Setting up a RADIUS server is essential for robust network security, and at rental-server.net, we understand its importance. A RADIUS (Remote Authentication Dial-In User Service) server centralizes authentication, authorization, and accounting (AAA) for your network, offering a significant upgrade over less secure methods. Discover how our server rental services can support your RADIUS implementation, enhancing network access control and data protection.
1. What is a RADIUS Server and Why Do I Need One?
A RADIUS server is a network protocol that provides centralized Authentication, Authorization, and Accounting (AAA) management for users who connect to a network service. You need a RADIUS server to enhance security, streamline network access, and gain better control over user activities.
RADIUS, short for Remote Authentication Dial-In User Service, acts as a central authority that verifies users’ identities before granting them access to network resources. According to the National Institute of Standards and Technology (NIST), using a centralized authentication system like RADIUS significantly reduces the risk of unauthorized access. Without RADIUS, managing user authentication across multiple access points can be cumbersome and less secure, especially when relying on methods like pre-shared keys (PSKs).
1.1. Key Benefits of Implementing a RADIUS Server
Implementing a RADIUS server offers several advantages:
-
Enhanced Security: RADIUS uses strong encryption to protect credentials during transmission, reducing the risk of interception and misuse.
-
Centralized Management: RADIUS simplifies user management by providing a single point to control access policies and permissions.
-
Detailed Accounting: RADIUS tracks network usage, providing valuable insights for billing, auditing, and resource allocation.
-
Scalability: RADIUS can handle a large number of users and devices, making it suitable for growing networks.
1.2. PSK Authentication vs. RADIUS: Understanding the Security Difference
Pre-Shared Key (PSK) authentication is simpler to set up but lacks the security depth of RADIUS. A PSK network relies on a single password shared among all users, making it vulnerable to attacks if compromised.
| Feature | PSK Authentication | RADIUS Authentication |
|---|---|---|
| Security Level | Low | High |
| Management | Decentralized, difficult to manage multiple users | Centralized, easy to manage user access and permissions |
| Scalability | Poor, not suitable for large networks | Excellent, suitable for large and growing networks |
| Vulnerabilities | Susceptible to password sharing and credential theft | Resistant to credential theft due to encryption and auditing |
| Credential Abuse | High Risk | Significantly Reduced Risk |
According to a Forbes report, 74% of data breaches start with privileged credential abuse, a risk significantly mitigated by using RADIUS authentication.
1.3. How RADIUS Prevents Private Information Leakage
RADIUS eliminates the risk of private information leakage by enabling individual users to authenticate with unique credentials. Unlike PSK, where a single compromised password exposes the entire network, RADIUS ensures that each user has their own secure login.
This approach enhances security because:
- Unique Credentials: Each user has a unique username and password, reducing the risk of widespread compromise.
- Encrypted Transmission: RADIUS encrypts authentication data, protecting it from eavesdropping.
- Access Control: RADIUS allows granular control over user permissions, ensuring that users only access resources they need.
2. Can I Use Windows Server as a RADIUS Server?
Yes, you can use Windows Server as a RADIUS server by leveraging the Network Policy Server (NPS) role. NPS provides the necessary functionality to implement RADIUS authentication within a Windows environment.
Windows Server includes Network Policy Server (NPS), which can act as a RADIUS server. NPS allows you to create access policies for connection requests and configure Network Access Servers (NAS) to forward these requests to remote RADIUS servers, which aids in load balancing. Before investing in third-party RADIUS solutions, consider NPS as a cost-effective option.
2.1. Understanding Network Policy Server (NPS)
NPS performs Authentication, Authorization, and Accounting (AAA) services for various connection requests:
- Wireless Networks
- Virtual Private Networks (VPN)
- 802.1x Switches
- Dial-up Connections
- Router-to-Router Connections
NPS is designed for on-premise infrastructure, which may not suit organizations seeking cloud solutions or those with non-Windows environments. Compatibility with cloud computing is crucial for long-term viability in today’s IT landscape.
2.2. Limitations of NPS in Modern Network Environments
While NPS is a viable option for Windows-centric environments, it has limitations:
- On-Premise Dependency: NPS is designed for on-premise infrastructure, making it less suitable for cloud-based or hybrid environments.
- Cloud Incompatibility: NPS does not natively integrate with cloud directories like Azure AD without workarounds, limiting its use in modern cloud-first organizations.
- Platform Restrictions: NPS is primarily a Windows solution, which may not blend well in mixed-OS environments.
2.3. Scenarios Where NPS is a Suitable RADIUS Solution
Despite its limitations, NPS can be a suitable RADIUS solution in specific scenarios:
- Small to Medium-Sized Businesses: If your organization has a predominantly Windows-based network and doesn’t require extensive cloud integration, NPS can be a cost-effective option.
- On-Premise Networks: For networks that are entirely on-premise and have no plans to migrate to the cloud, NPS provides a straightforward RADIUS solution.
- Basic Authentication Needs: If your authentication needs are simple and don’t require advanced features like multi-factor authentication or granular access control, NPS can suffice.
3. What are the Prerequisites for Configuring a Microsoft RADIUS Server?
Before configuring a Microsoft RADIUS Server, ensure you have the following prerequisites:
- Windows Server 2022 Installed
- Windows Server 2022 Desktop Experience Enabled
- Devices that Support WPA2-Enterprise
- An Activated Domain Controller for Windows
- Active Directory Installed on Your Windows Server
- NPS Role Installed
These prerequisites ensure that your environment is properly set up to support RADIUS authentication using NPS.
3.1. Detailed Breakdown of Each Prerequisite
To successfully configure a Microsoft RADIUS server, each prerequisite must be carefully addressed:
- Windows Server 2022 Installation: The base operating system must be installed and running smoothly. Ensure it is properly licensed and activated.
- Windows Server 2022 Desktop Experience Enabled: The Desktop Experience provides the graphical user interface necessary for managing the server. This feature is required to access the NPS configuration tools.
- Devices that Support WPA2-Enterprise: Your network devices (e.g., Wi-Fi access points, switches) must support the WPA2-Enterprise security protocol, which is essential for RADIUS authentication.
- An Activated Domain Controller for Windows: The Domain Controller manages user accounts and authentication policies. It must be active and properly configured to integrate with NPS.
- Active Directory Installed on Your Windows Server: Active Directory (AD) stores user credentials and group memberships. NPS relies on AD for user authentication.
- NPS Role Installed: The Network Policy Server role provides the RADIUS server functionality. It must be installed through the Server Manager console.
3.2. Why are These Prerequisites Important?
These prerequisites are crucial for the following reasons:
- Compatibility: Ensures all components work together seamlessly.
- Security: Provides a secure foundation for RADIUS authentication.
- Functionality: Enables all necessary features for managing network access.
- Stability: Reduces the risk of errors and downtime.
3.3. Steps to Verify Each Prerequisite
Before proceeding with the RADIUS server configuration, verify that each prerequisite is met:
- Windows Server 2022 Installation:
- Check the server’s system information to confirm the correct version is installed.
- Verify that the server is activated with a valid license.
- Windows Server 2022 Desktop Experience Enabled:
- Ensure you can access the graphical user interface and Server Manager console.
- If not enabled, install the Desktop Experience feature through Server Manager.
- Devices that Support WPA2-Enterprise:
- Consult the documentation for your network devices to confirm WPA2-Enterprise support.
- Update the firmware of your devices if necessary.
- An Activated Domain Controller for Windows:
- Check the Domain Controller status in Server Manager.
- Ensure the Domain Controller is functioning correctly and replicating with other domain controllers if applicable.
- Active Directory Installed on Your Windows Server:
- Verify that the Active Directory Domain Services role is installed in Server Manager.
- Check that you can manage users and groups through the Active Directory Users and Computers console.
- NPS Role Installed:
- Confirm that the Network Policy Server role is installed in Server Manager.
- Access the NPS console to verify its functionality.
4. How to Set Up a Microsoft RADIUS Server: A Step-by-Step Guide
Setting up a Microsoft RADIUS Server involves creating a new group on Active Directory, adding the Network Policy and Access Services role, and configuring RADIUS using NPS. Follow these steps to configure your RADIUS server effectively.
4.1. Step 1 – Create a New Group on Active Directory (AD)
To manage users who will authenticate through the RADIUS server, create a new group in Active Directory:
- Open Active Directory Users and Computers:
- Click on Tools in Server Manager and select Active Directory Users and Computers.
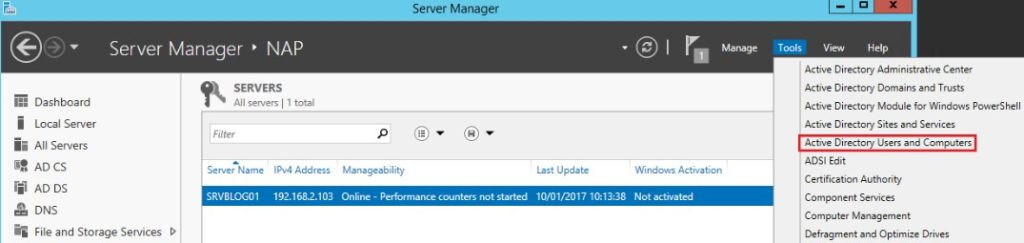 Active Directory Users and Computers
Active Directory Users and Computers
- Click on Tools in Server Manager and select Active Directory Users and Computers.
- Create a New Group:
- Right-click on Users, select New, and choose Group.
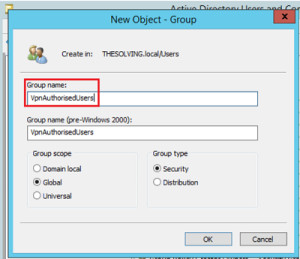 Create New Group
Create New Group
- Right-click on Users, select New, and choose Group.
- Name the AD Group:
- Enter a name for the group under Group name (e.g., RADIUS_Users).
- Add Users to the Group:
- Right-click on the user you want to authenticate through the new group.
- Select Add to a group.
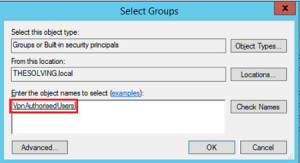 Add User to Group
Add User to Group
- Select the Newly Created Group:
- Enter the name of the group (e.g., RADIUS_Users) and click OK.
4.2. Step 2 – Add Network Policy and Access Services Role
To enable RADIUS server functionality, add the Network Policy and Access Services role:
- Open Add Roles and Features Wizard:
- In Server Manager, click Add roles and features.
- Select Installation Type:
- Choose Role-based or feature-based installation.
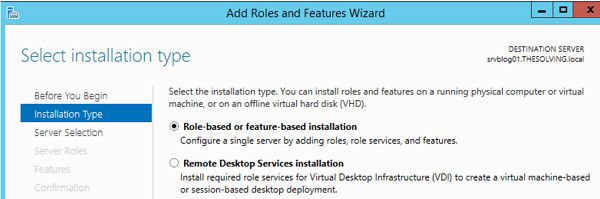 Select Installation Type
Select Installation Type
- Choose Role-based or feature-based installation.
- Select Server:
- Select the server where you want to install the role.
- Add Network Policy and Access Services:
- Check the box next to Network Policy and Access Services.
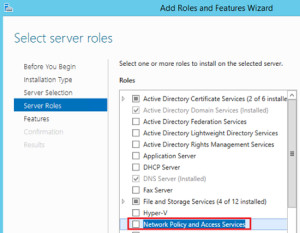 Add Network Policy and Access Services
Add Network Policy and Access Services
- Check the box next to Network Policy and Access Services.
- Add Role Services:
- Select Network Policy Server.
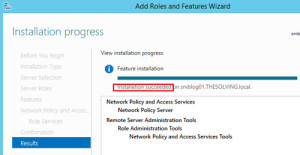 Select Network Policy Server
Select Network Policy Server
- Select Network Policy Server.
- Confirm and Finish Installation:
- Click Next through the remaining screens and then click Install.
4.3. Step 3 – Configure RADIUS Using NPS
To configure RADIUS using NPS, follow these steps:
- Open Network Policy Server:
- Select Network Policy Server from the Tools menu in Server Manager.
- Register NPS in Active Directory:
- Right-click NPS (Local) and select Register Server in Active Directory.
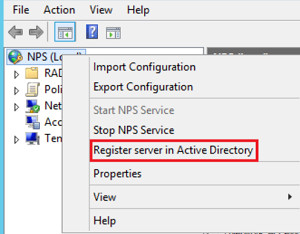 Register NPS in AD
Register NPS in AD
- Right-click NPS (Local) and select Register Server in Active Directory.
- Create a New RADIUS Client:
- Expand RADIUS Clients and Servers, right-click on RADIUS Clients, and select New.
- Configure RADIUS Client Settings:
- Friendly name: Enter a name for the RADIUS client (e.g., AccessPoint01).
- Address (IP or DNS): Enter the IP address of the device that will forward authentication requests to the RADIUS server.
- Shared secret: Enter a password for the network (this will be used as the shared secret between the RADIUS server and the client).
 Configure RADIUS Client
Configure RADIUS Client
- Configure Network Policies:
- Navigate to Policies and select Network Policies.
- Create a new policy or modify the default policy to match your network requirements.
5. What are the Security Concerns with Microsoft RADIUS?
Microsoft RADIUS, while functional, has security concerns, particularly with shared secrets. Shared secrets are vulnerable to attacks, and the lack of a revocation mechanism poses a significant risk.
5.1. Vulnerabilities of Shared Secrets
Shared secrets, a common method for authenticating clients in RADIUS, have inherent vulnerabilities:
- Weak Authentication: Shared secrets are a weak form of authentication security.
- Keypair Copying: The server generates a keypair that is copied to every client machine, making it susceptible to compromise.
- Private Key Harvesting: An attacker can easily harvest the server’s private key and impersonate an authenticated server.
5.2. Lack of Revocation Mechanism
The absence of a revocation mechanism in pre-shared secrets is a major security flaw. Once a secret is compromised, there is no way to prevent an attacker from using it.
This means:
- No Immediate Protection: If a shared secret is compromised, the network remains vulnerable until the secret is manually changed on all clients.
- Increased Risk of Data Breaches: Attackers can exploit compromised secrets to gain unauthorized access to sensitive data.
- Administrative Overhead: Manually managing and updating shared secrets across multiple devices is time-consuming and error-prone.
5.3. The Superior Security of Digital Certificates
Digital certificates offer superior security compared to shared secrets:
- Strong Authentication: Certificates provide a more robust form of authentication, reducing the risk of impersonation.
- Certificate Revocation Lists (CRL): RADIUS servers check CRLs to ensure certificates are not revoked or expired.
- Immediate Revocation: If a certificate is compromised, it can be added to the CRL, immediately preventing further use.
According to security experts, digital certificates provide a more secure and manageable authentication solution for RADIUS deployments.
6. How Can Cloud RADIUS Replace Microsoft RADIUS Server?
Cloud RADIUS offers a robust replacement for Microsoft RADIUS Server by providing enhanced security, cloud integration, and scalability. Cloud RADIUS solutions like SecureW2 bridge the gap between on-premise and cloud environments, offering a seamless and secure authentication experience.
6.1. Limitations of On-Premise Infrastructure
On-premise infrastructures, like those relying on Microsoft RADIUS Server, have inherent vulnerabilities:
- Physical Security Risks: On-premise servers are vulnerable to intruders and physical disasters.
- Zero-Day Attacks: A significant percentage of successful cybersecurity breaches stem from zero-day attacks.
- Maintenance Costs: Maintaining on-premise servers requires significant resources, including hardware, software, and IT staff.
6.2. Advantages of Cloud RADIUS
Cloud RADIUS networks are typically better protected and more resilient than on-premise counterparts:
- Enhanced Security: Cloud providers invest heavily in security measures, protecting against a wide range of threats.
- High Availability: Cloud RADIUS solutions offer high availability and redundancy, minimizing downtime.
- Scalability: Cloud RADIUS can easily scale to accommodate growing network demands.
- Cost-Effectiveness: Cloud RADIUS eliminates the need for expensive hardware and reduces IT maintenance costs.
6.3. Integration with Cloud Directories
Cloud RADIUS seamlessly integrates with cloud directories like Azure AD, simplifying user management and enhancing security:
- Native Integration: Cloud RADIUS solutions are designed to work seamlessly with cloud directories, eliminating the need for workarounds.
- Centralized Management: User accounts and access policies can be managed centrally through the cloud directory.
- Improved Security: Cloud RADIUS leverages the security features of cloud directories, such as multi-factor authentication and conditional access policies.
7. How Do I Migrate to Cloud RADIUS Using Azure?
Migrating to Cloud RADIUS using Azure involves integrating SecureW2’s RADIUS and Managed PKI Services with Azure AD. This turnkey solution bridges the gap between on-premise and cloud environments, providing a seamless and secure authentication experience.
7.1. Understanding SecureW2’s RADIUS and Managed PKI Services
SecureW2 offers a comprehensive suite of services for migrating to Cloud RADIUS:
- Cloud RADIUS: Provides a secure and scalable RADIUS solution hosted in the cloud.
- Managed PKI: Simplifies the management of digital certificates, ensuring strong authentication.
- Integration with Azure AD: Seamlessly integrates with Azure AD for centralized user management and authentication.
7.2. Step-by-Step Migration Process
The migration process typically involves the following steps:
- Assessment:
- Evaluate your existing network infrastructure and authentication requirements.
- Planning:
- Develop a migration plan that outlines the steps, timelines, and resources required.
- Configuration:
- Configure SecureW2’s RADIUS and Managed PKI Services to integrate with Azure AD.
- Testing:
- Test the new Cloud RADIUS solution to ensure it meets your security and performance requirements.
- Deployment:
- Deploy the Cloud RADIUS solution to your production network.
- Monitoring:
- Monitor the performance and security of the Cloud RADIUS solution to ensure it continues to meet your needs.
7.3. Benefits of Using SecureW2 for Cloud RADIUS Migration
Using SecureW2 for Cloud RADIUS migration offers several benefits:
- Simplified Migration: SecureW2 provides a turnkey solution that simplifies the migration process.
- Enhanced Security: SecureW2’s RADIUS and Managed PKI Services provide robust security features.
- Seamless Integration: SecureW2 seamlessly integrates with Azure AD, minimizing disruption to your existing infrastructure.
- Cost-Effective: SecureW2 eliminates the need for expensive hardware and reduces IT maintenance costs.
8. What are the Key Considerations for Choosing a RADIUS Server Solution?
Choosing the right RADIUS server solution requires careful consideration of security, scalability, integration capabilities, and cost. Evaluate your specific needs and choose a solution that aligns with your organization’s requirements.
8.1. Security Requirements
Security is paramount when selecting a RADIUS server solution. Consider the following:
- Encryption: Ensure the solution uses strong encryption algorithms to protect authentication data.
- Authentication Methods: Evaluate the authentication methods supported by the solution, such as digital certificates and multi-factor authentication.
- Compliance: Ensure the solution meets relevant compliance standards, such as PCI DSS and HIPAA.
8.2. Scalability and Performance
Choose a solution that can scale to accommodate your growing network demands:
- Capacity: Ensure the solution can handle the number of users and devices on your network.
- Performance: Evaluate the solution’s performance under load to ensure it can handle peak traffic.
- Redundancy: Choose a solution that offers redundancy and high availability to minimize downtime.
8.3. Integration Capabilities
Seamless integration with your existing infrastructure is crucial:
- Directory Services: Ensure the solution integrates with your directory services, such as Active Directory or Azure AD.
- Network Devices: Verify that the solution is compatible with your network devices, such as Wi-Fi access points and switches.
- Cloud Services: Choose a solution that integrates with your cloud services, such as Azure and AWS.
8.4. Cost Considerations
Evaluate the total cost of ownership (TCO) of the RADIUS server solution:
- Licensing Fees: Consider the licensing fees for the solution.
- Hardware Costs: Evaluate the hardware costs associated with the solution, such as servers and network devices.
- Maintenance Costs: Consider the maintenance costs, including software updates, security patches, and IT support.
9. How Can rental-server.net Help with Your RADIUS Server Needs?
At rental-server.net, we offer a range of server solutions that can support your RADIUS server implementation. Our dedicated servers, VPS, and cloud servers provide the performance, reliability, and security you need to run your RADIUS server effectively.
9.1. Server Options for RADIUS Implementation
We offer several server options to suit your specific needs:
- Dedicated Servers: Provide maximum performance and control for demanding RADIUS deployments.
- Virtual Private Servers (VPS): Offer a cost-effective solution for smaller networks and testing environments.
- Cloud Servers: Provide scalability and flexibility for growing networks.
9.2. Benefits of Choosing rental-server.net
Choosing rental-server.net offers several advantages:
- Reliable Infrastructure: Our servers are housed in state-of-the-art data centers, ensuring high availability and performance.
- Scalable Resources: Easily scale your server resources to accommodate growing network demands.
- Dedicated Support: Our expert support team is available 24/7 to assist with any issues.
- Competitive Pricing: We offer competitive pricing on all our server solutions.
9.3. Case Studies and Success Stories
Many organizations have successfully implemented RADIUS servers using our server solutions. Contact us to learn more about our case studies and success stories.
10. Frequently Asked Questions (FAQ) About RADIUS Servers
Here are some frequently asked questions about RADIUS servers:
- What is the main purpose of a RADIUS server?
- The main purpose of a RADIUS server is to centralize authentication, authorization, and accounting (AAA) for network access.
- Is RADIUS more secure than PSK?
- Yes, RADIUS is significantly more secure than PSK because it uses individual credentials and encryption.
- Can I use Windows Server as a RADIUS server?
- Yes, you can use Windows Server as a RADIUS server by leveraging the Network Policy Server (NPS) role.
- What are the limitations of NPS?
- NPS is designed for on-premise infrastructure and lacks native integration with cloud directories.
- What is Cloud RADIUS?
- Cloud RADIUS is a RADIUS solution hosted in the cloud, offering enhanced security, scalability, and integration capabilities.
- How do I migrate to Cloud RADIUS?
- You can migrate to Cloud RADIUS by integrating SecureW2’s RADIUS and Managed PKI Services with Azure AD.
- What are the benefits of using digital certificates with RADIUS?
- Digital certificates offer stronger authentication, certificate revocation lists, and immediate revocation capabilities.
- What are the key considerations for choosing a RADIUS server solution?
- Key considerations include security, scalability, integration capabilities, and cost.
- How can rental-server.net help with my RADIUS server needs?
- rental-server.net offers a range of server solutions, including dedicated servers, VPS, and cloud servers, to support your RADIUS server implementation.
- What is the cost of implementing a RADIUS server?
- The cost varies depending on the solution and your specific needs. Contact us for a personalized quote.
Implementing a RADIUS server is a critical step in securing your network. At rental-server.net, we provide the server solutions and expertise you need to deploy and manage your RADIUS server effectively. Explore our server options, compare pricing, and find the perfect solution for your organization. Contact us today to learn more and get started. Visit rental-server.net or call us at +1 (703) 435-2000 to discover how we can help you enhance your network security. Our address is 21710 Ashbrook Place, Suite 100, Ashburn, VA 20147, United States.
