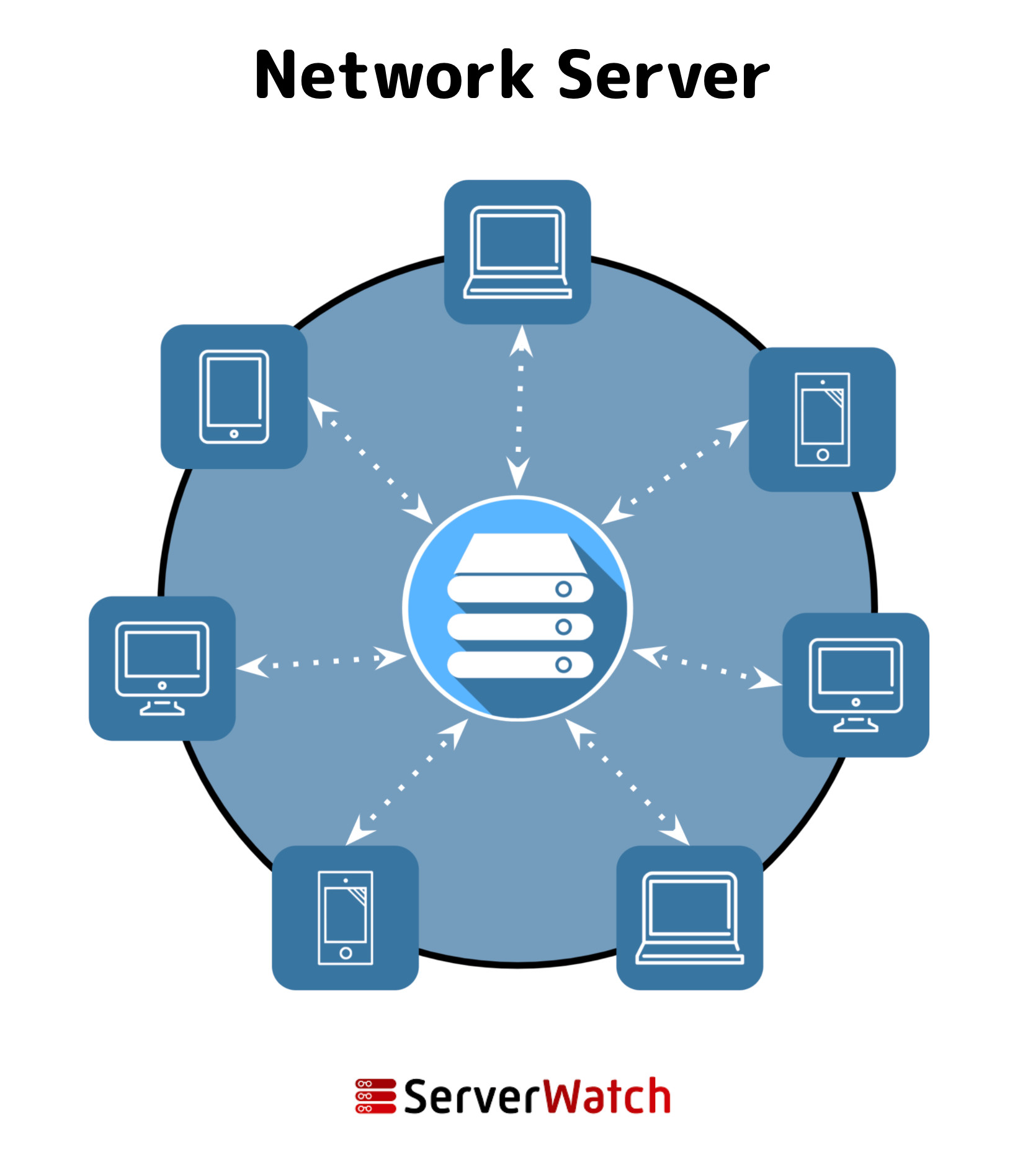
 A graphic designed to show how a network server works with and provides resources to a network. Designed by Sam Ingalls.
A graphic designed to show how a network server works with and provides resources to a network. Designed by Sam Ingalls.
In the realm of computer networking, a Network Server stands as a robust and specialized computer system. Its primary function is to centrally manage network resources and deliver essential services to other computers, known as clients, within a network environment. Unlike a typical workstation, a network server is explicitly designed and optimized for demanding network tasks. These tasks encompass a wide array of functionalities, including efficient data storage, seamless application hosting, reliable email processing, and much more, all tailored to meet the needs of a connected user base.
From the confines of a small business’s local network to the expansive and intricate architectures of cloud-based infrastructures, network servers are indispensable. They serve as the very cornerstone that ensures the continuous and fluid exchange of information and services. Effectively, they are the linchpin that keeps the wheel of digital operations turning smoothly. By centralizing crucial data and applications, network servers significantly simplify management, streamline maintenance procedures, and enhance the overall security posture of an organization’s vital digital assets.
This article aims to provide a comprehensive exploration of network servers. We will delve into the operational mechanics of these critical systems, examine the diverse types of network servers available, and analyze their ongoing evolution in the face of technological advancements. Furthermore, we will guide you through the process of setting up a basic network server and explore the most prominent use cases that highlight their versatility. Finally, we will address the paramount importance of network server security and the measures necessary to safeguard these essential components of modern IT infrastructure.
How Network Servers Operate
Network servers are the central nervous system of any computer network, meticulously orchestrating communication and data flow among connected devices. To understand their crucial role, let’s break down the key steps in their operation:
1. Request Reception
Network servers are perpetually in listening mode, vigilantly awaiting incoming requests from client computers within the network. These requests can span a broad spectrum of actions, from simple tasks like accessing a specific file or executing a program to more complex operations such as retrieving email data or initiating database queries. The fundamental responsibility of the server is to process these requests and provide a timely and appropriate response.
2. Processing and Response Generation
Upon receiving a client request, the network server initiates a processing sequence tailored to the nature of the request and the resources required to fulfill it. For example, a request to load a webpage will be handled differently from a request to access a database record. The server leverages its sophisticated hardware and software resources to execute the requested operation. Once processed, the server transmits the requested data or a confirmation message back to the requesting client, ensuring seamless communication and task completion.
3. Resource Management
Efficiency in resource allocation is a hallmark of network servers. They are engineered to adeptly manage and distribute available resources, including processing power, memory, and storage capacity. This involves skillfully handling numerous concurrent requests, prioritizing critical tasks, and optimizing hardware utilization to ensure peak performance and responsiveness under varying loads.
4. Network Administration
Beyond serving individual client requests, network servers play a vital administrative role in maintaining the overall network health and efficiency. This encompasses essential network management tasks such as dynamically assigning IP addresses to devices, effectively managing network traffic flow to prevent congestion, ensuring the integrity and consistency of data transmission, and enforcing robust security protocols to protect the network from unauthorized access and threats.
5. Service Specialization
Network servers are often specialized to provide specific types of services, enhancing their efficiency and effectiveness in targeted areas. For instance, a web server is dedicated to hosting websites and delivering web content, while a file server is optimized for managing and sharing files and data across the network. Similarly, a mail server is specifically designed to handle email storage, sending, and receiving, ensuring reliable email communication within the network.
Types of Network Servers
Network servers are categorized based on the distinct services they offer, with each type playing a unique and crucial role in the overall network infrastructure. Understanding these different server types is essential for designing and managing networks effectively. Here are some prevalent categories of network servers:
- Web Servers: These servers are the backbone of the internet, hosting websites and delivering web pages and related content to users’ browsers upon request. They use protocols like HTTP to communicate and are fundamental for online presence.
- File Servers: Designed for centralized file storage and management, file servers enable users to store, access, and share files across a network. They are essential for collaboration and data management in organizations.
- Mail Servers: These servers handle the intricacies of email communication, managing the sending, receiving, and storage of emails. They utilize protocols like SMTP, POP3, and IMAP to ensure reliable email services.
- Database Servers: Database servers are powerful systems that store and manage databases, providing access to data for applications and users. They are critical for applications requiring structured data storage and retrieval, such as CRM and ERP systems.
- Application Servers: These servers host and run applications, providing the necessary environment and resources for software applications to operate and be accessed by multiple users over a network.
- Print Servers: Print servers manage print jobs and printers, allowing multiple users on a network to share printing resources efficiently.
- Proxy Servers: Acting as intermediaries between clients and the internet, proxy servers enhance security, control web access, and improve network performance by caching frequently accessed content.
- DNS Servers (Domain Name System): DNS servers translate domain names (like “google.com”) into IP addresses, enabling users to access websites and online resources using easy-to-remember names.
- DHCP Servers (Dynamic Host Configuration Protocol): DHCP servers automatically assign IP addresses and network configuration parameters to devices on a network, simplifying network administration and device connectivity.
- VPN Servers (Virtual Private Network): VPN servers provide secure and encrypted connections between networks or devices, enabling secure remote access and enhancing online privacy.
Evolution of Network Servers
The landscape of network servers is in constant flux, driven by relentless technological innovation and the ever-evolving demands of the digital world. Several key trends are shaping the future of network servers:
Increased Virtualization and Cloud Computing
The paradigm of network servers is undergoing a significant transformation towards virtualization and cloud computing. This shift offers compelling advantages, most notably enhanced scalability. Virtualization allows for the creation of multiple virtual servers on a single physical server, optimizing resource utilization and reducing hardware costs. Cloud computing takes this further, offering on-demand access to server resources over the internet, providing unparalleled flexibility and scalability. This transition also minimizes the need for extensive physical infrastructure, leading to substantial cost reductions and simplified IT management. Cloud-based servers empower businesses with the agility to access server resources and applications from virtually anywhere, fostering seamless collaboration and enabling robust remote work capabilities.
Enhanced Security Measures
In response to the escalating sophistication and frequency of cyber threats, network servers are continually incorporating increasingly advanced security measures. Robust encryption techniques are now standard, safeguarding sensitive data both during transmission and when stored. Next-generation firewalls, intrusion detection, and prevention systems are becoming integral components of server security architectures, providing proactive threat mitigation. The implementation of regular security updates and patches is now a critical operational norm, ensuring that servers are promptly protected against newly discovered vulnerabilities, thereby maintaining the confidentiality, integrity, and availability of stored and processed data.
Energy Efficiency and Green Computing
With growing global awareness of environmental sustainability, energy efficiency and green computing practices are becoming increasingly paramount in network server design and operation. This encompasses a range of initiatives, including optimizing server operations to minimize power consumption, utilizing energy-efficient hardware components, and adopting sustainable practices within data centers. These environmentally conscious efforts not only contribute to reducing the carbon footprint of IT operations but also translate into significant cost savings through reduced energy expenditure.
Greater Automation and AI Integration
Automation and artificial intelligence (AI) are revolutionizing network server management, introducing new levels of efficiency and proactive capabilities. AI algorithms are being deployed to facilitate predictive maintenance, enabling servers to anticipate potential hardware or software issues before they escalate into critical problems. Automation is streamlining essential tasks such as load balancing and resource allocation, optimizing server performance and minimizing the need for manual intervention. The integration of AI and automation technologies is enhancing the overall reliability, efficiency, and resilience of network servers, reducing downtime and improving operational effectiveness.
Edge Computing Adoption
Edge computing represents a transformative shift in network server deployment strategies. By strategically positioning servers closer to the source of data generation – at the “edge” of the network – edge computing minimizes latency and optimizes bandwidth utilization. This approach is particularly advantageous for applications and devices that demand real-time processing and low latency, such as Internet of Things (IoT) devices, autonomous systems, and real-time analytics platforms. Edge server networking enables faster response times, improved reliability, and more efficient data processing for these latency-sensitive applications.
Improved Scalability and Performance
Modern network servers are engineered for exceptional scalability, enabling organizations to seamlessly expand their server capacity in alignment with their evolving business needs and growth trajectories. Continuous advancements in processor technology, memory architectures, and storage solutions are driving significant improvements in server performance and scalability. These advancements ensure that servers can effectively handle increasing workloads, accommodate growing user bases, and manage expanding data volumes without compromising performance or responsiveness. This inherent adaptability is crucial for businesses to maintain competitiveness and agility in today’s dynamic digital landscape.
Software-Defined Networking (SDN) Integration
Software-defined networking (SDN) is reshaping traditional network management approaches, introducing a more agile and flexible paradigm. By decoupling the network’s control logic from the underlying hardware infrastructure, SDN provides a centralized and programmable approach to network configuration and management. This abstraction empowers network administrators to rapidly adapt to changing network requirements, dynamically allocate resources, and efficiently manage and troubleshoot network issues. SDN enhances network agility, simplifies management, and improves overall network efficiency.
Network Server Features
Network servers are equipped with a comprehensive suite of features specifically designed to address the diverse demands and challenges of network environments. Understanding these features is crucial for appreciating the capabilities and potential applications of network servers in various IT scenarios.
Robust Processing Power
Network servers are built with high-performance processors, often featuring multiple cores and advanced architectures. This substantial processing power is essential for handling concurrent requests from numerous clients, executing complex operations efficiently, and ensuring rapid data processing. The ability to process data swiftly is paramount in high-demand environments such as high-traffic websites, large databases, and computationally intensive applications, guaranteeing seamless operations even under peak loads.
High Memory Capacity
Servers are characterized by their extensive memory capacity, typically measured in gigabytes or terabytes of RAM. This ample memory is critical for efficiently managing multiple concurrent operations, caching frequently accessed data for rapid retrieval, and accommodating large datasets in memory for faster processing. High memory capacity is particularly vital for applications that require real-time data processing, such as online transaction processing systems, in-memory databases, and high-performance computing applications.
Scalability
Scalability is a fundamental characteristic of network servers, referring to their ability to seamlessly adapt to increasing demands by adding resources such as storage capacity, memory, or processing power. This adaptability ensures that organizations can incrementally enhance their server capabilities without requiring disruptive and costly complete system replacements. Scalability provides a cost-effective and flexible approach to handling growing workloads, expanding user bases, and evolving business requirements.
Advanced Security Protocols
Network servers incorporate a wide array of advanced security protocols and mechanisms to protect against cyber threats and safeguard sensitive data. These security features include robust firewalls to control network access and block unauthorized connections, sophisticated encryption algorithms to protect data confidentiality and integrity, and Secure Socket Layer (SSL) and Transport Layer Security (TLS) protocols to secure data transmission over networks. Regular security updates and patches are also essential components of server security, addressing vulnerabilities and maintaining a strong security posture.
Redundancy and Failover Capabilities
Redundancy and failover capabilities are paramount for ensuring continuous operation and minimizing downtime in critical network server environments. Redundancy involves incorporating backup components, such as redundant power supplies, network interfaces, and storage arrays, to mitigate the impact of hardware failures. Failover systems enable servers to automatically switch to redundant components or backup systems in the event of a primary component failure, ensuring uninterrupted service availability.
Remote Management and Monitoring
Remote management tools are indispensable for efficient server administration, allowing administrators to oversee and manage server operations from any location with network connectivity. These tools provide capabilities for monitoring server performance metrics, managing network traffic, diagnosing and troubleshooting issues remotely, and performing routine maintenance tasks. Remote management is particularly valuable for managing geographically distributed servers or servers in remote data centers, reducing the need for on-site personnel and improving operational efficiency.
Virtualization Support
Virtualization support is a key feature in modern network servers, enabling them to host and run multiple virtual servers (virtual machines) on a single physical server. Virtualization maximizes hardware resource utilization, reduces hardware footprint and energy consumption, and provides greater flexibility in managing diverse operating systems and applications. Virtualization simplifies server provisioning, improves resource allocation, and enhances overall server infrastructure efficiency and cost-effectiveness.
Energy Efficiency
Energy efficiency is an increasingly important consideration in network server design and operation, driven by both environmental concerns and cost optimization goals. Modern servers incorporate energy-efficient components, such as low-power processors and memory modules, and implement intelligent power management systems that dynamically adjust energy consumption based on server load. Energy-efficient servers reduce operating costs, minimize environmental impact, and contribute to sustainable IT practices.
How to Set Up a Network Server
Creating a network server involves a systematic process, with each step crucial for ensuring the server’s functionality, security, and seamless integration within a network environment. Here’s a step-by-step guide to setting up a basic network server:
1. Define the Server’s Purpose
The initial step is to clearly define the primary function and intended use of the server. This decision will dictate subsequent choices, from hardware selection to software configuration and security settings. For example, a file server will require ample storage capacity, while a web server will prioritize processing power and network bandwidth to handle web traffic efficiently.
2. Select the Appropriate Hardware
Hardware selection should be carefully aligned with the server’s defined purpose and anticipated workload. Key hardware components to consider include:
- Processor (CPU): Choose a processor with sufficient cores and clock speed to handle the expected processing demands. Faster processors are essential for high-performance tasks and handling concurrent requests.
- Memory (RAM): Ensure adequate RAM capacity to support smooth multitasking, efficient data caching, and the memory requirements of the server operating system and applications.
- Storage (Hard Drives or SSDs): Select storage type and capacity based on storage needs and performance requirements. Traditional Hard Disk Drives (HDDs) offer cost-effective bulk storage, while Solid State Drives (SSDs) provide significantly faster access speeds, improving overall server performance.
- Network Interface Card (NIC): Choose a NIC with appropriate network interface speed and type (e.g., Gigabit Ethernet, 10 Gigabit Ethernet) to match the network infrastructure and bandwidth requirements.
3. Choose the Operating System (OS)
The selection of the server operating system (OS) should be guided by factors such as compatibility with the server’s intended tasks, required security features, ease of administration, and the administrator’s familiarity with the OS. Popular server operating systems include Windows Server, known for its user-friendliness and broad application support, and various Linux distributions, favored for their flexibility, robustness, and open-source nature.
4. Configure Network Settings
Proper network configuration is essential for seamless server integration into the network and reliable communication with clients. Key network settings to configure include:
- Static IP Address: Assign a static IP address to the server to ensure consistent and reliable network identification. This prevents the server’s IP address from changing, which is crucial for stable network services.
- DNS Settings: Configure DNS (Domain Name System) settings to enable network name resolution, allowing clients to access the server using domain names instead of IP addresses.
- Subnet Mask and Gateway: Define the subnet mask and default gateway to ensure the server can communicate correctly within its network segment and with other networks, including the internet.
5. Install and Configure Server Software
Install the necessary server software applications relevant to the server’s defined purpose. For example, for a web server, install web server software such as Apache or Nginx. For a database server, install a database management system like MySQL, PostgreSQL, or SQL Server. Configuration involves setting up user accounts, defining access permissions, configuring operational parameters, and optimizing performance settings based on anticipated workloads and security requirements.
6. Implement Security Measures
Implementing robust security measures is paramount to protect the server and the network from unauthorized access, data breaches, and cyber threats. Essential security measures include:
- Firewall Configuration: Install and configure a firewall to control network traffic, block unauthorized access attempts, and restrict communication to necessary ports and services.
- User Access Control: Implement strong user authentication and access control mechanisms to restrict access to sensitive data and server resources to authorized users only. Utilize strong passwords and multi-factor authentication where possible.
- Data Encryption: Implement encryption for sensitive data both in transit (using protocols like SSL/TLS) and at rest (using disk encryption) to protect data confidentiality.
- Security Updates and Patch Management: Establish a regular schedule for applying security updates and patches to the server operating system and applications to address known vulnerabilities and maintain a secure system.
7. Test the Server Functionality
Thorough testing is essential to verify that the server operates as intended and meets performance and security expectations. Testing should include:
- Functionality Testing: Verify that the server provides the intended services correctly and that clients can access and utilize these services as expected.
- Performance Testing (Load Testing): Conduct load testing to assess server performance under peak conditions and ensure it can handle anticipated workloads without performance degradation.
- Security Testing (Vulnerability Scanning): Perform security testing, including vulnerability scanning, to identify potential security weaknesses and verify that implemented security measures are effective.
8. Regular Maintenance and Monitoring
Ongoing maintenance and monitoring are vital for ensuring long-term server health, stability, and security. Regular maintenance tasks include:
- Performance Monitoring: Continuously monitor server performance metrics (CPU utilization, memory usage, disk I/O, network traffic) to identify potential bottlenecks or performance issues and address them proactively.
- Security Log Review: Regularly review security logs for any suspicious activity, intrusion attempts, or security incidents.
- Software Updates and Patching: Stay vigilant for software updates and security patches and apply them promptly to maintain system security and stability.
- Data Backups: Implement regular data backup procedures to protect against data loss due to hardware failures, software errors, or security incidents. Regularly test backup and recovery processes to ensure data recoverability.
Use Cases of Network Servers
Network servers are incredibly versatile and play a critical role in a wide range of applications across diverse industries. Their adaptability and robust capabilities make them indispensable components of modern computing environments. Here are some prominent use cases of network servers:
- Web Hosting: Network servers are the foundational infrastructure for hosting websites and web applications, serving content to users globally over the internet. They are essential for businesses, organizations, and individuals seeking an online presence.
- File Storage and Sharing: Network servers function as centralized repositories for file storage and sharing within organizations. They facilitate secure and efficient document access, collaboration, and version control, streamlining workflows and enhancing productivity.
- Database Management: Database servers are critical for storing, managing, and providing access to large datasets. They are fundamental in sectors such as banking, healthcare, and retail, enabling fast and reliable data processing, analysis, and reporting for mission-critical applications.
- Email Hosting: Email servers manage the complex processes of email communication, handling the storage, sending, and receiving of emails. They ensure secure and efficient email operations within businesses and organizations, supporting essential communication workflows.
- Application Hosting: Application servers host and run a wide variety of business applications, providing the necessary resources and environment for software like Customer Relationship Management (CRM) systems, Enterprise Resource Planning (ERP) systems, and other business-critical applications to function effectively and be accessed by multiple users.
- Virtualization Infrastructure: Network servers form the backbone of virtualization environments, enabling the creation and management of multiple virtual machines (VMs) on a single physical server. Virtualization optimizes resource utilization, reduces hardware costs, and enhances IT infrastructure agility and scalability.
- Streaming Media Services: Media servers are specialized network servers designed for storing and streaming multimedia content, such as videos, audio, and live broadcasts. They are crucial in the entertainment industry, content delivery networks (CDNs), and online education platforms, enabling efficient and reliable delivery of rich media content.
- Online Gaming Platforms: Gaming servers host multiplayer online games, managing game state, player interactions, and providing a seamless and immersive gaming experience for players worldwide. They require high performance, low latency, and robust security to support demanding online gaming environments.
- E-commerce Transaction Processing: Network servers are essential for processing e-commerce transactions in online retail and e-commerce platforms. They handle user authentication, secure payment processing, order management, and inventory updates, ensuring secure and reliable online shopping experiences.
- Remote Work and Collaboration Support: Network servers play a vital role in supporting remote work and collaboration initiatives. They enable secure Virtual Private Network (VPN) access for remote employees, facilitate file sharing and collaboration, and provide access to essential applications and resources, empowering remote teams and distributed workforces.
Enhancing Network Server Security
Securing network servers is a paramount concern in today’s interconnected digital landscape, where cyber threats are constantly evolving and becoming more sophisticated. Implementing robust security measures is not merely an option but a necessity. Here are detailed strategies for strengthening network server security:
Regular Software Updates and Patch Management
Maintaining up-to-date server software and operating systems is a foundational security practice. This involves diligently installing the latest security patches and updates released by software vendors. These updates often address newly discovered vulnerabilities that malicious actors could exploit. Establishing a proactive and regular schedule for updates and actively monitoring for new patch releases is crucial to ensure servers are protected against known vulnerabilities promptly. Automated patch management systems can significantly streamline this process, ensuring timely and consistent patching across server infrastructure.
Robust Firewall and Intrusion Prevention Systems (IPS)
Implementing a strong firewall is the first line of defense for any network server, acting as a gatekeeper to control network traffic based on pre-defined security rules. Firewalls meticulously examine incoming and outgoing network traffic, blocking unauthorized access attempts and preventing malicious traffic from reaching the server. Intrusion Prevention Systems (IPS) complement firewalls by providing an additional layer of security. IPS continuously monitor network activity for suspicious patterns, malicious behavior, and policy violations. When threats are detected, IPS can automatically take preventative actions, such as blocking malicious traffic or terminating suspicious connections, to mitigate potential security breaches proactively.
Advanced Encryption Techniques
Encryption is a cornerstone of data security, and its application to network servers is critical. Employing robust encryption techniques is essential for protecting sensitive data, both while it is being transmitted across the network and when it is stored on the server. Utilizing secure protocols like SSL/TLS for data transmission encrypts data in transit, rendering it unreadable to eavesdroppers. Encrypting sensitive data at rest, using technologies like disk encryption or database encryption, ensures that even if unauthorized access to the server’s storage occurs, the data remains protected and unintelligible without the decryption key.
Strong Authentication and Access Controls
Enhancing security with strong authentication methods and granular access controls significantly reduces the risk of unauthorized access to network servers. Implementing multi-factor authentication (MFA), which requires users to provide multiple forms of verification (e.g., password and a code from a mobile device), adds a substantial layer of security beyond traditional password-based authentication. Access controls should be rigorously applied based on the principle of least privilege, ensuring that users and applications are granted only the minimum necessary permissions to access server resources. Regularly reviewing and updating access control lists and user permissions is essential to maintain a secure and well-managed access environment.
Regular Security Audits and Vulnerability Assessments
Conducting periodic security audits and vulnerability assessments is a proactive approach to identifying and mitigating potential security weaknesses in network servers. Security audits involve a comprehensive review of server configurations, security policies, and operational practices to ensure adherence to security best practices and compliance standards. Vulnerability assessments utilize automated tools and manual techniques to scan servers for known vulnerabilities, misconfigurations, and security flaws. These assessments provide valuable insights into the server’s security posture, enabling organizations to prioritize remediation efforts and strengthen their defenses. Penetration testing, a more in-depth form of security assessment, simulates real-world cyberattacks to identify exploitable vulnerabilities and evaluate the effectiveness of security controls.
Network Segmentation and Monitoring
Segmenting the network into isolated zones or VLANs (Virtual LANs) is a valuable security strategy. Network segmentation helps contain potential security breaches by limiting the lateral movement of attackers within the network. If one segment is compromised, segmentation can prevent the attacker from easily spreading to other critical parts of the network. Continuous monitoring of network traffic and server logs is crucial for the early detection of unusual activities, anomalies, or potential security threats. Security Information and Event Management (SIEM) systems can automate log collection, analysis, and correlation, providing real-time security monitoring and alerting capabilities.
Anti-Malware and Antivirus Protection
Installing robust anti-malware and antivirus software on network servers is an essential measure to protect against malware infections, viruses, ransomware, and other types of malicious software. Anti-malware software should provide real-time scanning, detection, and removal capabilities to prevent malware from compromising the server. Regular updates to anti-malware software are crucial to ensure it can effectively detect and defend against the latest malware threats. Server-specific anti-malware solutions are often tailored to the unique requirements and workloads of server environments, providing optimized protection without impacting server performance.
Employee Training and Security Awareness Programs
Educating employees and fostering a strong security awareness culture are critical components of a comprehensive cybersecurity strategy. Human error is often a significant factor in security breaches. Regular security awareness training programs can educate staff on security best practices, such as identifying phishing attacks, practicing safe internet usage, handling sensitive data securely, and understanding the importance of security protocols. Empowering employees to recognize and report security threats can significantly reduce the risk of security breaches caused by human error or social engineering attacks.
Backup and Disaster Recovery Planning
Maintaining regular backups of critical server data and having a comprehensive disaster recovery plan are essential for business continuity and data protection. Regular data backups ensure that, in the event of a security breach, system failure, hardware malfunction, or natural disaster, data can be recovered and operations can be resumed with minimal disruption and data loss. A well-defined disaster recovery plan outlines the procedures and steps to be taken to recover from a disaster scenario, including server restoration, data recovery, and business resumption. Regularly testing backup and disaster recovery procedures is crucial to ensure their effectiveness and reliability.
Secure Configuration and Server Hardening
Proper server configuration and hardening are vital steps in minimizing the server’s attack surface and strengthening its security posture. Server hardening involves implementing a range of security configurations and best practices to reduce vulnerabilities and enhance security. This includes disabling unnecessary services and features, closing unused network ports, removing default accounts and passwords, and implementing strong password policies. Regularly reviewing and adjusting server security settings and policies to harden servers against attacks provides an additional layer of security and reduces the likelihood of successful exploitation of vulnerabilities. Security configuration management tools can automate and enforce secure server configurations across server infrastructure.
Conclusion: The Enduring Importance of Network Servers
Network servers are undeniably at the heart of modern digital infrastructure. They are not merely supporting components but are, in fact, indispensable engines that drive data management, facilitate seamless communication, and power the vast array of applications that underpin operations across diverse sectors globally. Their ongoing evolution, characterized by remarkable advancements in virtualization, ever-strengthening security measures, and the transformative integration of AI and machine learning, is leading to server solutions that are not only more efficient and secure but also increasingly intelligent and adaptable.
Looking towards the future, the trajectory of network servers is firmly set on a path of continuous technological advancement, driven by the escalating demands of an increasingly interconnected world. As cyber threats become more sophisticated and persistent, security measures within network servers will undoubtedly evolve in parallel, ensuring robust and proactive protection of sensitive data and upholding network integrity. The relentless proliferation of IoT devices and the growing reliance on remote work solutions will further catalyze innovation in server technologies, spurring the development of new server paradigms and solutions tailored to meet these rapidly emerging demands and shape the future of connected experiences.
To further assist you in managing and securing your data center, we encourage you to explore our comprehensive guides to the best server management software, the best server security tools, and the best server backup software.
