxy.
- Using Tor: Tor is an anonymizing network that routes traffic through multiple relays, making it difficult to trace the origin of the traffic.
Countermeasures to prevent bypassing include:
- Blocking VPN and Proxy Traffic: Blocking traffic to known VPN and proxy servers.
- Enforcing Proxy Settings: Using group policies or other mechanisms to enforce proxy settings on user devices.
- Monitoring Network Traffic: Monitoring network traffic for suspicious activity that may indicate bypassing attempts.
Staying ahead of bypassing techniques requires ongoing vigilance and adaptation.
16. Transparent Proxy Logging and Monitoring: What to Track and Why
Logging and monitoring are essential for managing and troubleshooting transparent proxy servers. Key metrics to track include:
- Traffic Volume: Monitoring the amount of traffic passing through the proxy server.
- Cache Hit Ratio: Tracking the percentage of requests that are served from the cache.
- Response Times: Measuring the time it takes for the proxy server to respond to requests.
- Error Rates: Monitoring the number of errors encountered by the proxy server.
- Security Events: Logging security-related events, such as blocked websites and detected threats.
Analyzing these metrics can help identify performance bottlenecks, security issues, and other problems that may affect the proxy server.
17. Load Balancing with Transparent Proxy Servers: How to Distribute Traffic
Load balancing is the process of distributing network traffic across multiple servers to improve performance and reliability. Transparent proxy servers can be used to load balance traffic to multiple backend servers.
Load balancing techniques include:
- Round Robin: Distributing traffic to servers in a sequential order.
- Least Connections: Distributing traffic to the server with the fewest active connections.
- Weighted Load Balancing: Distributing traffic based on the capacity or performance of each server.
Load balancing can significantly improve the scalability and availability of web applications and online services.
18. Legal and Ethical Considerations for Transparent Proxy Servers
Using transparent proxy servers raises several legal and ethical considerations:
- Privacy: Monitoring user traffic without their knowledge or consent may violate privacy laws.
- Transparency: Users should be informed about the presence of a transparent proxy server and its purpose.
- Data Security: Protecting user data from unauthorized access or disclosure is essential.
- Compliance: Complying with all applicable laws and regulations, such as GDPR and CCPA.
Organizations should carefully consider these legal and ethical considerations before deploying transparent proxy servers.
19. The Future of Transparent Proxy Servers: Trends and Innovations
The future of transparent proxy servers is likely to be shaped by several trends and innovations:
- Cloud-Based Proxies: Cloud-based proxy services offer scalability, flexibility, and ease of management.
- AI-Powered Security: Artificial intelligence (AI) can be used to enhance the security of transparent proxy servers by detecting and blocking sophisticated threats.
- Improved Caching: Advanced caching techniques, such as content-aware caching, can further improve network performance.
- Enhanced Privacy: Privacy-enhancing technologies, such as differential privacy, can be used to protect user privacy while still allowing for traffic monitoring.
These trends and innovations promise to make transparent proxy servers even more powerful and versatile in the future.
20. How to Choose the Right Transparent Proxy Server Solution for Your Needs
Choosing the right transparent proxy server solution depends on your specific requirements and goals. Key factors to consider include:
- Performance: The proxy server should be able to handle the expected traffic load without introducing significant performance overhead.
- Security: The proxy server should provide robust security features, such as content filtering and threat detection.
- Scalability: The proxy server should be able to scale to meet the growing needs of your organization.
- Manageability: The proxy server should be easy to manage and maintain.
- Cost: The proxy server should fit within your budget.
Carefully evaluating these factors can help you choose the best transparent proxy server solution for your needs.
Ready to explore transparent proxy server solutions and enhance your server infrastructure? Visit rental-server.net today to discover a wide range of server options, including dedicated servers, VPS hosting, and cloud servers tailored to meet your unique requirements.
Address: 21710 Ashbrook Place, Suite 100, Ashburn, VA 20147, United States
Phone: +1 (703) 435-2000
Website: rental-server.net
FAQ: Transparent Proxy Servers
1. What is the primary function of a transparent proxy server?
A transparent proxy server primarily intercepts network traffic between users and the internet without requiring any client-side configuration, enabling content filtering, traffic monitoring, and caching.
2. How does a transparent proxy differ from a traditional proxy?
A transparent proxy operates invisibly to the user, while a traditional proxy requires explicit configuration on the user’s device.
3. What are the main benefits of using a transparent proxy?
The main benefits include content filtering, traffic monitoring, transparent caching, and forced authentication.
4. What are some potential drawbacks of using a transparent proxy?
Potential drawbacks include privacy concerns, performance overhead, complexity, and the possibility of circumvention by technically savvy users.
5. In what scenarios is a transparent proxy commonly used?
Transparent proxies are commonly used in corporate networks, educational institutions, public Wi-Fi hotspots, ISPs, and government agencies.
6. How can Squid be configured as a transparent proxy?
Squid can be configured as a transparent proxy by installing the Squid package, editing the configuration file, redirecting traffic, testing the configuration, and monitoring performance.
7. What is transparent proxy authentication?
Transparent proxy authentication is the process of authenticating users without requiring them to explicitly enter their credentials, often using IP address, cookie-based, or Kerberos authentication.
8. What are the security implications of using a transparent proxy?
Security implications include content filtering, traffic monitoring, SSL interception, and potential privacy concerns.
9. How does a transparent proxy handle SSL/TLS traffic?
A transparent proxy can handle SSL/TLS traffic through SSL bridging (decrypting and re-encrypting traffic) or SSL passthrough (forwarding traffic without decrypting it).
10. How can caching improve network performance with a transparent proxy?
Caching improves network performance by storing frequently accessed content and serving requests directly from the cache, reducing the load on the origin server and improving response times.

