As a content creator for rental-server.net, I specialize in making complex server technologies accessible and understandable. In this article, we’ll dive into a crucial aspect of securing your applications with Duende Identity Server: configuring Client Redirect URLs. While our previous discussions may have touched upon authentication flows like Resource Owner Password Credentials (ROPC), here, we’re focusing specifically on how to manage and insert records for ClientRedirectUris within your Duende Identity Server setup. This is vital for ensuring that your OAuth 2.0 and OpenID Connect flows are secure and function as expected.
Understanding Client Redirect URLs in Duende Identity Server
Client Redirect URLs, or ClientRedirectUris, are a fundamental security component in OAuth 2.0 and OpenID Connect protocols, and thus in Duende Identity Server. They serve as approved destinations where the Identity Server can redirect users after successful authentication or authorization. Think of them as a pre-approved list of addresses where the authorization server is permitted to send users back to your application.
Why are they important?
Imagine a scenario without properly configured redirect URLs. After a user successfully authenticates with the Identity Server, a malicious application could intercept the authorization code or access token by manipulating the redirect URL. By strictly defining ClientRedirectUris, you prevent this type of open redirect vulnerability, ensuring that the Identity Server only redirects back to trusted locations.
In essence, ClientRedirectUris are a critical safeguard against unauthorized access and data breaches, forming a cornerstone of secure authentication workflows with Duende Identity Server.
Methods to Insert and Manage Client Redirect URLs
Duende Identity Server offers flexible ways to manage ClientRedirectUris. The method you choose often depends on your environment, scale, and how you manage your overall Identity Server configuration. Here are the primary approaches:
-
Configuration Files (e.g., Config.cs): For development, testing, and smaller deployments, configuring clients and their
ClientRedirectUrisdirectly in code, such as within aConfig.csfile, is common and straightforward. This is the approach demonstrated in the original article for defining client configurations. You “insert” or define these URLs as part of the client’s static configuration.new Client { ClientId = "your_client_id", ClientName = "Your Application Name", RedirectUris = new List<string> { "https://localhost:3000/signin-oidc", // Example Redirect URI "https://yourapp.com/callback" // Another valid Redirect URI }, // ... other client configurations }In this method, you are essentially hardcoding the
ClientRedirectUris. While easy for initial setup, it might not be ideal for production environments where you need more dynamic management. -
Database Configuration: For larger, production-scale Identity Server deployments, storing client configurations, including
ClientRedirectUris, in a database is highly recommended. Duende Identity Server is designed to work seamlessly with databases. This approach offers several advantages:- Dynamic Management: You can add, modify, or remove
ClientRedirectUriswithout redeploying your Identity Server. This is crucial for handling changes in your application landscape. - Centralized Configuration: A database provides a single source of truth for all client configurations, making management and auditing easier.
- Scalability: Database-backed configuration scales much better for handling numerous clients and complex setups.
To “insert records” into the database for
ClientRedirectUris, you would typically interact with the database context provided by Duende Identity Server. This might involve using Entity Framework Core migrations to set up the database schema initially, and then using the DbContext to add or updateCliententities and their associatedRedirectUris.While direct SQL insertion is possible, it’s generally discouraged. Using the provided APIs and ORM (Entity Framework Core) ensures data integrity and consistency with Duende Identity Server’s internal data models.
- Dynamic Management: You can add, modify, or remove
-
Admin UI (If Provided): Some implementations or extensions of Duende Identity Server might offer an Admin UI. If available, this UI often provides a user-friendly interface to manage clients and their configurations, including adding and modifying
ClientRedirectUriswithout directly touching code or the database. This is the most user-friendly approach for operational tasks.
Choosing the Right Method:
- Development/Testing: Configuration files are perfectly acceptable for simplicity.
- Production (Small to Medium Scale): Database configuration is strongly recommended for manageability and scalability.
- Production (Large Scale with Operations Teams): Database configuration with an Admin UI (if available) offers the best balance of control and ease of use.
Example: Configuring Client Redirect URLs in Config.cs (Code-Based)
Let’s revisit the Config.cs example, expanding on how ClientRedirectUris are defined within the client configuration. This approach is excellent for understanding the fundamental structure.
// Config.cs
public static IEnumerable<Client> Clients =>
new List<Client>
{
new Client
{
ClientId = "nextjs_web_app",
ClientName = "NextJs Web App",
ClientSecrets = { new Secret("secret".Sha256()) },
AllowedGrantTypes = GrantTypes.Code, // Or GrantTypes.ResourceOwnerPassword for ROPC
RequireClientSecret = false,
AllowOfflineAccess = true,
RedirectUris = new List<string>
{
"http://localhost:3000/api/auth/callback/sample-identity-server", // Callback for Authorization Code Flow
"http://localhost:3000/login/callback" // Another potential callback URI
},
PostLogoutRedirectUris = { "http://localhost:3000" },
AllowedCorsOrigins= { "http://localhost:3000" },
AllowedScopes = new List<string>
{
IdentityServerConstants.StandardScopes.OpenId,
IdentityServerConstants.StandardScopes.Profile,
"SampleAPI"
}
}
};Explanation:
-
RedirectUris: This property is a list of strings. Each string represents a valid redirect URL for this client (nextjs_web_app). -
Adding a new Redirect URL: To “insert a record,” you simply add a new string to this list. For example, if your Next.js application adds a new authentication callback path, you would add it here:
RedirectUris = new List<string> { "http://localhost:3000/api/auth/callback/sample-identity-server", "http://localhost:3000/login/callback", "http://localhost:3000/another/callback/path" // New Redirect URI added },
Important Considerations for ClientRedirectUris:
- Exact Match: Duende Identity Server typically requires an exact match between the redirect URI sent by the client during the authorization request and one of the configured
ClientRedirectUris. Ensure accuracy. - Scheme and Authority: Include the scheme (e.g.,
http://orhttps://) and authority (domain and port) in your URLs. - Path: Be precise with the path. If your callback is at
/api/auth/callback, configure exactly that, not just/api/auth/. - Security (HTTPS): In production, always use
https://for your redirect URLs to encrypt communication and prevent interception of sensitive data.http://localhostis acceptable for local development.
Client Redirect URLs in the Context of ROPC and Other Flows
While the original article focused on ROPC, it’s important to note that ClientRedirectUris are primarily used with flows that involve redirects, such as:
- Authorization Code Flow: This is the most common and recommended flow for web applications and SPAs.
ClientRedirectUrisare essential for this flow. - Hybrid Flow: A combination of Authorization Code and Implicit flows, also relying on redirects and thus
ClientRedirectUris. - Implicit Flow (Generally Discouraged): While redirect-based, the Implicit flow has security drawbacks and is less common now.
ROPC (Resource Owner Password Credentials) Flow: Interestingly, the ROPC flow, as demonstrated in the original article, does not directly utilize ClientRedirectUris. ROPC is a direct credential exchange; the client sends the username and password directly to the Identity Server’s token endpoint. The server validates these credentials and, if valid, directly returns tokens to the client. There’s no redirection involved in the core ROPC flow itself.
However, even if you are using ROPC in some parts of your system (and understand its security implications and deprecation warnings), you will likely still be using redirect-based flows (like Authorization Code Flow) for other clients or scenarios within your overall application ecosystem. Therefore, understanding and correctly configuring ClientRedirectUris remains crucial, even if not directly relevant to ROPC in isolation.
Security Best Practices for Client Redirect URLs
- Use HTTPS in Production: Always use
https://for production redirect URLs. - Avoid Wildcards: Be as specific as possible with your redirect URIs. Avoid wildcard entries if possible, as they can broaden the attack surface.
- Regularly Review and Audit: Periodically review your configured
ClientRedirectUristo ensure they are still valid and necessary. Remove any that are no longer in use. - Protect Configuration: Secure your configuration files or database where
ClientRedirectUrisare stored to prevent unauthorized modifications.
Conclusion
Correctly configuring ClientRedirectUris in Duende Identity Server is a fundamental security practice. Whether you are “inserting records” via code, database interactions, or an Admin UI, understanding their purpose and adhering to security best practices is paramount. By properly managing these URLs, you significantly strengthen the security posture of your applications that rely on Duende Identity Server for authentication and authorization.
For deeper insights and advanced configurations, always refer to the official Duende Identity Server documentation. Secure configurations are the foundation of trustworthy applications.
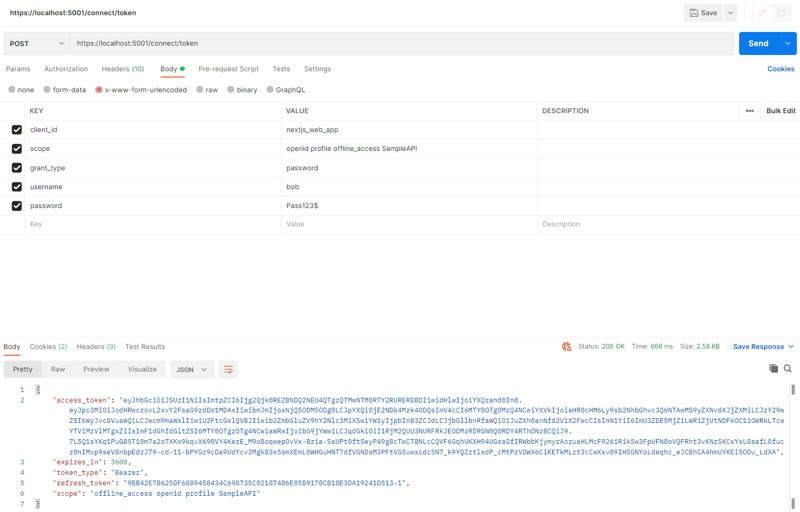 Postman Get Token
Postman Get Token
 NextAuth.js default Sign-in page
NextAuth.js default Sign-in page

