The client-server model stands as a cornerstone of modern computing, forming the architectural foundation for the vast majority of applications and services we interact with daily. This distributed application structure efficiently divides tasks and workloads between resource providers, known as servers, and service requesters, called clients. In essence, when a client computer requires data or a specific service, it sends a request over a network, typically the internet, to a server. The server, upon receiving this request, processes it and delivers the requested data packets back to the client. A key characteristic of this model is that clients do not share their resources with each other; they solely rely on servers for resources and services. Common examples of the Client-Server Model in action include email systems and the World Wide Web itself.
Delving Deeper: How the Client-Server Model Operates
To fully grasp the client-server model, it’s crucial to understand the roles of clients and servers and how they interact, particularly in the context of internet browsing. This understanding provides a solid foundation for working with web technologies and comprehending the internet’s infrastructure.
-
Client: In the client-server context, a client is any computer or system (referred to as a host) that initiates a request to utilize a service or obtain information from a server. Think of it as the user-facing side, the point of interaction where users access applications and data. Web browsers, email applications, and even online games act as clients when they request data from servers.
-
Server: Conversely, a server is a remote computer system dedicated to providing information, data, or access to specific services. Servers are the backbone of the internet and internal networks, designed to handle requests from numerous clients simultaneously. They are equipped with the necessary hardware and software to store, process, and transmit data efficiently. Web servers, email servers, and database servers are all examples of servers providing different types of services.
Fundamentally, the client-server model is a request-response system: the client requests, and the server responds, provided the requested information or service is available.
 Client Server Request and Response
Client Server Request and Response
The Browser’s Interaction with Servers: A Step-by-Step Breakdown
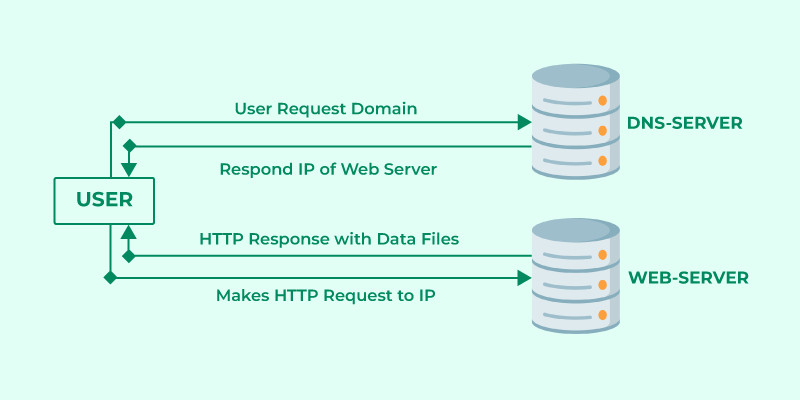
When you browse the internet, your browser engages in a series of interactions with servers based on the client-server model. Here’s a detailed breakdown of the process:
-
URL Entry and DNS Request: The user initiates the process by entering a website address, known as a URL (Uniform Resource Locator), into the browser’s address bar. The browser then begins by querying a DNS (Domain Name System) Server.
-
DNS Server Lookup: The DNS Server’s role is to translate the human-readable website name (like
rental-server.net) into a numerical IP address (Internet Protocol address) that computers use to identify each other on the internet. The DNS server searches its database to find the IP address associated with the requested website URL. -
IP Address Response: The DNS Server responds to the browser with the IP address of the web server that hosts the website.
-
HTTP/HTTPS Request to Web Server: Armed with the web server’s IP address, the browser sends an HTTP (Hypertext Transfer Protocol) or HTTPS (HTTP Secure) request to that IP address. This request is essentially asking the web server to send the website’s files. HTTPS is the secure version of HTTP, encrypting communication for enhanced security.
-
Server File Delivery: The web server receives the request and, if everything is in order, sends back the necessary files to display the website. These files typically include HTML (Hypertext Markup Language) for structure, CSS (Cascading Style Sheets) for styling, and JavaScript for interactivity.
-
Browser Rendering and Display: Finally, the browser receives these files and renders them to display the website on the user’s screen. This rendering process involves several interpreters:
- DOM (Document Object Model) interpreter: Parses the HTML and creates a structured representation of the web page.
- CSS interpreter: Applies the styles defined in CSS files to the HTML structure.
- JS Engine (JavaScript Engine): Executes any JavaScript code to enable dynamic and interactive elements on the webpage.
These components collectively are sometimes referred to as JIT (Just-In-Time) Compilers, as they interpret and compile code in real-time as needed.
Advantages of the Client-Server Model
The client-server model offers several significant advantages, making it a preferred architecture for many applications:
-
Centralized System: Data and resources are centralized on servers, providing a single point of access and control. This centralization simplifies management, enhances security, and ensures data consistency.
-
Cost Efficiency: Centralization leads to cost savings in several ways. Maintenance costs are reduced as resources are concentrated. Data recovery and backups are more manageable and cost-effective when handled centrally on servers.
-
Scalability: The client-server model allows for independent scaling of client and server components. Server capacity can be upgraded to handle increased client load without requiring changes to the client side. This scalability is crucial for accommodating growing user bases and increasing demands.
Disadvantages of the Client-Server Model
Despite its advantages, the client-server model also has certain drawbacks that need to be considered:
-
Security Vulnerabilities: Centralized servers can become single points of failure and targets for attacks. If a server is compromised, clients connected to it can be vulnerable to various threats.
- Malware Propagation: If a server becomes infected with viruses, Trojans, or worms, these can potentially spread to connected clients.
- Denial of Service (DoS) Attacks: Servers are susceptible to DoS attacks, where malicious actors flood the server with requests, overwhelming it and preventing legitimate clients from accessing services.
-
Data Interception Risks: Data transmitted between clients and servers can be intercepted or modified during transmission if not properly secured.
- Spoofing and Data Modification: Attackers can potentially spoof data packets or modify data in transit, leading to data breaches or corruption.
- Phishing and MITM Attacks: Phishing attacks can trick users into revealing login credentials or sensitive information. MITM (Man-in-the-Middle) attacks involve intercepting communication between a client and server to steal or manipulate data.
Conclusion
The client-server architecture provides a robust and efficient framework for distributed computing. By centralizing resources and processing on servers, it offers enhanced control, security, and scalability. While cost-effective and widely adopted, it’s essential to acknowledge and mitigate its inherent security risks. The client-server model remains fundamental to modern IT infrastructure and continues to evolve, adapting to trends like cloud computing, which further leverages its principles for delivering scalable and accessible services.
