In the realm of database administration, data integrity stands as a paramount concern. Imagine a scenario where your critical business data, the lifeblood of your operations, becomes silently corrupted, leading to potentially catastrophic consequences. This isn’t a hypothetical threat; it’s a tangible risk, especially when Server And Database configurations aren’t meticulously managed. This article delves into a hands-on demonstration of database corruption, highlighting a critical yet often overlooked server and database setting: PAGE_VERIFY. We’ll explore how easily a database can be compromised when this setting is misconfigured, and more importantly, what steps you can take to fortify your server and database environment against such vulnerabilities.
Let’s dive into a practical example of how data corruption can occur unnoticed. We’ll start by creating a sample database and intentionally disabling a crucial data integrity feature.
CREATEDATABASE[50Ways];
GO
ALTERDATABASE[50Ways] SET PAGE_VERIFY NONE; /* Normally a bad idea */
GO
USE[50Ways];
GO
CREATETABLE[dbo].[ToLeaveYourLover]([Way]VARCHAR(50));
GO
INSERTINTO[dbo].[ToLeaveYourLover]([Way])
VALUES ('Slip out the back, Jack'),
('Make a new plan, Stan'),
('Hop on the bus, Gus'),
('Drop off the key, Lee')
GO
SELECT *
FROM [50Ways]..[ToLeaveYourLover]; /* Yep, we have data */
GO
ALTERDATABASE[50Ways] SET OFFLINE WITH ROLLBACK IMMEDIATE;
GONow, the stage is set to introduce corruption. Using a hex editor, like the freely available xvi32 (ensure you run it as administrator), open the MDF file of the newly created database. This tool allows us to directly inspect and modify the raw data within the database file.
 XVI32 opening the mdf file
XVI32 opening the mdf file
(Alt text: XVI32 hex editor interface displaying the contents of a database MDF file, illustrating direct file access for potential data manipulation.)
Once the MDF file is open in the hex editor, you’re presented with the underlying structure of your database. Contrary to what some might assume, SQL Server doesn’t inherently encrypt data at rest in a way that prevents direct file inspection. Sensitive information, if stored unencrypted within the database, is potentially visible in plain text within the MDF file.
To locate our sample data, we can use the “Find” function within the hex editor and search for the text “Stan”.
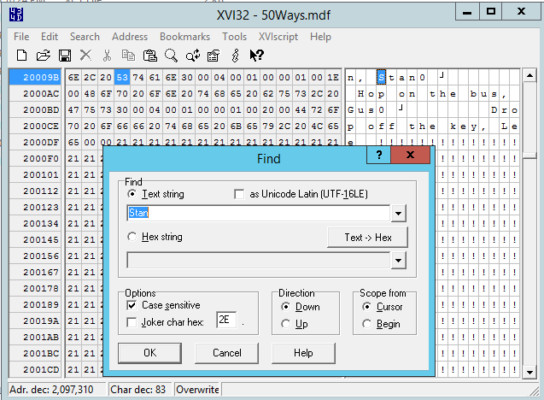 Search function in XVI32 locating text within the MDF file
Search function in XVI32 locating text within the MDF file
(Alt text: XVI32 hex editor search dialog box highlighting the text “Stan” found within the database MDF file, demonstrating the visibility of database content.)
The search will pinpoint the location of the string “Stan” within the file, revealing the raw, unencrypted data. Now, for the corruption part. Within the hex editor, directly modify the “S” in “Stan” to an “F”, effectively changing “Stan” to “Flan”. Save the changes in xvi32 and close the editor.
Bring the database back online in SQL Server:
ALTERDATABASE[50Ways] SET ONLINE;
GO
SELECT *
FROM [50Ways]..[ToLeaveYourLover];Execute the SELECT statement, and you’ll observe that the data has indeed been altered. Instead of “Stan”, you’ll now see “Flan”.
 Screenshot showing corrupted data in SQL Server Management Studio
Screenshot showing corrupted data in SQL Server Management Studio
(Alt text: SQL Server Management Studio output displaying a table with “Flan” instead of “Stan”, illustrating successful data corruption via direct file editing.)
Remarkably, SQL Server doesn’t flag any errors or corruption warnings. From its perspective, the data is perfectly valid. Even running DBCC CHECKDB, a database integrity check command, will not report any inconsistencies in this scenario. This is because PAGE_VERIFY is set to NONE, instructing SQL Server to bypass checksum validations during page reads and writes.
The Impact of Clustered Columnstore Indexes
You might wonder if different indexing strategies influence this behavior. Let’s repeat the experiment, this time incorporating a clustered columnstore index into our table.
CREATEDATABASE[50Ways];
GO
ALTERDATABASE[50Ways] SET PAGE_VERIFY NONE; /* Normally a bad idea */
GO
USE[50Ways];
GO
CREATETABLE[dbo].[ToLeaveYourLover]
(
[ID] INT IDENTITY(1, 1),
[Way] VARCHAR(50),
[Guy] VARCHAR(50)
);
GO
CREATECLUSTEREDCOLUMNSTOREINDEX cci
ON [dbo].[ToLeaveYourLover]
GO
INSERTINTO[dbo].[ToLeaveYourLover]([Way], [Guy])
VALUES ('Slip out the back', 'Jack'),
('Make a new plan', 'Stan'),
('Hop on the bus', 'Gus'),
('Drop off the key', 'Lee')
GO
SELECT *
FROM [50Ways]..[ToLeaveYourLover]; /* Yep, we have data */
GO
ALTERDATABASE[50Ways] SET OFFLINE WITH ROLLBACK IMMEDIATE;
GOAgain, after taking the database offline, we use xvi32 to find “Stan”. As before, the text is readily accessible in plain sight.
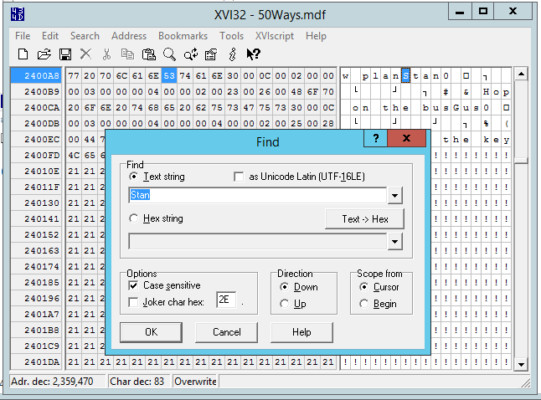 Finding 'Stan' in MDF file with columnstore index using XVI32
Finding 'Stan' in MDF file with columnstore index using XVI32
(Alt text: XVI32 hex editor showing the search result for “Stan” within the MDF file of a database using a clustered columnstore index, highlighting consistent data vulnerability.)
We repeat the process, changing “Stan” to “Flan” using the hex editor, saving the file, and bringing the database back online. Executing the SELECT query reveals the corrupted data, even with a clustered columnstore index in place.
(Alt text: SQL Server Management Studio displaying query results with “Flan” in a table with a clustered columnstore index, demonstrating that index type doesn’t prevent this type of corruption.)
The outcome remains consistent: clustered columnstore indexes, just like traditional rowstore indexes, are susceptible to this type of manual corruption when PAGE_VERIFY is disabled. SQL Server doesn’t detect the alteration, and CHECKDB remains oblivious to the changes.
The Critical Role of PAGE_VERIFY
The vulnerability demonstrated hinges on the PAGE_VERIFY NONE setting we deliberately applied when creating the database. This setting instructs SQL Server to skip page verification processes during disk read and write operations. There are three options for PAGE_VERIFY:
- NONE: As demonstrated, this option disables page verification, leaving your database vulnerable to silent corruption. It is highly discouraged for production environments.
- TORN_PAGE_DETECTION: This option offers minimal protection and is also generally considered insufficient. It detects torn pages, which are pages that were not fully written to disk due to power failures or similar events, but it does not protect against the type of manual corruption we’ve demonstrated or other forms of data corruption.
- CHECKSUM: This is the recommended and robust option. With
CHECKSUMenabled, SQL Server calculates a checksum for each page as it’s written to disk. When the page is subsequently read, SQL Server recalculates the checksum and compares it to the stored checksum. If they don’t match, it indicates data corruption.
Let’s illustrate the difference. If we repeat the initial rowstore or columnstore demo, but this time set PAGE_VERIFY CHECKSUM, the outcome is drastically different. SQL Server immediately detects the corruption when attempting to read the modified page.
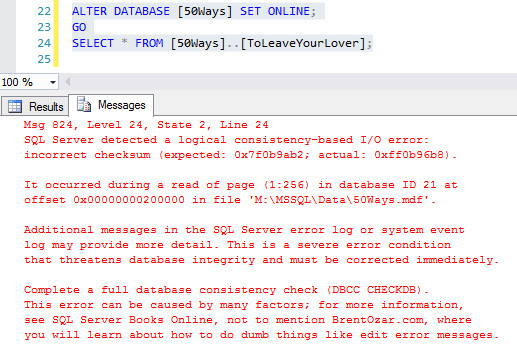 Error message in SQL Server indicating checksum mismatch and database corruption
Error message in SQL Server indicating checksum mismatch and database corruption
(Alt text: SQL Server error message displayed in Management Studio, indicating a checksum error and data corruption detected upon page read.)
The error message clearly signals a checksum mismatch, alerting you to the corruption. It’s crucial to understand that checksum verification is for detection, not recovery. It informs you that data is compromised, but it doesn’t automatically repair it. Data recovery from corruption typically involves restoring from backups.
Essential Steps to Enhance Server and Database Security
To proactively protect your server and database environments, implement these critical steps:
- Assess PAGE_VERIFY Status: Utilize
sp_Blitz, a free SQL Server health check script, to quickly identify databases withPAGE_VERIFYset toNONEorTORN_PAGE_DETECTION. - Enable CHECKSUM Verification: Immediately set
PAGE_VERIFY CHECKSUMfor all databases lacking it. Use theALTER DATABASEcommand:ALTER DATABASE [YourDatabaseName] SET PAGE_VERIFY CHECKSUM; - Trigger Checksum Calculation: Enabling checksum doesn’t retroactively apply it to existing pages until they are rewritten. To expedite this, perform operations that force page writes, such as index rebuilds. Be mindful that this will generate significant transaction log activity.
- Configure Corruption Alerts: Set up SQL Server alerts to promptly notify administrators when corrupt pages are detected. This enables timely intervention and minimizes potential data loss. Resources like Brent Ozar Unlimited’s Blitz documentation provide guidance on configuring these alerts.
- Test Alerting Mechanisms: Simulate a corruption scenario (like the one demonstrated in this article with a test database) and attach it to your production server. Execute a
SELECTquery against the corrupted data to verify that the configured alerts are triggered correctly. - Implement Regular CHECKDB: Establish a schedule for running
DBCC CHECKDBregularly. WhilePAGE_VERIFY CHECKSUMdetects corruption during page reads,CHECKDBperforms a comprehensive database integrity check, including physical and logical consistency. - Address Unencrypted Sensitive Data: Engage stakeholders to discuss the sensitivity of data stored unencrypted in databases. Explore encryption options like Transparent Data Encryption (TDE) or column-level encryption to protect sensitive information at rest.
By prioritizing these steps, you significantly strengthen your server and database infrastructure against silent data corruption and enhance overall data security. Remember, proactive measures are crucial for maintaining data integrity and the reliability of your database systems.
Continue Exploring Database Integrity
Dive deeper into database integrity and related topics with these resources:
- Part 2: Nonclustered Indexes: Let’s Corrupt a Database Together – Part 2: Nonclustered Indexes
- Brent Ozar Unlimited’s sp_Blitz: sp_Blitz® Script
Related Topics
Database Security, SQL Server Administration, Data Integrity, Server Configuration, Data Protection
