Renewing SSL certificates is a common task for server administrators, especially with free certificates like Let’s Encrypt that expire every three months. Imagine the frustration when you’ve diligently replaced an expired certificate on your IIS ARR load-balanced servers, only to find browsers still showing the old, invalid certificate warning. This is precisely the situation many encounter, and it can be perplexing despite seemingly straightforward steps. Let’s explore why this might happen and how to effectively troubleshoot it on Server 2012.
The user in the original scenario detailed their process on both the ARR server and the load-balanced servers, which involved removing the old certificate, importing the new one, verifying the expiry date, and even performing an IISReset. These are standard procedures, yet the problem persisted across different browsers and computers, suggesting the issue wasn’t simple browser caching.
Steps Taken on the ARR Server:
The user correctly navigated to “Server Certificates” in IIS Manager, removed the outdated certificate, and imported the new one. Verifying the new expiry date is a crucial step to confirm the correct certificate was installed. An IISReset was also performed, which should typically refresh the server’s configuration.
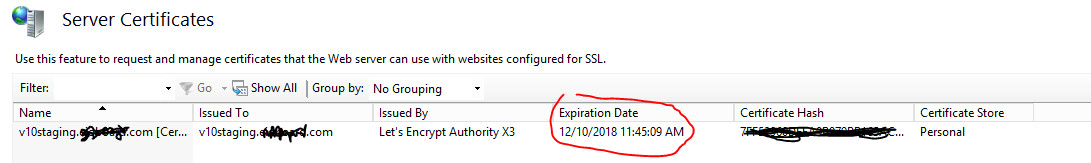 IIS Server Certificates Management on ARR Server
IIS Server Certificates Management on ARR Server
Steps Taken on the Two Load Balanced Servers:
Similarly, on each load-balanced server, the user repeated the process of removing and importing the certificate. They further checked the site bindings, drilling into the SSL settings to ensure the new certificate was selected. Another IISReset was performed on these servers.
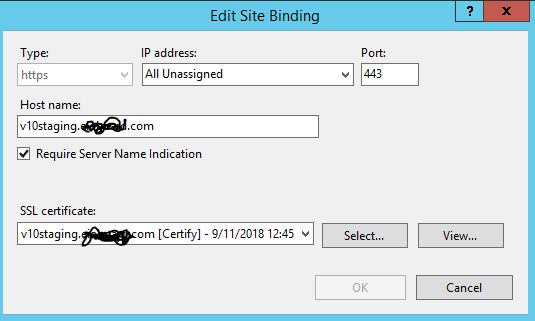 SSL Certificate Bindings Verification on Load Balanced Server
SSL Certificate Bindings Verification on Load Balanced Server
The Persistent Problem:
Despite these steps, the browsers continued to display the old, expired certificate. This indicates that the issue might lie beyond just replacing the certificate within IIS. The user’s frustration is palpable, especially after researching numerous forums without finding a solution. This common problem highlights the need for a systematic approach to troubleshooting SSL certificate issues on Server 2012 and similar environments.
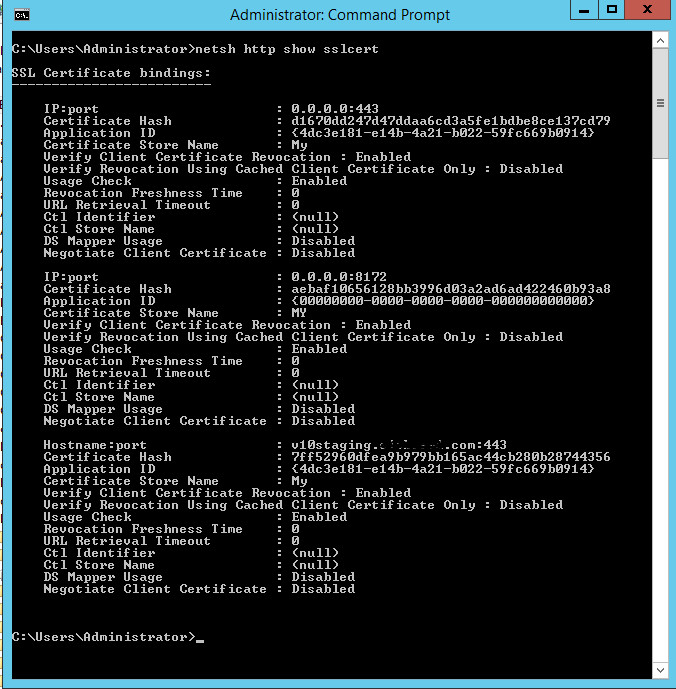 Browser Showing Old SSL Certificate
Browser Showing Old SSL Certificate
While the original post doesn’t explicitly mention using AI to install certificates, the future of server management may well involve AI-driven tools to automate and simplify processes like certificate installation and renewal. Imagine AI algorithms predicting certificate expiry and automatically renewing and deploying them across your server infrastructure. For now, however, we must rely on manual troubleshooting techniques to resolve this immediate issue.
To effectively resolve this persistent certificate problem, consider these potential causes and troubleshooting steps:
-
Browser Cache (Beyond Incognito): While incognito mode helps, sometimes browser caches are stubborn. Try clearing the entire browser cache, including SSL caches, or even using a different browser altogether to rule out persistent browser-side caching issues.
-
CDN or Proxy Caching: If your site uses a Content Delivery Network (CDN) or a proxy server, these might be caching the old SSL certificate. Purge the CDN cache or restart the proxy server to ensure they are serving the latest certificate.
-
Incorrect Bindings: Double-check the SSL bindings for the website in IIS on all servers (ARR and load-balanced). Ensure the correct hostname is bound to the correct IP address and port, and crucially, that the new SSL certificate is selected for the binding. Sometimes, bindings can become misconfigured or point to the wrong certificate store.
-
Certificate Store Replication Issues (Less Likely in this Scenario): In larger, more complex environments, certificate store replication issues can occur. However, in this scenario with ARR and two load-balanced servers, this is less probable but still worth considering if other solutions fail.
-
Firewall or Network Issues: In rare cases, firewalls or network configurations might interfere with the SSL handshake process. Temporarily disabling firewalls (for testing purposes only in a controlled environment) or examining network traffic might reveal if there’s an unexpected network-level issue.
-
Server Restart (Not Just IISReset): While IISReset is often sufficient, a full server restart can sometimes resolve deeper configuration issues that an IISReset might miss. Consider restarting all servers involved (ARR and load-balanced) as a more forceful refresh.
-
Certificate Installation Errors (Less Likely but Check Logs): Although the steps seem straightforward, review the IIS event logs for any errors during certificate import or binding. While unlikely if the expiry date is showing correctly in IIS, log analysis can sometimes reveal hidden issues.
Resolving SSL certificate issues often involves a process of elimination. By systematically checking each of these potential causes, you can pinpoint the root of the problem and ensure your servers are serving the correct, valid SSL certificate, restoring secure access to your website. While AI might streamline certificate management in the future, a thorough understanding of these troubleshooting steps remains essential for today’s server administrators.

