Ensuring the security of your web services is paramount, especially when it comes to SSL/TLS encryption. For anyone responsible for web hosting, understanding how your server stacks up against industry security standards is crucial. This is where the Ssl Labs Server Test comes into play, a powerful and free online tool to analyze your server’s SSL/TLS configuration. When I first discovered this tool, I was immediately curious to see how my own server would perform. The results can be eye-opening, and the process of improving your score is a valuable learning experience in web security optimization. Let’s explore how to enhance your Apache configurations to achieve a top score and strengthen your website’s security.
To demonstrate the impact of different configurations, we’ll begin with a deliberately weakened Apache setup, showcasing a low initial score. Then, we’ll incrementally apply security enhancements, observing how each adjustment affects the SSL Labs Server Test results. This step-by-step approach will highlight the significance of each configuration change in bolstering your server’s security posture.
 Initial SSL Labs Server Test Score: F Grade, highlighting critical security vulnerabilities.
Initial SSL Labs Server Test Score: F Grade, highlighting critical security vulnerabilities.
As you can see, our starting point is far from ideal. To be completely transparent, this “F” grade wasn’t achieved by accident. I intentionally downgraded my Apache configuration to illustrate the potential security weaknesses if best practices are not followed. Interestingly, even with a default, unoptimized configuration on a fully patched CentOS 7 server with Apache 2.4.6, the baseline security isn’t terrible. However, to achieve this dismal score, I enabled insecure cipher suites, disabled secure ones, and employed a weak 1024-bit certificate from an untrusted Certificate Authority. I even attempted to enable outdated SSLv2 and v3 protocols, but thankfully, my Apache version no longer supports them. This underscores the importance of explicitly disabling these obsolete and vulnerable protocols in your Apache configuration. Ensure you have a line similar to the one below in your configuration to prevent the use of insecure SSL/TLS versions:
SSLProtocol all -SSLv2 -SSLv3 -TLSv1Our first crucial step towards improving this score is to rectify the weak certificate. We’ll request a new certificate using Let’s Encrypt, a free, automated, and open Certificate Authority. When generating your Certificate Signing Request (CSR), ensure you use at least a 2048-bit private key for robust security. For a streamlined CSR generation process, consider using CertificateTools.com. This helpful tool simplifies CSR creation for both RSA and ECC keys and conveniently provides the corresponding OpenSSL commands for local execution.
 Improved SSL Labs Server Test Score after updating to a valid certificate from Let's Encrypt: C Grade.
Improved SSL Labs Server Test Score after updating to a valid certificate from Let's Encrypt: C Grade.
Significant progress! By simply replacing the insecure certificate with a valid one from Let’s Encrypt, we’ve eliminated several warnings and elevated our grade from an “F” to a “C”. However, there’s still room for substantial improvement. The next critical area to address is the server’s supported cipher suites.
The next step involves strengthening our cipher suite configuration. Cipher suites are sets of cryptographic algorithms that are used to establish secure connections. By default, servers might support a wide range of ciphers, including some that are considered weak or outdated. We need to refine this selection to prioritize strong and secure ciphers.
After adjusting the cipher suites, re-running the SSL Labs Server Test reveals a crucial point: the server does not support Forward Secrecy. Forward Secrecy (FS), also known as Perfect Forward Secrecy (PFS), is a critical security feature that ensures that even if a server’s private key is compromised in the future, past communication sessions remain secure. This is achieved by using ephemeral (temporary) session keys that are unique to each connection.
To enable Forward Secrecy, we must include ECDHE (Elliptic Curve Diffie-Hellman Ephemeral) cipher suites in our Apache configuration. I deliberately omitted these ciphers earlier to highlight the importance of Forward Secrecy and its impact on the SSL Labs score. For optimal cipher hardening and full support for Perfect Forward Secrecy, ensure the following lines are present in your Apache configuration:
SSLHonorCipherOrder on
SSLCipherSuite ALL:!aNULL:!eNULL:!LOW:!3DES:!MD5:!EXP:!PSK:!SRP:!DSS:!RC4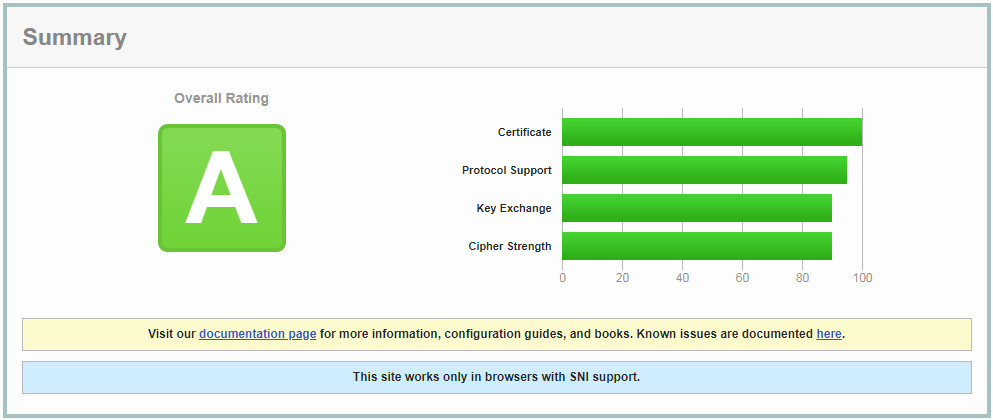 SSL Labs Server Test Score after implementing strong cipher suites and enabling Forward Secrecy: A Grade.
SSL Labs Server Test Score after implementing strong cipher suites and enabling Forward Secrecy: A Grade.
Excellent progress! We’ve now achieved an “A” grade. To reach the coveted “A+” score on the SSL Labs Server Test, we need to implement HTTP Strict Transport Security (HSTS). HSTS is a simple yet powerful security header that instructs web browsers to exclusively communicate with the server over HTTPS for a specified duration. This effectively prevents downgrade attacks like SSLStrip, where attackers attempt to force browsers to use insecure HTTP connections.
Enabling HSTS in Apache is straightforward. You can add the following line to your configuration. This header sets a max-age of two years (63072000 seconds), includes subdomains, and enables preloading, which further enhances security by pre-registering your domain in browser HSTS lists.
Header always set Strict-Transport-Security "max-age=63072000; includeSubdomains; preload"With HSTS enabled, our server now achieves the highest possible rating: A+ on the SSL Labs Server Test.
While we’ve reached an “A+”, there’s another advanced security feature worth mentioning: HTTP Public Key Pinning (HPKP). HPKP allows a website to associate itself with a specific cryptographic public key. During a user’s first visit, the browser stores (“pins”) at least one certificate from the server’s certificate chain. On subsequent visits, if the server presents a certificate chain that doesn’t include the pinned certificate, the browser will prevent the user from accessing the site. HPKP is a potent defense against man-in-the-middle (MITM) attacks.
However, implementing HPKP requires careful planning and diligent maintenance. Incorrectly configured HPKP can inadvertently block legitimate users from accessing your website. Furthermore, major browsers like Chrome have announced plans to deprecate HPKP due to the risks of misconfiguration and potential for denial-of-service. Therefore, while HPKP offers strong security benefits, it’s not generally recommended for most websites unless you have a deep understanding of its intricacies and are prepared for the operational overhead.
In conclusion, regularly testing your server with the SSL Labs Server Test is a vital practice for maintaining robust web security. By implementing the configurations discussed, including using valid certificates, strong cipher suites with Forward Secrecy, and HSTS, you can significantly improve your security posture and achieve an “A+” rating. I hope this guide has been helpful in understanding how to enhance your server’s SSL/TLS configuration. Feel free to share any questions or comments below.