File Transfer Protocol (FTP) is a standard network protocol used for transferring files between a client and server on a network. Think of it as a language computers use to exchange data, similar to how HTTP is used for web browsing. While FTP is widely used, it’s important to note that by default, it transmits data without encryption, making it less secure for sensitive information.
For Ubuntu users seeking a straightforward way to establish an FTP server, vsftpd (Very Secure FTP Daemon) stands out as the most user-friendly option.
This guide provides a detailed walkthrough on how to install and configure an FTP server on Ubuntu using vsftpd.
 A visual guide to installing an FTP server on Ubuntu with vsftpd.
A visual guide to installing an FTP server on Ubuntu with vsftpd.
Prerequisites
Before you begin, ensure you have the following:
- Root Privileges: Access to a user account with root or sudo privileges on your Ubuntu system.
- Terminal Access: Access to a terminal window or command line. You can typically open this with the shortcut Ctrl+Alt+T.
- apt Package Manager: Ubuntu’s default package manager,
apt, must be installed and functional.
Installing the FTP Server on Ubuntu
Follow these step-by-step instructions to install the vsftpd utility on your Ubuntu server:
Step 1: Update Your System Packages
It’s always best practice to start by updating your system’s package repository. This ensures you’re installing the latest available version of vsftpd and its dependencies. Open your terminal and execute the following command:
sudo apt updateWait for the update process to complete before proceeding.
Step 2: Install the vsftpd Package
vsftpd is a popular open-source FTP server known for its security and speed. Install it on your Ubuntu system using the following command:
sudo apt install vsftpdStep 3: Start and Enable vsftpd Service
Once the installation is complete, you need to start the vsftpd service and enable it to launch automatically whenever your system boots. Run these commands in your terminal:
sudo systemctl start vsftpd
sudo systemctl enable vsftpdStep 4: Back Up the Default Configuration File
Before making any modifications, it’s crucial to back up the default vsftpd configuration file. This allows you to revert to the original settings if needed. Use the cp command to create a backup:
sudo cp /etc/vsftpd.conf /etc/vsftpd.conf_defaultThis command creates a copy of vsftpd.conf named vsftpd.conf_default in the same directory (/etc/).
Step 5: Create a Dedicated FTP User (Optional)
For enhanced security, it’s recommended to create a dedicated user account specifically for FTP access. If you prefer to grant FTP access to an existing user, you can skip this step.
To create a new user, use the useradd command followed by passwd to set the password:
sudo useradd -m [username]
sudo passwd [username]Replace [username] with your desired username. For example, to create a user named ftpuser, you would use:
sudo useradd -m ftpuser
sudo passwd ftpuserYou will be prompted to enter and confirm a password for the new user.
Step 6: Configure the Firewall for FTP Traffic
If you have the UFW firewall enabled on your Ubuntu system (which is common), it will likely be blocking FTP traffic by default. To allow connections to your FTP server, you need to open ports 20 and 21 in the firewall. Execute these commands:
sudo ufw allow 20/tcp
sudo ufw allow 21/tcp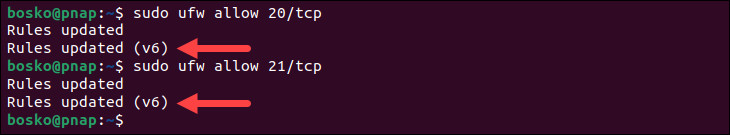 Commands to update firewall rules to permit FTP traffic on ports 20 and 21.
Commands to update firewall rules to permit FTP traffic on ports 20 and 21.
If you are using a different firewall, consult its documentation to learn how to open ports 20 and 21 for TCP traffic. These ports are essential for FTP communication.
Step 7: Connect to Your Ubuntu FTP Server
Now that the server is installed and the firewall is configured, you can attempt to connect to your FTP server. Use the following command syntax:
ftp [system_name]Replace [system_name] with the hostname or IP address of your Ubuntu system. If you are testing locally, you can use localhost or 127.0.0.1.
For example:
ftp localhostOnce connected, log in using the username and password you created in Step 5 or with the credentials of an existing user you are granting FTP access to.
Configuring Your vsftpd Server for Optimal Use
Configuration is key to tailoring your FTP server to your specific needs. By modifying the vsftpd.conf file, you can adjust various settings to enhance security, performance, and features. Let’s explore some essential configurations.
Changing the Default FTP Directory
By default, vsftpd uses the /srv/ftp directory as the root directory for FTP users. For security and organizational purposes, you might want to change this default or create specific directories for different users.
Here’s how to change the default directory:
-
Create a New Directory: Use the
mkdircommand to create your desired directory. For example, to create a directory namedftpsharewithin/srv/ftp, use:sudo mkdir /srv/ftp/ftpshare -
Modify User Home Directory: To change the default directory for a specific FTP user, use the
usermodcommand. For instance, to set/srv/ftp/ftpshareas the home directory for theftpuser, run:sudo usermod -d /srv/ftp/ftpshare ftp -
Restart vsftpd Service: Apply the changes by restarting the
vsftpdservice:sudo systemctl restart vsftpd.service
Now, when the specified FTP user logs in, they will be placed directly into the newly configured directory.
Enabling FTP User Authentication for Uploads
By default, anonymous uploads might be disabled. If you need to allow authenticated FTP users to upload files to the server, you must modify the vsftpd.conf file.
-
Open
vsftpd.conf: Use a text editor likenanoto open the configuration file:sudo nano /etc/vsftpd.conf -
Enable Write Access: Locate the line
#write_enable=YESand uncomment it by removing the#at the beginning of the line, so it reads:write_enable=YES. -
Save and Restart: Save the changes to the
vsftpd.conffile, exit the editor, and restart thevsftpdservice to activate the changes:sudo systemctl restart vsftpd.service
With this setting enabled, authenticated users will have the permission to create, modify, and delete files within their designated home directories.
Securing Your Ubuntu FTP Server
Security is paramount when running an FTP server, especially if it’s accessible over the internet. Unsecured FTP servers are vulnerable to various exploits. vsftpd offers several configuration options to bolster your server’s security and protect against unauthorized access and data breaches.
Restricting User Access to Home Directories (Chroot)
Chrooting users confines them to their home directory, preventing them from navigating to other parts of the server’s file system. This is a vital security measure.
-
Open
vsftpd.conf: Access the configuration file using a text editor:sudo nano /etc/vsftpd.conf -
Enable Chroot: Find and uncomment the line
#chroot_local_user=YESto activate the chroot feature for all local users:chroot_local_user=YES. -
Save and Restart: Save the file, exit the editor, and restart the
vsftpdservice:sudo systemctl restart vsftpd.service
Implementing User Lists for Granular Access Control
For more refined control over user access, you can use user lists. This allows you to explicitly permit or deny access to specific users, overriding the default chroot setting for listed users.
-
Create User List File: Create a file named
vsftpd.chroot_listin the/etc/directory and add usernames to it, one per line. These users will be exempt from the chroot restriction and have broader access. -
Configure
vsftpd.conf: Openvsftpd.confand ensure the following lines are uncommented:chroot_local_user=YES chroot_list_enable=YES chroot_list_file=/etc/vsftpd.chroot_list -
Restart vsftpd: Apply the changes by restarting the service:
sudo systemctl restart vsftpd.service
Conversely, you can block users by adding them to the /etc/ftpusers file. Users listed in this file will be denied FTP access entirely.
Encrypting FTP Traffic with FTPS (FTP over SSL/TLS)
To secure data transmission and prevent eavesdropping, encrypt your FTP traffic using FTPS. This adds a layer of SSL/TLS encryption to the standard FTP protocol.
-
Generate SSL Certificate: Create a self-signed SSL certificate using
openssl. This certificate will be used to encrypt the FTP traffic.sudo openssl req -x509 -nodes -days 365 -newkey rsa:2048 -keyout /etc/ssl/private/vsftpd.pem -out /etc/ssl/private/vsftpd.pemYou will be prompted for information to include in the certificate. You can accept the defaults by pressing Enter through the prompts if needed for testing purposes.
-
Configure
vsftpd.conffor FTPS: Openvsftpd.confand modify the SSL settings. Changessl_enable=NOtossl_enable=YES. Then, add the following lines to configure FTPS:rsa_cert_file=/etc/ssl/private/vsftpd.pem rsa_private_key_file=/etc/ssl/private/vsftpd.pem allow_anon_ssl=NO force_local_data_ssl=YES force_local_logins_ssl=YES ssl_tlsv1=YES ssl_sslv2=NO ssl_sslv3=NO require_ssl_reuse=NO ssl_ciphers=HIGH pasv_min_port=40000 pasv_max_port=50000 -
Restart vsftpd Service: Restart the service to enable FTPS:
sudo systemctl restart vsftpd.service
Now your FTP server will use FTPS, encrypting the data transmission for enhanced security. Clients connecting to your server will need to support FTPS for secure communication.
Conclusion
By following this guide, you have successfully installed, configured, and secured an FTP server on Ubuntu using vsftpd. This setup enables efficient file sharing and management across networks. Remember to regularly review and adjust your vsftpd configurations to maintain optimal security and performance.
To further explore related topics, consider learning about SFTP vs. SSH for secure file transfer options or delve deeper into the Linux ftp command for advanced FTP usage.
