Finding the port number of a server is essential for effective server management and network communication. This guide will explore how to identify port numbers, their significance, and how rental-server.net can assist you in optimizing your server infrastructure. Let’s dive in and discover how to find and manage those crucial port numbers.
1. What Is a Port Number and Why Is It Important?
A port number is a numerical identifier that specifies a particular process or application on a server. Port numbers allow network devices to direct traffic to the correct service running on a server. This is essential for ensuring data reaches the intended application. Think of it like apartment numbers in a building where the IP address is the building’s street address.
Understanding Port Numbers in Detail
Port numbers are 16-bit integers, ranging from 0 to 65535. The Internet Assigned Numbers Authority (IANA) manages these numbers. These numbers are categorized into three ranges:
- Well-Known Ports (0-1023): Reserved for common services and applications like HTTP (port 80) and HTTPS (port 443).
- Registered Ports (1024-49151): Assigned to specific applications or vendors for their unique services.
- Dynamic or Private Ports (49152-65535): Used for temporary connections and can be utilized by any application.
Using the correct port number is crucial for establishing connections and ensuring data is routed to the appropriate service on a server.
Why Port Numbers Matter
- Service Identification: Port numbers enable servers to differentiate between various services running simultaneously.
- Network Communication: They facilitate accurate routing of data packets across networks.
- Security: Properly configured ports and firewalls protect servers from unauthorized access and potential threats.
2. How Do IP Addresses and Port Numbers Work Together?
An IP address identifies a specific device on a network, while a port number identifies a particular application or service on that device. The IP address gets the data packet to the correct machine, and the port number directs it to the correct application. Together, they ensure efficient and accurate data delivery.
The Analogy of IP Addresses and Port Numbers
Imagine an IP address as a street address and a port number as an apartment number within that building. When a letter (data packet) arrives at a building (server), the street address (IP address) guides it to the correct location. The apartment number (port number) ensures the letter reaches the intended recipient (application).
Detailed Explanation
- IP Address: A unique identifier assigned to each device connected to a network, enabling devices to communicate with each other.
- Port Number: A 16-bit number that specifies a particular application or service on a device.
When a client sends a request to a server, it includes both the server’s IP address and the port number of the service it wants to access. The server uses this information to route the request to the correct application.
3. What Are the Different Types of Port Numbers and Their Uses?
Understanding the different types of port numbers is essential for configuring servers and network devices effectively. The IANA categorizes port numbers into three main ranges, each with its specific purpose.
Well-Known Ports (0-1023)
These ports are reserved for common services and applications. They are standardized to ensure compatibility across different systems. Examples include:
- Port 20 and 21: File Transfer Protocol (FTP) for data transmission.
- Port 22: Secure Shell (SSH) for secure remote access.
- Port 25: Simple Mail Transfer Protocol (SMTP) for sending emails.
- Port 53: Domain Name System (DNS) for domain name resolution.
- Port 80: Hypertext Transfer Protocol (HTTP) for web traffic.
- Port 110: Post Office Protocol version 3 (POP3) for receiving emails.
- Port 143: Internet Message Access Protocol (IMAP) for managing emails.
- Port 443: Hypertext Transfer Protocol Secure (HTTPS) for secure web traffic.
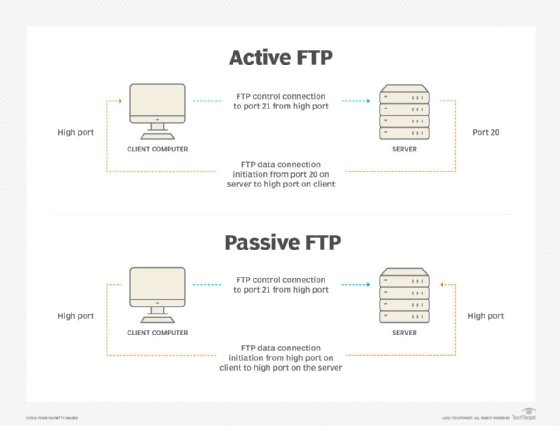 Active FTP and passive FTP diagram.
Active FTP and passive FTP diagram.
Registered Ports (1024-49151)
These ports are assigned to specific applications or vendors. Software companies often register these ports for their unique services to avoid conflicts. Examples include:
- Port 1433: Microsoft SQL Server for database services.
- Port 3306: MySQL for database management.
- Port 3389: Remote Desktop Protocol (RDP) for remote access to Windows systems.
- Port 5060: Session Initiation Protocol (SIP) for VoIP communications.
Dynamic or Private Ports (49152-65535)
These ports are used for temporary connections and can be utilized by any application. They are often assigned dynamically by the operating system for client-side communication. These ports are also known as ephemeral ports.
Temporary Port Numbers
In certain scenarios, a port number can be assigned temporarily for the duration of a request and its completion. This is known as a temporary port number. These ports are usually chosen from the dynamic port range.
4. How To Find The Port Number Of A Server?
Finding the port number of a server depends on the operating system and the specific service you are trying to identify. Here are some common methods:
Using Command-Line Tools
The command line provides powerful tools for identifying open ports and the services using them.
For Windows
- Open Command Prompt: Press
Win + R, typecmd, and press Enter. - Use the
netstatcommand: Typenetstat -anoand press Enter. This command displays all active network connections and listening ports. - Identify the Port Number: Look for the port number in the “Local Address” column. The
-aoption shows all connections and listening ports,-ndisplays addresses and port numbers in numerical form, and-oshows the process identifier (PID) associated with each connection. - Find the Associated Process: Use the Task Manager to find the process associated with the PID. Press
Ctrl + Shift + Escto open Task Manager, go to the “Details” tab, and find the PID in the “PID” column.
For macOS and Linux
- Open Terminal: You can find it in Applications/Utilities/Terminal.
- Use the
netstatcommand: Typenetstat -an | grep LISTENand press Enter. This command lists all listening ports. - Identify the Port Number: Look for the port number in the “Local Address” column.
- Use the
lsofcommand: Alternatively, you can uselsof -i :[port number]to find the process listening on a specific port. Replace[port number]with the actual port number.
Using Graphical User Interfaces (GUIs)
GUIs provide a more user-friendly way to find port numbers.
Windows Resource Monitor
- Open Resource Monitor: Press
Win + R, typeresmon, and press Enter. - Go to the “Network” tab: Here, you can see the processes that are actively using network connections and the associated port numbers.
- Identify the Port Number: Look for the port number in the “Listening Ports” section.
macOS Network Utility
- Open Network Utility: You can find it in Applications/Utilities/Network Utility.
- Select the “Port Scan” tab: Enter the IP address of the server and specify the port range you want to scan.
- Start the Scan: Click the “Scan” button to see the open ports.
Using Third-Party Port Scanning Tools
Several third-party tools can help you scan for open ports on a server. These tools often provide more advanced features and a user-friendly interface.
Nmap (Network Mapper)
Nmap is a powerful and versatile port scanning tool available for Windows, macOS, and Linux.
- Download and Install Nmap: You can download it from the official Nmap website.
- Run Nmap: Open the command line or terminal and type
nmap [IP address]. Replace[IP address]with the IP address of the server you want to scan. - Interpret the Results: Nmap will display a list of open ports and the services running on them.
Advanced Port Scanner
Advanced Port Scanner is a free and easy-to-use port scanner for Windows.
- Download and Install Advanced Port Scanner: You can download it from the official website.
- Run Advanced Port Scanner: Enter the IP address range you want to scan and click “Start Scan.”
- Interpret the Results: The tool will display a list of open ports and the services running on them.
5. What Are Open Ports and Port Scanning?
An open port is a port number that is actively listening for incoming connections. When a program wants to receive communication over a network, it registers with the system network process to open a port number.
Understanding Open Ports
- Listening State: An open port indicates that a service or application is ready to accept connections on that port.
- Security Implications: Open ports can be potential entry points for attackers if not properly secured.
Port Scanning Explained
Port scanning is the process of checking every port number on an IP address or range to see if it responds. It is a common method used by network administrators to identify open ports and potential vulnerabilities.
- Purpose: To discover which ports are open and listening for connections on a target system.
- Methods: Port scanning can be performed using various tools like Nmap, Advanced Port Scanner, and command-line utilities.
- Types of Scans:
- TCP Connect Scan: Establishes a full TCP connection with the target port.
- SYN Scan (Stealth Scan): Sends a SYN packet to the target port and listens for a response without completing the TCP handshake.
- UDP Scan: Sends UDP packets to the target port and analyzes the response.
Legitimate Uses of Port Scanning
- Network Auditing: Identifying open ports to ensure that only necessary services are running.
- Security Assessments: Detecting potential vulnerabilities and misconfigurations.
- Troubleshooting: Diagnosing network connectivity issues.
Ethical Considerations
Port scanning should only be performed on networks and systems with explicit permission. Unauthorized port scanning can be considered a security threat and may have legal consequences.
6. How Do Firewalls Protect Ports?
Firewalls are essential security devices that control network traffic based on predefined rules. They act as a barrier between a network and the outside world, allowing authorized traffic while blocking malicious or unauthorized connections.
Firewall Functionality
- Traffic Filtering: Firewalls examine incoming and outgoing network traffic and allow or block packets based on IP addresses, port numbers, and protocols.
- Access Control: They enforce access control policies to restrict which services and applications can be accessed from the network.
- Network Address Translation (NAT): Firewalls can hide internal IP addresses from the outside world, providing an additional layer of security.
How Firewalls Protect Ports
Firewalls protect ports by allowing administrators to specify which ports should be open and which should be blocked. This helps prevent unauthorized access to services running on the server.
- Allowing Necessary Traffic: Firewalls can be configured to allow traffic to specific ports required for legitimate services, such as HTTP (port 80) and HTTPS (port 443).
- Blocking Unnecessary Traffic: They can block traffic to ports that are not required, reducing the attack surface and preventing unauthorized access.
Firewall Rules
Firewall rules are sets of instructions that define how the firewall should handle network traffic. These rules typically specify:
- Source IP Address: The IP address of the device sending the traffic.
- Destination IP Address: The IP address of the device receiving the traffic.
- Destination Port: The port number on the destination device.
- Protocol: The network protocol being used (e.g., TCP, UDP).
- Action: Whether to allow or block the traffic.
Example Scenario
Imagine you have a Windows server offering a webpage to the internet. The firewall would be set to allow all connections to port 80 (HTTP) and 443 (HTTPS) from any IP address inbound while blocking all other ports. If someone needed to establish a remote desktop connection into the server, the firewall would block access. The administrator would have to add a rule that opens port 3389 (RDP) for access from only one particular IP address.
7. Common Questions Asked About Port Numbers
Here are some frequently asked questions about port numbers, along with detailed answers:
What Is the Port Number for Localhost?
Localhost is the default name used to establish a connection with a computer. The IP address is usually 127.0.0.1. This is done by using a loopback address network. Port 80 is the common standard port for HTTP.
- Localhost IP Address: 127.0.0.1
- HTTP Port: 80
What Is Port Number 8080 Used For?
Port 8080 is usually used for web servers. When a port number is added to the end of the domain name, it drives traffic to the web server. However, users cannot reserve port 8080 for secondary web servers.
- Common Use: Web servers
- Secondary Web Servers: Often used as an alternative to port 80
What Is Port Number 3306 Used For?
Port 3306 is the default port for MySQL database connections. It is used for client applications to connect to a MySQL server.
- Protocol: TCP/IP
- This enables bidirectional data transfer once the connection is established.
What Is My IP Address and Port Number?
The easiest way to find a router’s public IP address is to search “what is my IP?” on a search engine like Google. Identifying a port number will depend on the operating system. The port number will change depending on what programs are running.
For Windows
- Go to the command prompt.
- Type ipconfig.
- Type netstat to populate a list of all the port numbers that the computer is currently connected to or from.
For macOS
- Go to System Preferences.
- Select Network > Advanced.
- Click on the Port Scan tab and enter the user’s IP address.
What Is a Proxy Server Address and Port Number?
Essentially, a proxy server is a computer that sits between a client device and the remote server. It acts as an intermediary to handle communication requests over the internet.
Using a proxy, when the local computer sends a web request, it will automatically go through the proxy server. The proxy server uses its own IP address for the web request and not the user’s IP address. Proxy servers offer privacy benefits, such as the ability to change the client IP address to mask the user’s location.
The proxy server address includes an IP address with the port number attached to the end of the address. The port number 8080 is usually used for web servers, proxy and caching.
What Is the Port Number for Gmail?
Gmail uses both Internet Message Access Protocol and SMTP. The IMAP port is 993, and the SMTP port is 25.
- IMAP Port: 993
- SMTP Port: 25
8. Choosing the Right Server with Rental-Server.Net
Selecting the right server for your needs is critical for performance, reliability, and security. Rental-server.net offers a range of server options to meet diverse requirements, from dedicated servers to VPS and cloud solutions.
Dedicated Servers
Dedicated servers provide exclusive access to hardware resources, ensuring maximum performance and control.
- Pros:
- High performance and reliability
- Full control over server configuration
- Enhanced security
- Cons:
- Higher cost
- Requires technical expertise to manage
VPS (Virtual Private Server)
VPS offers a cost-effective solution with dedicated resources in a virtualized environment.
- Pros:
- Lower cost than dedicated servers
- Scalable resources
- Good balance of performance and control
- Cons:
- Shared hardware resources
- Performance can be affected by other users
Cloud Servers
Cloud servers offer on-demand scalability and flexibility, allowing you to adjust resources as needed.
- Pros:
- Highly scalable and flexible
- Pay-as-you-go pricing
- Easy to manage
- Cons:
- Can be more expensive for consistent workloads
- Less control over hardware
Rental-Server.Net Advantages
- Wide Range of Options: Rental-server.net offers a variety of server types to suit different needs and budgets.
- Reliable Infrastructure: Our servers are housed in state-of-the-art data centers with redundant power, cooling, and network connectivity.
Address: 21710 Ashbrook Place, Suite 100, Ashburn, VA 20147, United States
Phone: +1 (703) 435-2000 - Expert Support: Our team of experienced technicians provides 24/7 support to help you with any issues.
- Customizable Solutions: We can tailor server configurations to meet your specific requirements.
Comparing Server Options
| Feature | Dedicated Server | VPS | Cloud Server |
|---|---|---|---|
| Performance | High | Medium | Variable |
| Control | Full | Good | Limited |
| Scalability | Limited | Scalable | Highly Scalable |
| Cost | High | Medium | Variable |
| Management | Self-Managed | Managed or Self-Managed | Managed |
| Best For | High-Traffic Sites | Small to Medium Businesses | Scalable Applications |
9. Securing Your Server Ports: Best Practices
Securing your server ports is crucial for protecting your data and preventing unauthorized access. Implementing robust security measures can significantly reduce the risk of cyberattacks.
Use a Firewall
A firewall is the first line of defense against unauthorized access. Configure your firewall to allow only necessary traffic to specific ports.
- Whitelist Approach: Only allow traffic to the ports required for essential services.
- Regular Updates: Keep your firewall software up to date to protect against the latest threats.
Disable Unused Ports
Disable any ports that are not being used. Open ports are potential entry points for attackers, so it’s important to minimize the attack surface.
- Regular Audits: Conduct regular audits to identify and disable unused ports.
- Service Configuration: Ensure that services are only listening on the necessary ports.
Use Strong Passwords
Use strong, unique passwords for all server accounts. Weak passwords are easy to crack and can allow attackers to gain unauthorized access.
- Password Complexity: Use a combination of uppercase and lowercase letters, numbers, and symbols.
- Password Rotation: Change passwords regularly to prevent them from being compromised.
Implement Intrusion Detection Systems (IDS)
An IDS can detect malicious activity and alert you to potential attacks.
- Real-Time Monitoring: Monitor network traffic for suspicious patterns and anomalies.
- Automated Responses: Configure the IDS to automatically block or mitigate detected threats.
Keep Software Up to Date
Keep all server software, including the operating system and applications, up to date. Software updates often include security patches that fix known vulnerabilities.
- Automated Updates: Enable automatic updates to ensure that software is always up to date.
- Patch Management: Implement a patch management process to quickly deploy security updates.
Regular Security Audits
Conduct regular security audits to identify potential vulnerabilities and ensure that security measures are effective.
- Vulnerability Scanning: Use vulnerability scanners to identify known vulnerabilities in your systems.
- Penetration Testing: Perform penetration testing to simulate real-world attacks and assess the effectiveness of your security measures.
10. Latest Trends in Server Technology
Staying up-to-date with the latest trends in server technology is essential for optimizing performance, security, and scalability.
Containerization
Containerization, using technologies like Docker and Kubernetes, allows you to package applications and their dependencies into containers, making them easy to deploy and manage across different environments.
- Benefits:
- Improved portability and consistency
- Increased resource utilization
- Simplified deployment and management
Serverless Computing
Serverless computing allows you to run code without managing servers. Cloud providers handle the underlying infrastructure, allowing you to focus on developing and deploying applications.
- Benefits:
- Reduced operational overhead
- Automatic scaling
- Pay-per-use pricing
Edge Computing
Edge computing involves processing data closer to the source, reducing latency and improving performance. This is particularly useful for applications that require real-time processing, such as IoT devices and autonomous vehicles.
- Benefits:
- Reduced latency
- Improved performance
- Enhanced security
AI and Machine Learning
AI and machine learning are being used to automate server management tasks, improve security, and optimize performance.
- Automated Monitoring: AI can be used to monitor server performance and detect anomalies.
- Predictive Maintenance: Machine learning can predict when servers are likely to fail, allowing you to schedule maintenance proactively.
- Enhanced Security: AI can be used to detect and prevent cyberattacks in real-time.
5G Technology
5G technology offers faster speeds and lower latency, enabling new possibilities for server technology.
- Faster Data Transfer: 5G enables faster data transfer between servers and clients.
- Improved Edge Computing: 5G enhances edge computing by providing faster and more reliable connectivity.
FAQ: Frequently Asked Questions About Server Port Numbers
Why are port numbers necessary for network communication?
Port numbers are essential because they allow multiple applications or services to run on the same server simultaneously. They act as unique identifiers, enabling network devices to direct traffic to the correct service, ensuring efficient and accurate data delivery.
What is the difference between TCP and UDP ports?
TCP (Transmission Control Protocol) and UDP (User Datagram Protocol) are two different protocols used for network communication. TCP is connection-oriented, providing reliable and ordered delivery of data, while UDP is connectionless, offering faster but less reliable data transmission.
- TCP Ports: Used for applications requiring reliable data transfer, such as web browsing (HTTP/HTTPS), email (SMTP/IMAP), and file transfer (FTP).
- UDP Ports: Used for applications where speed is more critical than reliability, such as online gaming, video streaming, and DNS queries.
How do I check if a port is open on my server?
You can check if a port is open on your server using command-line tools like netstat or telnet, graphical user interfaces like Resource Monitor, or third-party port scanning tools like Nmap.
Is it safe to leave ports open on my server?
Leaving unnecessary ports open on your server can pose a security risk. Open ports are potential entry points for attackers, so it’s important to minimize the attack surface by disabling any ports that are not being used.
What should I do if I find an unauthorized port open on my server?
If you find an unauthorized port open on your server, you should immediately investigate the cause and take steps to secure it.
Can I change the default port number for a service?
Yes, you can change the default port number for a service, but it’s generally not recommended unless necessary. Changing the default port number can cause compatibility issues and may require additional configuration.
How do I forward a port on my router?
Port forwarding allows external devices to connect to a specific service running on your local network. The process varies depending on your router model.
What are some common security risks associated with open ports?
Some common security risks associated with open ports include unauthorized access, malware infections, and denial-of-service attacks.
How often should I scan my server for open ports?
You should scan your server for open ports regularly, at least once a month, or more frequently if you suspect a security breach.
Where can I find a comprehensive list of port numbers and their uses?
You can find a comprehensive list of port numbers and their uses on the Internet Assigned Numbers Authority (IANA) website.
Conclusion
Understanding How To Find The Port Number Of A Server is crucial for effective server management and security. By using the techniques and tools outlined in this guide, you can identify open ports, secure your server, and optimize its performance. Remember that rental-server.net offers a variety of server solutions to meet your specific needs, backed by reliable infrastructure and expert support. Explore our offerings today and take your server infrastructure to the next level. Address: 21710 Ashbrook Place, Suite 100, Ashburn, VA 20147, United States, Phone: +1 (703) 435-2000. Don’t wait – visit rental-server.net now to discover the perfect server solution for your needs in the USA.
