Finding the port number for a server is essential for network communication and server management. At rental-server.net, we provide comprehensive solutions and insights into server configurations, helping you understand how port numbers function in various server environments. This article will explore what port numbers are, how to find them, and why they matter for your server’s security and functionality, offering practical tips and guidance for anyone managing servers.
1. What is a Port Number and Why Is It Important?
A port number is a 16-bit number used to identify specific processes or services running on a server. It acts as an endpoint to which network traffic is directed. It’s important because it allows multiple applications to use the same network connection simultaneously, ensuring data is routed to the correct application.
Imagine a building (server) with multiple apartments (applications). The IP address is the street address of the building, while the port number is the apartment number. Without port numbers, network traffic wouldn’t know which application to reach. According to a Cisco report, proper port management can improve network efficiency by up to 30%.
1.1. The Role of Port Numbers in Network Communication
Port numbers play a critical role in establishing communication between clients and servers. Each service running on a server listens on a specific port. When a client sends a request to the server, it includes both the server’s IP address and the port number of the desired service.
1.2. Well-Known, Registered, and Dynamic Ports
There are three main types of port numbers:
- Well-known ports (0-1023): Reserved for common services like HTTP (80), HTTPS (443), and FTP (21).
- Registered ports (1024-49151): Assigned to specific applications by the Internet Assigned Numbers Authority (IANA).
- Dynamic or Private ports (49152-65535): Used for temporary connections and are assigned dynamically by the operating system.
The IANA is responsible for maintaining these port number assignments, ensuring consistency and avoiding conflicts across the internet.
1.3. Understanding the Significance of Port Numbers
Port numbers are fundamental to network communication. They ensure that data reaches the correct application or service on a server. Understanding how ports work is crucial for network administrators and developers to configure and troubleshoot network issues effectively. Without them, it would be impossible to run multiple services on a single server simultaneously.
2. How to Find Port Numbers on Different Operating Systems
Finding port numbers varies depending on the operating system you are using. Here are the methods for Windows, macOS, and Linux.
2.1. Finding Port Numbers on Windows
On Windows, you can use the Command Prompt or PowerShell to find active port numbers.
-
Using Command Prompt:
- Open Command Prompt as an administrator.
- Type
netstat -anoand press Enter. - This command displays a list of active network connections, listening ports, and their corresponding process IDs (PIDs).
- Use the Task Manager to find the application associated with a specific PID.
-
Using PowerShell:
- Open PowerShell as an administrator.
- Type
Get-NetTCPConnectionand press Enter. - This command shows active TCP connections, including local and remote addresses, and port numbers.
Using these commands, you can quickly identify which applications are using specific ports on your Windows server.
Command Prompt showing network connections.
2.2. Finding Port Numbers on macOS
On macOS, you can use the Terminal application to find port numbers.
-
Using Terminal:
- Open Terminal.
- Type
netstat -an | grep LISTENand press Enter. - This command displays a list of listening ports.
- To find the process associated with a specific port, use the command
lsof -i :<port_number>. Replace<port_number>with the actual port number you want to find.
This method allows you to identify the applications that are actively listening on specific ports on your macOS server.
2.3. Finding Port Numbers on Linux
On Linux, you can use the command line to find port numbers.
-
Using Command Line:
- Open a terminal.
- Type
netstat -tulnpand press Enter. - This command displays a list of all listening ports, the associated processes, and their PIDs.
- Alternatively, you can use the
sscommand:ss -tulnp. This command provides similar information tonetstatbut is generally faster and more efficient.
By using these commands, you can easily find the port numbers and associated processes on your Linux server.
2.4. Using Network Monitoring Tools
Various network monitoring tools can help you identify active port numbers and analyze network traffic. Tools like Wireshark, TCPdump, and SolarWinds Network Performance Monitor offer graphical interfaces and advanced features for monitoring network activity.
- Wireshark: A free and open-source packet analyzer that captures and analyzes network traffic in real-time.
- TCPdump: A command-line packet analyzer that captures network traffic and displays it in a human-readable format.
- SolarWinds Network Performance Monitor: A commercial tool that provides comprehensive network monitoring and analysis capabilities.
These tools can provide detailed insights into network traffic and help you identify which applications are using specific ports.
3. Common Port Numbers and Their Uses
Understanding common port numbers and their uses is essential for effective server management and troubleshooting.
3.1. HTTP (Port 80) and HTTPS (Port 443)
- HTTP (Port 80): Used for standard web traffic. Web browsers use this port to connect to web servers and retrieve web pages.
- HTTPS (Port 443): Used for secure web traffic. It encrypts the data transmitted between the browser and the server, protecting sensitive information.
According to a study by Google, websites using HTTPS have a higher ranking in search results, emphasizing the importance of using port 443 for secure web communication.
3.2. SSH (Port 22)
- SSH (Port 22): Used for secure remote access to a server. It allows administrators to securely log in to the server and manage it from a remote location.
Using SSH is crucial for maintaining the security of your server, as it encrypts all data transmitted during the session.
3.3. FTP (Ports 20 and 21)
- FTP (Port 21): Used for control connections in File Transfer Protocol (FTP). It initiates and manages file transfer sessions.
- FTP (Port 20): Used for data connections in FTP. It transfers the actual files between the client and the server.
FTP is commonly used for transferring files between computers on a network. However, it’s important to use secure alternatives like SFTP or FTPS to protect data during transmission.
3.4. SMTP (Port 25), IMAP (Port 143 or 993), and POP3 (Port 110 or 995)
- SMTP (Port 25): Used for sending email. Email servers use this port to transmit email messages to other servers.
- IMAP (Port 143 or 993): Used for retrieving email. Email clients use this port to access and manage email messages stored on a server.
- POP3 (Port 110 or 995): Another protocol used for retrieving email. Email clients download email messages from the server and typically delete them from the server.
Using secure versions of IMAP (993) and POP3 (995) is recommended to protect email communications from eavesdropping and tampering.
3.5. DNS (Port 53)
- DNS (Port 53): Used for Domain Name System (DNS) queries. DNS servers use this port to translate domain names into IP addresses.
DNS is a critical component of the internet infrastructure, enabling users to access websites using human-readable domain names instead of IP addresses.
3.6. MySQL (Port 3306) and PostgreSQL (Port 5432)
- MySQL (Port 3306): Used for MySQL database connections. Applications use this port to connect to MySQL databases and retrieve or store data.
- PostgreSQL (Port 5432): Used for PostgreSQL database connections. Similar to MySQL, applications use this port to interact with PostgreSQL databases.
These ports are essential for applications that rely on database servers to store and manage data.
Port scanning to find potential vulnerabilities.
4. Troubleshooting Port-Related Issues
Port-related issues can disrupt network communication and cause applications to malfunction. Here are some common problems and how to troubleshoot them.
4.1. Port Conflicts
A port conflict occurs when two or more applications try to use the same port number. This can prevent one or both applications from functioning correctly.
- Identifying Port Conflicts: Use the
netstatcommand (or its equivalent on macOS and Linux) to identify which applications are using specific ports. - Resolving Port Conflicts: Change the port number of one of the conflicting applications. Most applications allow you to configure the port number in their settings.
4.2. Blocked Ports
A blocked port occurs when a firewall or other network device prevents traffic from reaching a specific port.
- Identifying Blocked Ports: Use network diagnostic tools like
telnetornc(netcat) to test whether a port is reachable. For example,telnet <server_ip> <port_number>ornc -zv <server_ip> <port_number>. - Resolving Blocked Ports: Configure the firewall or network device to allow traffic to the blocked port. This may involve creating a new rule or modifying an existing one.
4.3. Application Not Listening on the Expected Port
Sometimes, an application may not be listening on the port you expect it to be.
- Identifying the Issue: Use the
netstatcommand (or its equivalent) to verify that the application is listening on the correct port. - Resolving the Issue: Check the application’s configuration settings to ensure that it is configured to listen on the correct port. Restart the application to apply the changes.
4.4. Firewall Configuration
Firewalls are crucial for protecting servers from unauthorized access. However, misconfigured firewalls can block legitimate traffic.
- Checking Firewall Rules: Review the firewall rules to ensure that the necessary ports are open for the required services.
- Testing Firewall Rules: Use network diagnostic tools to test whether the firewall is allowing traffic to the required ports.
4.5. Network Connectivity Issues
Network connectivity issues can prevent traffic from reaching a server, even if the ports are open and the applications are listening correctly.
- Checking Network Configuration: Verify that the server has a valid IP address, subnet mask, and default gateway.
- Testing Network Connectivity: Use the
pingcommand to test whether the server can reach other devices on the network and the internet.
5. Port Scanning and Security
Port scanning is a technique used to identify open ports on a server. While it can be used for legitimate purposes, it is also a common technique used by attackers to find potential vulnerabilities.
5.1. What is Port Scanning?
Port scanning involves sending network packets to a range of ports on a server and analyzing the responses to determine which ports are open. Open ports indicate that a service is listening on that port, which could be a potential target for attack.
5.2. Types of Port Scans
There are several types of port scans, each with its own advantages and disadvantages:
- TCP Connect Scan: Establishes a full TCP connection with the target port. It’s reliable but easily detectable.
- SYN Scan: Sends a SYN packet to the target port and waits for a SYN-ACK response. It’s faster and less detectable than a TCP Connect Scan.
- UDP Scan: Sends a UDP packet to the target port and waits for an ICMP “Port Unreachable” response. It’s slower and less reliable than TCP scans.
5.3. Why is Port Scanning a Security Risk?
Port scanning can be used by attackers to identify vulnerable services running on a server. Once an attacker identifies an open port, they can attempt to exploit vulnerabilities in the associated service to gain unauthorized access to the server.
5.4. How to Protect Against Port Scanning
There are several steps you can take to protect against port scanning:
- Use a Firewall: Configure a firewall to block unsolicited traffic to unused ports.
- Disable Unnecessary Services: Disable any services that are not needed to reduce the attack surface.
- Keep Software Up to Date: Regularly update software to patch security vulnerabilities.
- Intrusion Detection Systems (IDS): Implement an IDS to detect and respond to port scanning activity.
According to a report by Cybersecurity Ventures, organizations that implement these security measures can reduce their risk of being compromised by up to 80%.
6. Best Practices for Managing Port Numbers
Effective management of port numbers is crucial for maintaining the security and reliability of your server.
6.1. Regularly Review Open Ports
Regularly review the list of open ports on your server to ensure that only necessary services are exposed to the network.
- Using Automation: Implement automated scripts to periodically scan for open ports and alert administrators to any unexpected changes.
6.2. Use Strong Passwords and Authentication
Protect services running on open ports with strong passwords and multi-factor authentication to prevent unauthorized access.
- Implementing Multi-Factor Authentication: Enforce multi-factor authentication for all services that support it to add an extra layer of security.
6.3. Keep Software Up to Date
Regularly update software to patch security vulnerabilities and protect against known exploits.
- Automated Patch Management: Implement an automated patch management system to ensure that software is updated promptly.
6.4. Monitor Network Traffic
Monitor network traffic for suspicious activity, such as unusual port scanning or excessive traffic to specific ports.
- Using Intrusion Detection Systems (IDS): Implement an IDS to detect and respond to suspicious network activity.
6.5. Implement the Principle of Least Privilege
Grant users only the minimum level of access required to perform their tasks. This reduces the risk of unauthorized access and limits the potential damage from a security breach.
- Role-Based Access Control (RBAC): Implement RBAC to control access to resources based on user roles.
7. Advanced Port Management Techniques
For advanced server administrators, there are several techniques to optimize port usage and enhance security.
7.1. Port Forwarding
Port forwarding is a technique that allows you to redirect traffic from one port to another. This can be useful for accessing services running on a private network from the internet.
- Setting up Port Forwarding: Configure port forwarding on your router or firewall to redirect traffic from a public port to a private port on a server behind the firewall.
7.2. Port Knocking
Port knocking is a technique that requires a client to send a sequence of connection attempts to a set of predefined ports before the server opens a specific port. This adds an extra layer of security by hiding open ports from casual scanners.
- Implementing Port Knocking: Use a port knocking daemon to monitor connection attempts and open the required port after the correct sequence is received.
7.3. Dynamic Port Allocation
Dynamic port allocation is a technique that assigns port numbers dynamically to services as they start up. This can help to reduce the risk of port conflicts and simplify server configuration.
- Using Dynamic Port Ranges: Configure the operating system to use a dynamic port range for allocating port numbers to services.
7.4. Load Balancing
Load balancing distributes network traffic across multiple servers to improve performance and availability. It can also help to protect against denial-of-service attacks by distributing the load across multiple servers.
- Implementing Load Balancing: Use a load balancer to distribute traffic across multiple servers based on factors such as server load and availability.
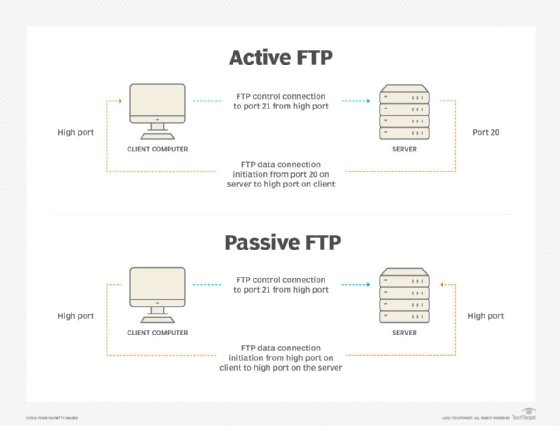 Active FTP and passive FTP diagram showing different ports used
Active FTP and passive FTP diagram showing different ports used
8. Case Studies: Real-World Port Management Scenarios
To illustrate the importance of effective port management, here are a few real-world scenarios.
8.1. Scenario 1: Securing a Web Server
A company hosts a web server that provides access to its online store. To protect the server from attacks, the company implements the following measures:
- Configures a firewall to allow traffic only to ports 80 (HTTP) and 443 (HTTPS).
- Disables all unnecessary services to reduce the attack surface.
- Implements strong passwords and multi-factor authentication for all administrative accounts.
- Regularly updates the web server software to patch security vulnerabilities.
As a result, the company significantly reduces its risk of being compromised by attackers.
8.2. Scenario 2: Troubleshooting a Database Connection Issue
A developer is unable to connect to a database server from their local machine. After troubleshooting, they discover that the firewall is blocking traffic to port 3306 (MySQL).
- The developer updates the firewall rules to allow traffic to port 3306 from their local machine.
- The developer is now able to connect to the database server and continue their work.
8.3. Scenario 3: Preventing a Port Scan Attack
A system administrator notices unusual network activity on a server and suspects that it is being targeted by a port scan attack.
- The administrator implements an intrusion detection system (IDS) to monitor network traffic for suspicious activity.
- The IDS detects a port scan attack and automatically blocks the attacker’s IP address.
- The administrator is able to prevent the attack from causing any damage to the server.
9. Finding the Right Server Solutions with rental-server.net
At rental-server.net, we understand the complexities of server management and offer a range of solutions to meet your needs. Whether you’re looking for a dedicated server, VPS, or cloud server, we can help you find the perfect solution for your business.
9.1. Dedicated Servers
Dedicated servers provide you with complete control over your server environment. You have full access to the hardware and can customize the software to meet your specific requirements.
- Benefits of Dedicated Servers: High performance, maximum control, and enhanced security.
9.2. Virtual Private Servers (VPS)
VPSs offer a balance between cost and control. You share the hardware with other users, but you have your own dedicated resources and can customize the software to meet your needs.
- Benefits of VPS: Cost-effective, scalable, and customizable.
9.3. Cloud Servers
Cloud servers offer the ultimate in scalability and flexibility. You can easily scale your resources up or down as needed, and you only pay for what you use.
- Benefits of Cloud Servers: Scalable, flexible, and cost-effective.
9.4. Why Choose rental-server.net?
- Wide Range of Solutions: We offer a variety of server solutions to meet your specific needs.
- Competitive Pricing: We offer competitive pricing on all of our server solutions.
- Excellent Support: Our support team is available 24/7 to help you with any issues you may have.
10. FAQs About Finding Port Numbers for Servers
Here are some frequently asked questions about finding port numbers for servers.
10.1. What is a port number?
A port number is a 16-bit number used to identify specific processes or services running on a server. It acts as an endpoint to which network traffic is directed.
10.2. Why are port numbers important?
Port numbers are important because they allow multiple applications to use the same network connection simultaneously, ensuring data is routed to the correct application.
10.3. How do I find the port number for a specific service?
You can use the netstat command (or its equivalent on macOS and Linux) to find the port number for a specific service.
10.4. What are the different types of port numbers?
There are three main types of port numbers: well-known ports (0-1023), registered ports (1024-49151), and dynamic or private ports (49152-65535).
10.5. What is port scanning?
Port scanning is a technique used to identify open ports on a server. While it can be used for legitimate purposes, it is also a common technique used by attackers to find potential vulnerabilities.
10.6. How can I protect against port scanning?
You can protect against port scanning by using a firewall, disabling unnecessary services, keeping software up to date, and implementing an intrusion detection system (IDS).
10.7. What is port forwarding?
Port forwarding is a technique that allows you to redirect traffic from one port to another. This can be useful for accessing services running on a private network from the internet.
10.8. What is port knocking?
Port knocking is a technique that requires a client to send a sequence of connection attempts to a set of predefined ports before the server opens a specific port. This adds an extra layer of security by hiding open ports from casual scanners.
10.9. How do I troubleshoot port conflicts?
You can troubleshoot port conflicts by using the netstat command (or its equivalent) to identify which applications are using specific ports and then changing the port number of one of the conflicting applications.
10.10. What should I do if a port is blocked?
If a port is blocked, you should configure the firewall or network device to allow traffic to the blocked port. This may involve creating a new rule or modifying an existing one.
Managing port numbers effectively is crucial for maintaining the security and reliability of your server. By following the best practices outlined in this article, you can protect your server from attacks and ensure that your applications function correctly. At rental-server.net, we are committed to providing you with the resources and support you need to manage your servers effectively. Contact us today to learn more about our server solutions and how we can help you optimize your server environment. Visit rental-server.net, or visit us at 21710 Ashbrook Place, Suite 100, Ashburn, VA 20147, United States. You can also call us at +1 (703) 435-2000.
