Logging on to a server effectively for troubleshooting involves understanding server logs and using the right tools, and rental-server.net offers comprehensive solutions for server management and access. Proper server access provides a detailed view of server activities, enabling efficient problem-solving and maintenance. Explore dedicated server solutions, cloud hosting options, and VPS hosting services for seamless server log analysis.
1. What Does “Log On Server” Mean and Why Is It Important?
Logging on to a server refers to the process of gaining access to a server’s operating system or specific applications, and this access is crucial for various administrative and maintenance tasks. Effective server access enables administrators to monitor performance, troubleshoot issues, and ensure the server runs smoothly.
Server logs provide a wealth of information about what’s happening “behind the scenes.” These logs capture a range of activities, from user access attempts to system errors, offering a detailed timeline of events. By analyzing these logs, administrators can:
- Identify Security Breaches: Detect unauthorized access attempts and potential security vulnerabilities.
- Troubleshoot Performance Issues: Pinpoint the root cause of slowdowns or crashes by examining error messages and system events.
- Monitor Resource Usage: Track CPU, memory, and disk I/O to optimize server performance.
- Audit User Activity: Monitor user actions for compliance and accountability.
According to a 2023 report by the Uptime Institute, proactive server monitoring and log analysis can reduce downtime by up to 30%.
2. What Are the Essential Steps to Log On to a Server?
The process of logging on to a server typically involves several key steps to ensure secure and authorized access. These steps often include authentication, authorization, and establishing a secure connection.
Here’s a breakdown of the essential steps:
- Obtain Credentials: Acquire the necessary username and password, SSH key, or other authentication methods.
- Choose a Method: Select the appropriate method based on the server’s configuration, such as SSH, Remote Desktop Protocol (RDP), or a web-based control panel.
- Establish Connection: Use a client tool (e.g., PuTTY, Terminal, RDP client) to initiate a connection to the server’s IP address or hostname.
- Authenticate: Enter your credentials when prompted. For SSH, you may need to provide a passphrase for your private key.
- Verify Access: Once logged in, verify that you have the necessary permissions to perform the required tasks.
For instance, logging into a Linux server often involves using SSH, while Windows servers may utilize RDP. Understanding these methods is essential for effective server management.
3. What Are the Different Methods for “Log On Server”?
There are various methods to log on to a server, each with its own advantages and use cases, and the choice depends on the server type, operating system, and security requirements. Common methods include SSH, RDP, console access, and web-based control panels.
Here’s a detailed look at each method:
- Secure Shell (SSH): A secure protocol for accessing Linux and Unix-based servers remotely. It provides encrypted communication, protecting sensitive data during transmission.
- Remote Desktop Protocol (RDP): A proprietary protocol developed by Microsoft for accessing Windows servers with a graphical user interface.
- Console Access: Direct access to the server’s physical console, typically used for initial setup or emergency troubleshooting.
- Web-Based Control Panels: User-friendly interfaces like cPanel, Plesk, or DirectAdmin, providing a web-based way to manage server settings, files, and applications.
According to a 2024 survey by Cybersecurity Ventures, SSH is used by approximately 75% of organizations for secure remote server access.
4. How Do I Choose the Right Server Logging Method?
Selecting the right server logging method is crucial for maintaining a secure and efficient server environment, and different logging methods offer varying levels of detail and accessibility. Consider factors like the server’s operating system, application requirements, and security policies.
Here’s a comparison of common server logging methods:
| Logging Method | Description | Pros | Cons | Use Cases |
|---|---|---|---|---|
| Text Files | Simple text-based logs that record events in a human-readable format. | Easy to read and understand, widely supported. | Can be difficult to search and analyze, requires manual parsing. | Basic event tracking, debugging simple applications. |
| System Logs (Syslog) | A standardized protocol for forwarding log messages from various devices to a central server. | Centralized logging, supports multiple devices, efficient for network monitoring. | Requires a dedicated syslog server, configuration can be complex. | Network monitoring, security auditing, compliance reporting. |
| Event Logs | A feature in Windows operating systems that records system events, application errors, and security alerts. | Detailed event information, integrated with Windows security features. | Limited to Windows environments, can generate a large volume of data. | Troubleshooting Windows servers, security monitoring, application debugging. |
| Database Logging | Storing log data in a database for structured querying and analysis. | Efficient querying, supports complex analysis, scalable for large environments. | Requires a database server, can be more complex to set up. | High-volume logging, complex analysis, reporting. |
| Cloud Logging | Cloud-based logging services that provide scalable and centralized log management. | Scalable, centralized, integrates with other cloud services. | Can be expensive, requires a cloud subscription. | Cloud-based applications, microservices, serverless functions. |
| Log Management Tools | Specialized software that collects, analyzes, and visualizes log data from various sources. | Automated analysis, real-time monitoring, advanced reporting. | Can be expensive, requires training to use effectively. | Large-scale environments, complex troubleshooting, security monitoring. |
According to a study by Gartner, organizations that implement centralized logging solutions experience a 20% reduction in troubleshooting time.
5. What Are Common Challenges When Trying to “Log On Server”?
Logging on to a server can present several challenges, ranging from authentication issues to network connectivity problems, and understanding these challenges is crucial for effective troubleshooting. Common issues include incorrect credentials, network outages, firewall restrictions, and account lockouts.
Here’s a closer look at these challenges:
- Incorrect Credentials: Entering the wrong username or password.
- Network Outages: Intermittent or complete loss of network connectivity.
- Firewall Restrictions: Firewalls blocking access to the server.
- Account Lockouts: Multiple failed login attempts leading to account suspension.
- Protocol Mismatches: Using the wrong protocol (e.g., attempting to SSH into a Windows server).
A 2022 report by Verizon found that 74% of breaches involved the human element, including the use of stolen credentials.
6. How Can I Troubleshoot Common “Log On Server” Issues?
Troubleshooting “Log On Server” issues requires a systematic approach to identify and resolve the underlying problems, and common techniques include verifying credentials, checking network connectivity, examining firewall settings, and reviewing server logs.
Here’s a step-by-step guide:
- Verify Credentials: Double-check the username and password for typos. Reset the password if necessary.
- Check Network Connectivity: Ensure the server is reachable by pinging its IP address.
- Examine Firewall Settings: Verify that the firewall allows traffic on the necessary ports (e.g., port 22 for SSH, port 3389 for RDP).
- Review Server Logs: Check the server’s authentication logs for error messages or failed login attempts.
- Test with Different Methods: Try alternative methods, such as console access or a web-based control panel.
- Contact Support: If all else fails, contact the server provider’s support team for assistance.
According to Microsoft’s support documentation, enabling verbose logging can help diagnose RDP connection issues.
7. What Tools Can Help Me Effectively “Log On Server”?
Several tools can help streamline the process of logging on to a server, enhancing security and efficiency, and these tools range from SSH clients and RDP clients to password managers and multi-factor authentication apps.
Here’s a list of helpful tools:
- PuTTY: A free SSH and Telnet client for Windows.
- MobaXterm: An enhanced terminal for Windows with built-in X server and SSH client.
- Termius: A cross-platform SSH client with a user-friendly interface.
- Microsoft Remote Desktop: The official RDP client for Windows, macOS, iOS, and Android.
- Royal TS: A connection management tool for Windows that supports RDP, SSH, VNC, and more.
- LastPass: A password manager that securely stores and autofills login credentials.
- Duo Security: A multi-factor authentication app that adds an extra layer of security to server access.
According to a survey by Spiceworks Ziff Davis, approximately 60% of IT professionals use password managers to improve security.
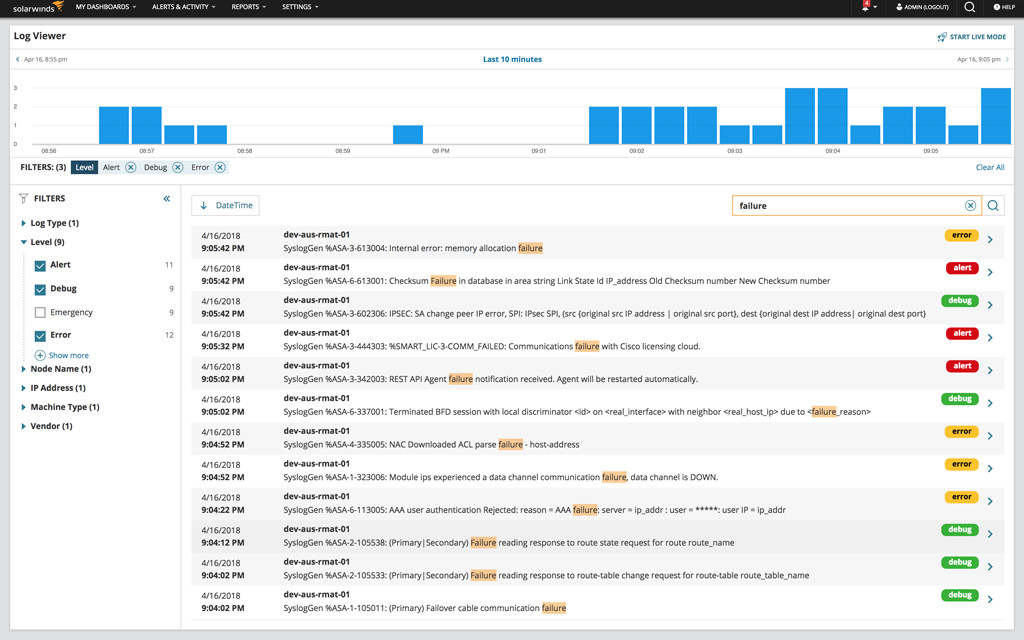 LM-real-time-log-stream
LM-real-time-log-stream
8. How Does Multi-Factor Authentication Enhance “Log On Server” Security?
Multi-factor authentication (MFA) adds an extra layer of security to the “log on server” process by requiring users to provide multiple forms of verification, and this significantly reduces the risk of unauthorized access, even if the password is compromised.
MFA typically involves combining something you know (password), something you have (security token or mobile device), and something you are (biometrics). By requiring multiple factors, MFA makes it much harder for attackers to gain access to the server.
According to a report by Google, MFA can block up to 99.9% of automated bot attacks.
9. What Are the Best Practices for Secure “Log On Server”?
Securing the “log on server” process requires implementing several best practices to protect against unauthorized access and potential security breaches, and these practices include using strong passwords, enabling MFA, restricting access privileges, and regularly auditing user activity.
Here’s a list of best practices:
- Use Strong Passwords: Create complex passwords that are difficult to guess.
- Enable MFA: Implement multi-factor authentication for all user accounts.
- Restrict Access Privileges: Grant users only the necessary permissions.
- Regularly Audit User Activity: Monitor user actions for suspicious behavior.
- Keep Software Updated: Regularly update the server’s operating system and applications to patch security vulnerabilities.
- Use SSH Keys: Use SSH keys instead of passwords for SSH access.
- Implement a Firewall: Configure a firewall to restrict access to the server.
According to the SANS Institute, implementing these best practices can significantly reduce the risk of server breaches.
10. How Can Rental-Server.Net Help Me With “Log On Server” Solutions?
Rental-server.net offers a range of services and resources to help you effectively manage and secure your server access, and our solutions include dedicated servers, VPS hosting, cloud hosting, and comprehensive support.
Here’s how rental-server.net can assist you:
- Dedicated Servers: Powerful servers with dedicated resources for demanding applications.
- VPS Hosting: Virtual private servers that offer a balance of performance and affordability.
- Cloud Hosting: Scalable cloud-based servers with pay-as-you-go pricing.
- Comprehensive Support: Expert technical support to assist you with server setup, configuration, and troubleshooting.
We provide solutions tailored to meet various needs and budgets, ensuring that you have the right tools and support to manage your server effectively. Whether you’re looking for robust dedicated server solutions, flexible cloud hosting, or reliable VPS hosting, rental-server.net has you covered. Our team is dedicated to providing top-notch service and support, so you can focus on your core business while we take care of your server infrastructure.
Ready to optimize your server access and enhance your troubleshooting capabilities? Visit rental-server.net today to explore our range of services and find the perfect solution for your needs. Our dedicated team is here to help you navigate the complexities of server management and ensure your systems are always running smoothly. Contact us at +1 (703) 435-2000 or visit our office at 21710 Ashbrook Place, Suite 100, Ashburn, VA 20147, United States.
FAQ Section
1. What is the first thing I should check if I can’t log on to my server?
The first thing to check is your login credentials (username and password) to ensure they are entered correctly.
2. What is SSH and why is it used for logging onto servers?
SSH (Secure Shell) is a cryptographic network protocol for securely accessing a server, encrypting the connection to protect sensitive data.
3. How does a firewall affect my ability to log on to a server?
A firewall can block connection attempts if it is not configured to allow traffic on the port used for logging in, such as port 22 for SSH or 3389 for RDP.
4. What is RDP and when is it used?
RDP (Remote Desktop Protocol) is a proprietary protocol developed by Microsoft which provides a graphical interface to connect to another computer over a network connection, and is commonly used for accessing Windows servers.
5. What are SSH keys and how do they improve server security?
SSH keys are a more secure way to log into a server than using a password, as they use cryptographic key pairs for authentication, eliminating the risk of password-based attacks.
6. What is multi-factor authentication (MFA) and why should I use it for server access?
MFA is a security system that requires more than one method of authentication from independent categories of credentials to verify the user’s identity for a login or other transaction, greatly enhancing security.
7. How do I check the server logs to troubleshoot login issues?
Server logs can be checked via the command line or a log management tool, typically found in /var/log on Linux systems, or through the Event Viewer on Windows.
8. What steps should I take if I suspect my server has been hacked?
If you suspect your server has been hacked, immediately disconnect it from the network, change all passwords, analyze logs for suspicious activity, and consider restoring from a clean backup.
9. How can rental-server.net help with server security and access issues?
Rental-server.net provides a range of secure server solutions, expert technical support, and tools to help manage and troubleshoot server access, ensuring a safe and reliable hosting environment.
10. What are the advantages of using a VPS over a dedicated server for logging on to a server?
A VPS offers a balance of performance and affordability, making it suitable for many applications, while dedicated servers provide more resources and control but can be more expensive.
By addressing these common questions and concerns, rental-server.net aims to provide comprehensive guidance and support for effective and secure server management. Whether you’re an experienced system administrator or new to server management, our goal is to empower you with the knowledge and tools you need to succeed.