Ensuring the security of web services protected by SSL/TLS is paramount. For anyone tasked with this responsibility, the Qualys Ssl Server Test stands out as an invaluable tool to assess and enhance your configuration. When I first encountered this platform, I was immediately intrigued to see how my server would measure up. The results can be eye-opening, and the process of optimizing your setup for a better score is incredibly educational and rewarding in terms of bolstering your web security posture.
In this guide, I’ll share insights derived from working with Apache configurations to help you save time and deepen your understanding of web security principles. We’ll start by dissecting a deliberately weakened Apache setup and gradually strengthen it, observing the impact of each configuration tweak on the Qualys SSL Server Test results.
Initial Qualys SSL Labs Server Test result showing an “F” grade due to insecure configuration.
The initial test reveals a concerning “F” grade. To be transparent, this score is the result of intentionally weakening my Apache configuration to highlight common vulnerabilities. In a default setup on a fully patched CentOS 7 web server with Apache 2.4.6, the baseline security is reasonably sound. To achieve this failing grade, I enabled a wide range of ciphers, specifically excluding secure ones, and employed a weak 1024-bit certificate from an untrusted Certificate Authority to amplify the negative impact. I even attempted to enable outdated SSLv2 and v3 protocols, but thankfully, my Apache version no longer supports them.
It’s crucial to explicitly disable these obsolete and insecure protocols in your Apache configuration. Ensure you have a line similar to the one below in your SSL configuration file:
SSLProtocol all -SSLv2 -SSLv3 -TLSv1This line ensures that only TLS protocols beyond version 1.0 are enabled, mitigating risks associated with older, vulnerable protocols.
Let’s begin the improvement process by addressing the weak certificate. We’ll request a new one using Let’s Encrypt, a free, automated, and open certificate authority, and ensure we use at least a 2048-bit private key for enhanced security. For generating your Certificate Signing Request (CSR), CertificateTools.com offers a user-friendly tool. It supports both RSA and ECC keys and conveniently provides the OpenSSL commands for local execution.

Qualys SSL Labs Server Test result after updating to a valid certificate, showing improved but still unsatisfactory grade.
After updating the certificate, the Qualys SSL Server Test shows noticeable improvement. We’ve eliminated several warnings, but the overall grade is still an “F”. The next step is to refine the supported cipher suites, which play a crucial role in the security and performance of SSL/TLS connections.
The next configuration adjustment focuses on cipher suites. Cipher suites are sets of cryptographic algorithms that SSL/TLS uses to secure connections. Choosing the right cipher suites is crucial for both security and performance.
SSLHonorCipherOrder on
SSLCipherSuite "EECDH+ECDSA+AESGCM EECDH+RSA+AESGCM EECDH+ECDSA+CHACHA20 EECDH+RSA+CHACHA20 EECDH+AESGCM EECDH+CHACHA20 EDH+AESGCM EDH+CHACHA20 !aNULL:!eNULL:!EXPORT:!DES:!RC4:!MD5:!PSK:!aECDH:!EDH-DSS-DES-CBC3-SHA:!EDH-RSA-DES-CBC3-SHA:!KRB5-DES-CBC3-SHA"By implementing these directives in your Apache configuration, you prioritize secure and modern cipher suites. SSLHonorCipherOrder on forces the server to choose ciphers in the order specified, rather than allowing the client to dictate cipher preference, enhancing security. The SSLCipherSuite line defines a strong set of ciphers, prioritizing:
- EECDH (Elliptic Curve Ephemeral Diffie-Hellman): Key exchange algorithm offering forward secrecy.
- ECDSA (Elliptic Curve Digital Signature Algorithm) & RSA: Key exchange and authentication algorithms.
- AESGCM (Advanced Encryption Standard Galois/Counter Mode) & CHACHA20: Modern, high-performance encryption algorithms.
The !aNULL:!eNULL:!EXPORT:!DES:!RC4:!MD5:!PSK:!aECDH:!EDH-DSS-DES-CBC3-SHA:!EDH-RSA-DES-CBC3-SHA:!KRB5-DES-CBC3-SHA part explicitly excludes weaker or insecure ciphers, ensuring only robust encryption methods are used.
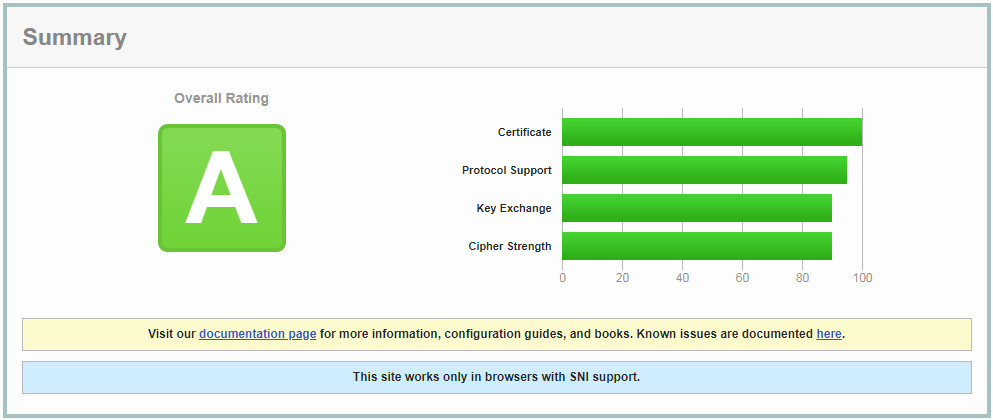
Qualys SSL Labs Server Test result showing an “A” grade after cipher suite hardening.
With these cipher configurations, the server achieves an “A” grade. However, the results highlight that “Forward Secrecy” is not fully supported. This is because the ECDHE (Elliptic Curve Diffie-Hellman Ephemeral) cipher suite was intentionally omitted to emphasize its importance. Forward secrecy ensures that even if the server’s private key is compromised in the future, past communication remains secure. To fully enable perfect forward secrecy and further harden cipher settings, ensure the following lines are in your Apache configuration:
SSLHonorCipherOrder on
SSLCipherSuite ALL:!aNULL:!eNULL:!LOW:!3DES:!MD5:!EXP:!PSK:!SRP:!DSS:!RC4This configuration prioritizes all strong ciphers (ALL), while explicitly excluding weaker and less secure ones using negation operators (!). This refined cipher suite configuration is crucial for achieving a top-tier security posture.
To finally reach the coveted “A+” score on the Qualys SSL Server Test, we need to enable HTTP Strict Transport Security (HSTS). HSTS is a security header that instructs browsers to interact with the website exclusively over HTTPS for a specified period. This effectively prevents downgrade attacks, such as SSLStrip, where attackers attempt to force browsers to use insecure HTTP. HSTS is a straightforward yet powerful security enhancement. While it can be enabled via plugins in platforms like WordPress, Apache provides a direct configuration method using the following directive:
Header always set Strict-Transport-Security "max-age=63072000; includeSubdomains; preload"This line adds the HSTS header to every HTTP response. Let’s break down the parameters:
max-age=63072000: Specifies the duration (in seconds) for which the browser should enforce HTTPS. 63072000 seconds equals two years, a recommended value for long-term HSTS enforcement.includeSubdomains: Extends HSTS protection to all subdomains of the domain.preload: Indicates that the domain is eligible for inclusion in browser HSTS preload lists. Preloading ensures HSTS is enforced from the very first connection to the domain.
By implementing HSTS, you significantly enhance your website’s security and protect users from protocol downgrade attacks.
Beyond HSTS, further HTTPS security enhancements can be achieved by implementing HTTP Public Key Pinning (HPKP). HPKP instructs browsers to store (“pin”) one or more certificates from the website’s certificate chain upon the first visit. Subsequent visits must present a certificate chain that includes a pinned certificate. This mechanism is highly effective against man-in-the-middle (MITM) attacks. However, HPKP is complex to manage and maintain correctly. If misconfigured, it can inadvertently block legitimate users from accessing the website. While HPKP offers robust security, it demands a deep understanding and meticulous management. Notably, major browsers like Chrome have deprecated HPKP due to its complexity and potential for misuse. Therefore, while HPKP represents an advanced security measure, it’s not generally recommended for most deployments due to its operational challenges and the risk of misconfiguration.
This guide aimed to provide a practical walkthrough of improving your SSL/TLS configuration using the Qualys SSL Server Test. By implementing these steps, you can significantly enhance your web server’s security posture and achieve a top-tier rating. Remember to regularly test your configuration and stay updated with the latest security best practices.

