Finding the port of a server is crucial for effective network communication and troubleshooting. This guide from rental-server.net provides a detailed explanation of server ports, their types, and how to identify them. Understanding port numbers is essential for managing server connections, enhancing network security, and optimizing server performance, especially when considering various server options like dedicated servers, VPS, and cloud servers.
1. What is a Server Port?
A server port is a virtual point where network connections start and end. Think of it as a doorway that allows specific types of traffic to enter or exit a server. These ports are identified by numbers ranging from 0 to 65535, and they enable servers to manage multiple services simultaneously. All network-connected devices utilize standardized ports with assigned numbers, reserved for specific protocols and their associated functions. According to Cisco, understanding server ports is fundamental to network administration.
1.1. Why are Server Ports Important?
Server ports are vital because they allow servers to differentiate between various types of network traffic. For example, web traffic typically uses port 80 (HTTP) or 443 (HTTPS), while email traffic uses port 25 (SMTP) or 143/993 (IMAP). This differentiation ensures that data is routed to the correct application or service running on the server. Understanding the functionality of server ports is paramount for anyone managing or utilizing server resources. Without them, data packets would not be able to reach their intended applications, leading to network chaos.
1.2. The History of Server Ports
The concept of port numbers was first proposed by developers of the Advanced Research Projects Agency Network (ARPANET). Initially known as socket numbers, they were designed to facilitate communication between different applications on the same machine or across a network. The early incarnation of port numbers was similar to the Internet Protocol (IP) address class used today. The Internet Engineering Task Force (IETF) plays a crucial role in standardizing these protocols, ensuring interoperability across different systems.
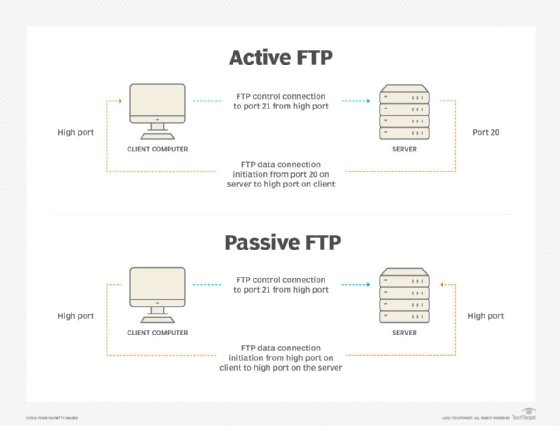 Active FTP and passive FTP diagram.
Active FTP and passive FTP diagram.
This diagram illustrates the active and passive modes of FTP, highlighting the use of ports 20 and 21 for file transfer.
2. IP Address vs. Port Number: What’s the Difference?
An IP address identifies a device on a network, while a port number specifies a particular application or service running on that device. If a computer were a building and the internet were a city, the IP address would be the building’s street address, and the port number would be the apartment number. According to research from the Uptime Institute, understanding the distinction between IP addresses and port numbers is essential for effective network management.
2.1. IP Address Explained
An IP address is a logical address that uniquely identifies a device on a network. Every device connected to the internet or a local network is assigned an IP address, allowing it to communicate with other devices. These addresses come in two main versions: IPv4 (32-bit) and IPv6 (128-bit). IPv4 addresses are more common but are gradually being replaced by IPv6 due to the increasing number of devices connected to the internet.
2.2. Port Number Explained
Port numbers are part of the addressing information that identifies senders and receivers of data. These 16-bit numbers, ranging from 1 to 65535, specify a particular application or service on a device. For example, when a client requests a file transfer from a remote server using File Transfer Protocol (FTP), the Transmission Control Protocol (TCP) software layer identifies port 21, which is associated with FTP requests.
2.3. Real-World Analogy
Imagine you’re sending a letter to a large office building. The IP address is like the street address of the building, ensuring the letter arrives at the correct location. The port number is like the suite number, ensuring the letter is delivered to the correct department within the building. Together, the IP address and port number ensure that data packets reach the intended application on the correct device.
3. Types of Port Numbers and Their Uses
While there are 65,535 possible port numbers, not all are used every day. These ports are categorized into three main types: well-known ports, registered ports, and dynamic/private ports.
3.1. Well-Known Ports (0 to 1023)
Well-known ports are reserved for common services and applications. These ports are controlled by the Internet Assigned Numbers Authority (IANA) and are typically used for essential network services like HTTP (port 80), HTTPS (port 443), FTP (port 21), and SSH (port 22). Using these ports requires root or administrator privileges on most operating systems.
3.1.1. Common Well-Known Ports
| Port Number | Service | Description |
|---|---|---|
| 20, 21 | FTP | File Transfer Protocol for transferring files between a client and a server. |
| 22 | SSH | Secure Shell for secure remote login and command execution. |
| 25 | SMTP | Simple Mail Transfer Protocol for sending email. |
| 53 | DNS | Domain Name System for translating domain names to IP addresses. |
| 80 | HTTP | Hypertext Transfer Protocol for serving web pages. |
| 110 | POP3 | Post Office Protocol version 3 for retrieving email. |
| 143 | IMAP | Internet Message Access Protocol for managing email on a server. |
| 443 | HTTPS | HTTP Secure for secure web communication using SSL/TLS. |
| 3389 | Remote Desktop (RDP) | Remote Desktop Protocol for remote access to Windows desktops. |
| 5900 | Virtual Network Computing (VNC) | VNC enables users to remotely access and control a computer’s desktop interface. |
3.1.2. Security Implications
Because well-known ports are commonly targeted by attackers, it’s crucial to secure them properly. Regularly monitoring these ports and implementing security measures like firewalls and intrusion detection systems can help protect against potential threats.
3.2. Registered Ports (1024 to 49151)
Registered ports are used by specific applications and vendors. Software companies typically register these port numbers with IANA for their specific protocols. While not as strictly controlled as well-known ports, registered ports help ensure that applications don’t conflict with each other.
3.2.1. Examples of Registered Ports
| Port Number | Service | Description |
|---|---|---|
| 1433 | Microsoft SQL | Default port for Microsoft SQL Server. |
| 1521 | Oracle | Default port for Oracle databases. |
| 3306 | MySQL | Default port for MySQL databases. |
| 5432 | PostgreSQL | Default port for PostgreSQL databases. |
| 8080 | HTTP Alternate | Commonly used for secondary web servers or proxy servers. |
| 8443 | HTTPS Alternate | Secure alternative to port 8080, often used for secure web administration interfaces. |
3.2.2. Choosing Registered Ports
When developing an application, choosing a registered port can help avoid conflicts with other applications. However, it’s essential to ensure that the chosen port is not already in use by another service on the same server.
3.3. Dynamic/Private Ports (49152 to 65535)
Dynamic or private ports are available for any program to use temporarily. These ports are typically assigned by the operating system for outgoing connections. When a client application makes a request to a server, it uses a dynamic port for the return traffic.
3.3.1. How Dynamic Ports Work
When a client initiates a connection to a server, the operating system assigns an available dynamic port to the client. This port is used for the duration of the connection, and once the connection is closed, the port becomes available for reuse. This dynamic assignment ensures that multiple client applications can communicate with the same server simultaneously.
3.3.2. Security Considerations
While dynamic ports are less likely to be targeted by attackers, it’s still important to monitor network traffic and implement security measures. Firewalls can be configured to allow traffic only on specific dynamic ports or within a certain range, enhancing overall network security.
4. Finding Open Ports and Port Scanning
An open port is a port number that is actively listening for incoming connections. Port scanning is the process of checking which ports on a server are open and responding to requests.
4.1. What is an Open Port?
An open port indicates that a service or application is actively listening for incoming connections on that port. When a program wants to receive communication over a network, it registers with the system network process to open a port number. When the system receives any network traffic for that port number, the system will forward it to the program to handle.
4.2. Why is Port Scanning Used?
Port scanning is used for various purposes, including:
- Security Audits: Identifying open ports to assess potential vulnerabilities.
- Network Troubleshooting: Diagnosing connectivity issues by checking if specific ports are open.
- Service Discovery: Discovering which services are running on a server.
4.3. Types of Port Scanning
There are several types of port scanning techniques, including:
- TCP Connect Scan: Establishes a full TCP connection to each port.
- SYN Scan: Sends a SYN packet and listens for a SYN-ACK response, without completing the full TCP handshake.
- UDP Scan: Sends UDP packets to each port and analyzes the responses.
- FIN Scan: Sends a FIN packet, which is used to gracefully close a connection.
4.4. Tools for Port Scanning
Several tools are available for port scanning, including:
- Nmap: A powerful and versatile tool for network discovery and security auditing.
- Angry IP Scanner: A fast and simple tool for scanning IP addresses and ports.
- Zenmap: The official GUI for Nmap, providing a user-friendly interface.
4.5. Legal and Ethical Considerations
It’s important to note that port scanning can be considered illegal or unethical if performed without permission. Always obtain explicit consent before scanning a network or server that you do not own or manage.
5. Firewalls: Protecting Ports
A firewall acts as a barrier between a network and the outside world, controlling which traffic is allowed to pass through. Firewalls use rules to allow or block traffic based on IP addresses, port numbers, and protocols.
5.1. How Firewalls Work
Firewalls examine incoming and outgoing network traffic and compare it against a set of predefined rules. If the traffic matches a rule, the firewall either allows or blocks it. This helps prevent unauthorized access to a server and protects against various types of network attacks.
5.2. Types of Firewalls
There are several types of firewalls, including:
- Hardware Firewalls: Physical devices that sit between a network and the internet.
- Software Firewalls: Applications that run on a computer or server to protect it.
- Cloud Firewalls: Firewalls that are hosted in the cloud and provide protection for cloud-based resources.
5.3. Configuring Firewall Rules
Configuring firewall rules involves specifying which traffic is allowed or blocked based on various criteria. For example, you might allow all incoming traffic on port 80 (HTTP) and 443 (HTTPS) to allow users to access your website, while blocking all other incoming traffic to prevent unauthorized access.
5.4. Best Practices for Firewall Management
- Keep your firewall software up to date: Regularly update your firewall software to ensure that it has the latest security patches.
- Use strong passwords: Protect your firewall with strong, unique passwords to prevent unauthorized access.
- Monitor firewall logs: Regularly review your firewall logs to identify and respond to potential security threats.
- Implement the principle of least privilege: Only allow the minimum necessary traffic through your firewall.
6. Identifying Open Ports on Different Operating Systems
The method for identifying open ports varies depending on the operating system. Here are instructions for Windows, macOS, and Linux.
6.1. Windows
-
Using Command Prompt:
- Open Command Prompt as an administrator.
- Type
netstat -anoand press Enter. - This command displays a list of all active network connections, including the local address, remote address, and the process ID (PID) using each port.
- Use Task Manager to identify the process associated with each PID.
-
Using PowerShell:
- Open PowerShell as an administrator.
- Type
Get-NetTCPConnectionand press Enter. - This command provides similar information to
netstat, including the local port, remote port, and state of the connection.
6.2. macOS
-
Using Terminal:
- Open Terminal.
- Type
netstat -an | grep LISTENand press Enter. - This command displays a list of all ports that are actively listening for connections.
-
Using Network Utility:
- Open Network Utility (located in /Applications/Utilities/).
- Click on the “Port Scan” tab.
- Enter the IP address of the server and specify a range of ports to scan.
- Click “Scan” to display a list of open ports.
6.3. Linux
-
Using netstat:
- Open a terminal.
- Type
netstat -tulnpand press Enter. - This command displays a list of all listening ports, including the protocol (TCP or UDP), local address, and the process ID (PID) using each port.
-
Using ss:
- Open a terminal.
- Type
ss -tulnpand press Enter. - The
sscommand is a modern alternative tonetstatand provides similar information.
-
Using lsof:
- Open a terminal.
- Type
lsof -i -P -n | grep LISTENand press Enter. - This command displays a list of all open network files, including listening ports and the associated processes.
7. Common Questions About Port Numbers
Here are some frequently asked questions about port numbers.
7.1. What is the Port Number for Localhost?
Localhost is the default name used to establish a connection with a computer. The IP address is usually 127.0.0.1. This is done by using a loopback address network. Port 80 is the common standard port for HTTP.
7.2. What is Port Number 8080 Used For?
Port 8080 is usually used for web servers. When a port number is added to the end of the domain name, it drives traffic to the web server. However, users cannot reserve port 8080 for secondary web servers.
7.3. What is Port Number 3306 Used For?
TCP/IP networks use port 3306, which is used as a communication endpoint for the MySQL database system. The connection-oriented protocol TCP demands handshaking to set up end-to-end communications. Upon establishing the connection, user data is transferred bidirectionally over the connection.
7.4. What is My IP Address and Port Number?
The easiest way to find a router’s public IP address is to search “what is my IP?” on a search engine like Google. Identifying a port number will depend on the operating system. The port number will change depending on what programs are running.
For Windows:
- Go to the command prompt.
- Type ipconfig.
- Type netstat to populate a list of all the port numbers that the computer is currently connected to or from.
For macOS:
- Go to System Preferences.
- Select Network > Advanced.
- Click on the Port Scan tab and enter the user’s IP address.
7.5. What is a Proxy Server Address and Port Number?
Essentially, a proxy server is a computer that sits between a client device and the remote server. It acts as an intermediary to handle communication requests over the internet.
Using a proxy, when the local computer sends a web request, it will automatically go through the proxy server. The proxy server uses its own IP address for the web request and not the user’s IP address. Proxy servers offer privacy benefits, such as the ability to change the client IP address to mask the user’s location.
The proxy server address includes an IP address with the port number attached to the end of the address. The port number 8080 is usually used for web servers, proxy and caching.
7.6. What is the Port Number for Gmail?
Gmail uses both Internet Message Access Protocol and SMTP. The IMAP port is 993, and the SMTP port is 25.
7.7. What is the Difference Between TCP and UDP Ports?
TCP (Transmission Control Protocol) and UDP (User Datagram Protocol) are two different protocols used for transmitting data over the internet. TCP is connection-oriented, meaning it establishes a connection before transmitting data and ensures reliable delivery. UDP, on the other hand, is connectionless and does not guarantee reliable delivery. TCP uses ports for reliable communication, while UDP uses ports for faster but less reliable communication.
7.8. Can a Port be Used by Multiple Applications?
Yes, but only under specific circumstances. Typically, only one application can listen on a specific port at a time. However, techniques like port sharing and multiplexing can allow multiple applications to share the same port.
7.9. How Do I Choose a Port Number for My Application?
When choosing a port number for your application, it’s best to use a registered port (1024 to 49151) or a dynamic/private port (49152 to 65535). Avoid using well-known ports (0 to 1023) unless your application provides a standard service.
7.10. What Are the Security Risks Associated with Open Ports?
Open ports can be exploited by attackers to gain unauthorized access to your server. It’s crucial to secure open ports by implementing firewalls, intrusion detection systems, and other security measures.
8. Optimizing Server Performance with Port Management
Effective port management can significantly impact server performance. By carefully configuring firewall rules and monitoring network traffic, you can optimize server performance and enhance security.
8.1. Load Balancing
Load balancing involves distributing network traffic across multiple servers to prevent any single server from becoming overloaded. This can be achieved by using a load balancer, which acts as a reverse proxy and distributes incoming traffic to multiple backend servers.
8.2. Quality of Service (QoS)
Quality of Service (QoS) allows you to prioritize certain types of network traffic over others. For example, you can prioritize VoIP traffic to ensure clear and uninterrupted voice communication.
8.3. Monitoring and Logging
Regularly monitoring network traffic and logging events can help you identify potential performance issues and security threats. Tools like Wireshark and tcpdump can be used to capture and analyze network traffic.
9. Choosing the Right Server and Port Configuration with rental-server.net
Selecting the appropriate server and port configuration is essential for optimal performance and security. Whether you need a dedicated server, VPS, or cloud server, rental-server.net offers a wide range of solutions to meet your specific needs.
9.1. Dedicated Servers
Dedicated servers offer the highest level of performance and control. With a dedicated server, you have exclusive access to all of the server’s resources, allowing you to customize the hardware and software to meet your specific requirements.
9.2. VPS (Virtual Private Servers)
VPS (Virtual Private Servers) provide a cost-effective alternative to dedicated servers. With a VPS, you share the resources of a physical server with other users, but each VPS operates independently with its own operating system and resources.
9.3. Cloud Servers
Cloud servers offer scalability and flexibility. With a cloud server, you can easily scale your resources up or down as needed, paying only for what you use. Cloud servers are ideal for applications with fluctuating traffic patterns.
9.4. How rental-server.net Can Help
At rental-server.net, we understand the complexities of server management and offer comprehensive solutions to simplify the process. Whether you’re looking for a dedicated server, VPS, or cloud server, we have the expertise and resources to help you choose the right solution for your needs.
- Expert Guidance: Our team of experienced professionals can provide expert guidance on choosing the right server and port configuration for your specific requirements.
- Wide Range of Solutions: We offer a wide range of server solutions, including dedicated servers, VPS, and cloud servers, to meet the needs of businesses of all sizes.
- Comprehensive Support: We provide comprehensive support to help you manage your server and ensure optimal performance.
To explore our service options and discover the perfect hosting solution tailored to your specific requirements, visit our website at rental-server.net, or contact us directly at Address: 21710 Ashbrook Place, Suite 100, Ashburn, VA 20147, United States. Phone: +1 (703) 435-2000.
10. Stay Updated with the Latest Trends
The world of server technology is constantly evolving. Stay updated with the latest trends and best practices to ensure that your server infrastructure is optimized for performance and security.
10.1. Emerging Technologies
- Containerization: Technologies like Docker and Kubernetes are revolutionizing the way applications are deployed and managed.
- Serverless Computing: Serverless computing allows you to run code without managing servers, reducing operational overhead.
- Edge Computing: Edge computing brings processing and storage closer to the edge of the network, reducing latency and improving performance.
10.2. Security Best Practices
- Zero Trust Security: Zero Trust security assumes that no user or device is trusted by default, requiring strict authentication and authorization.
- Multi-Factor Authentication (MFA): MFA adds an extra layer of security by requiring users to provide multiple forms of identification.
- Regular Security Audits: Conducting regular security audits can help you identify and address potential vulnerabilities.
By staying informed about the latest trends and best practices, you can ensure that your server infrastructure remains secure, efficient, and reliable.
Navigating the complexities of server ports and configurations can be challenging, but with the right knowledge and resources, you can optimize your server infrastructure for performance, security, and scalability. Explore the diverse range of server solutions available at rental-server.net to find the perfect fit for your unique needs, and empower your online presence with confidence and control.
